The North Korean espionage-focused actor known as Kimsuky has
been observed using three different Android malware strains to
target users located in its southern counterpart.
That’s according to findings from South Korean cybersecurity
company S2W, which named the malware families FastFire, FastViewer,
and FastSpy.
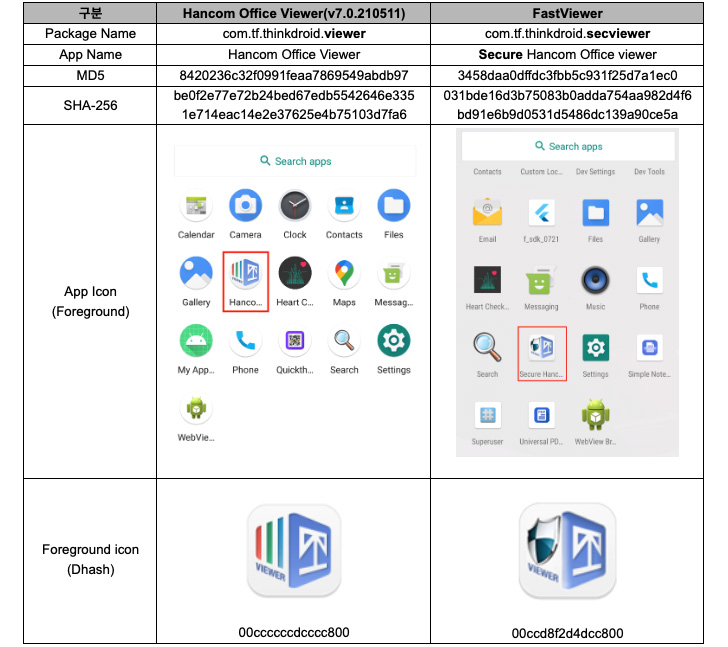
“The FastFire malware is disguised as a Google security plugin,
and the FastViewer malware disguises itself as ‘Hancom Office
Viewer,’ [while] FastSpy is a remote access tool based on AndroSpy[1],” researchers Lee Sebin
and Shin Yeongjae said[2].
Kimsuky, also known by the names Black Banshee, Thallium, and
Velvet Chollima, is believed to be tasked by the North Korean
regime with a global intelligence-gathering mission,
disproportionately targeting individuals and organizations in South
Korea, Japan, and the U.S.
This past August, Kaspersky unearthed a previously undocumented
infection chain dubbed GoldDragon[3]
to deploy a Windows backdoor capable of stealing information from
the victim such as file lists, user keystrokes, and stored web
browser login credentials.
The advanced persistent threat is also known to an Android
version of AppleSeed[4]
implant to execute arbitrary actions and exfiltrate information
from the infected devices.
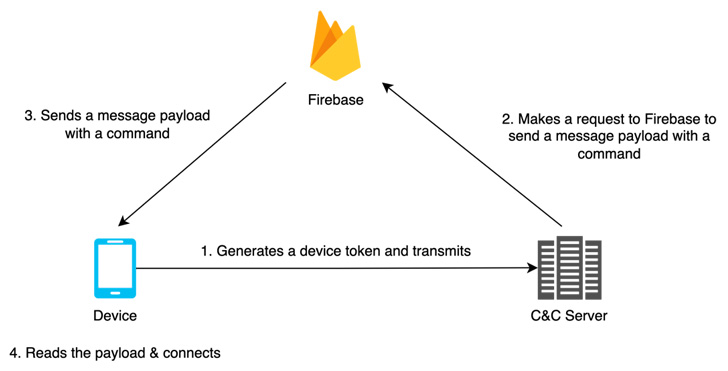
FastFire, FastViewer, and FastSpy are the latest additions to
its evolving Android malware arsenal, which are designed to receive
commands from Firebase and download additional payloads.
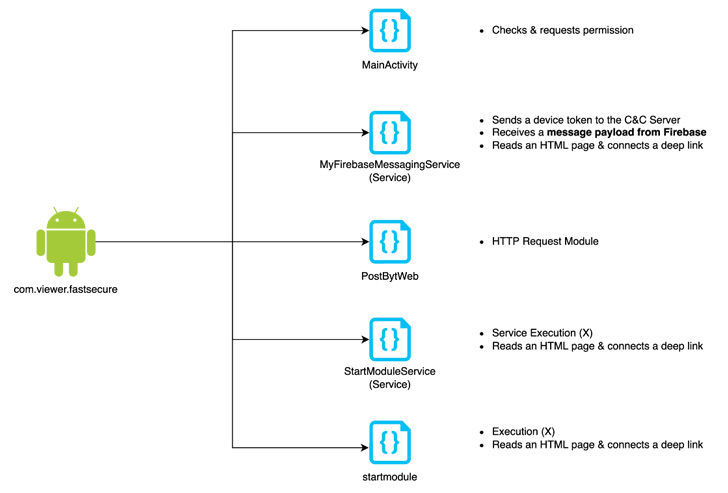
“FastViewer is a repackaged APK by adding arbitrary malicious
code inserted by an attacker to the normal Hancom Office Viewer
app,” the researchers said, adding the malware also downloads
FastSpy as a next-stage.
The rogue apps in question are below –
- com.viewer.fastsecure (Google 보안 Plugin)
- com.tf.thinkdroid.secviewer (FastViewer)
Both FastViewer and FastSpy abuse Android’s accessibility API
permissions to fulfill its spying behaviors, with the latter
automating user clicks to grant itself extensive permissions in a
manner analogous to MaliBot[5].
FastSpy, once launched, enables the adversary to seize control
of the targeted devices, intercept phone calls and SMSes, track
users’ locations, harvest documents, capture keystrokes, and record
information from the phone’s camera, microphone, and speaker.
S2W’s attribution of the malware to Kimsuky is based on overlaps
with a server domain named “mc.pzs[.]kr,” which was previously
employed in a May 2022 campaign[6]
identified as orchestrated by the group to distribute malware
disguised as North Korea related press releases.
“Kimsuky group has continuously performed attacks to steal the
target’s information targeting mobile devices,” the researchers
said. “In addition, various attempts are being made to bypass
detection by customizing Androspy, an open source RAT.”
“Since Kimsuky group’s mobile targeting strategy is getting more
advanced, it is necessary to be careful about sophisticated attacks
targeting Android devices.”
References
Read more https://thehackernews.com/2022/10/kimsuky-hackers-spotted-using-3-new.html