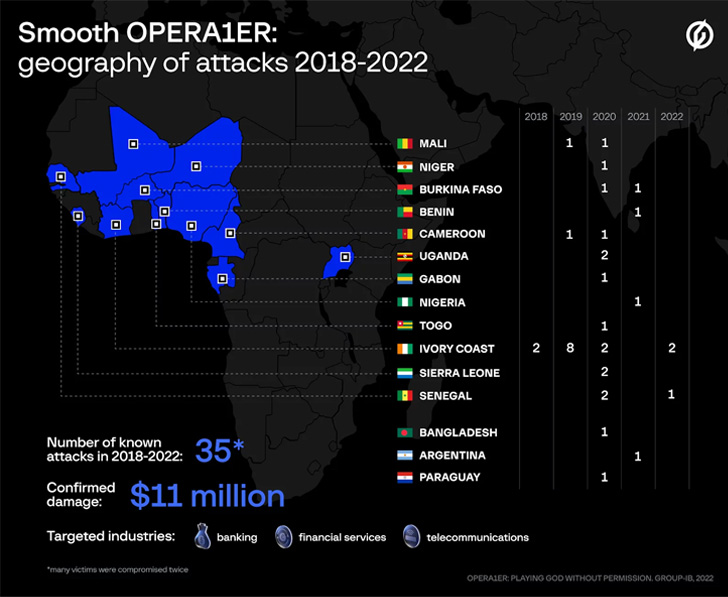
A French-speaking threat actor dubbed OPERA1ER
has been linked to a series of more than 30 successful cyber
attacks aimed at banks, financial services, and telecom companies
across Africa, Asia, and Latin America between 2018 and 2022.
According to Singapore-headquartered cybersecurity company
Group-IB, the attacks have led to thefts totaling $11 million, with
actual damages estimated to be as high as $30 million.
Some of the more recent attacks in 2021 and 2021 have singled
out five different banks in Burkina Faso, Benin, Ivory Coast, and
Senegal. Many of the victims identified are said to have been
compromised twice, and their infrastructure subsequently weaponized
to strike other organizations.
OPERA1ER, also known by the names DESKTOP-GROUP, Common Raven,
and NXSMS, is known to be active since 2016, operating with the
goal of conducting financially motivated heists and exfiltration of
documents for further use in spear-phishing attacks.
“OPERA1ER often operates during weekends and public holidays,”
Group-IB said in a report[1]
shared with The Hacker News, adding the adversary’s “entire arsenal
is based on open-source programs and trojans, or free published
RATs that can be found on the dark web.”
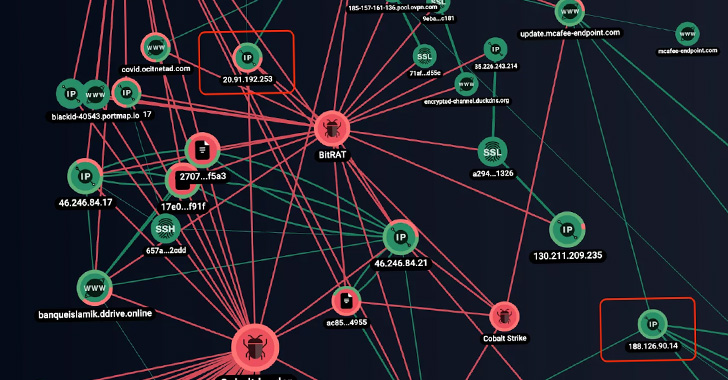
This includes off-the-shelf malware such as Nanocore, Netwire,
Agent Teslam Venom RAT, BitRAT, Metasploit, and Cobalt Strike
Beacon, among others.
The attack chain commences with “high-quality spear-phishing
emails” with invoice and delivery-themed lures written primarily in
French and to a lesser extent in English.
These messages feature ZIP archive attachments or links to
Google Drive, Discord servers, infected legitimate websites, and
other actor-controlled domains, which lead to the deployment of
remote access trojans.
Succeeding in the RAT execution, post-exploitation frameworks
like Metasploit Meterpreter and Cobalt Strike Beacon are downloaded
and launched to establish persistent access, harvest credentials,
and exfiltrate files of interest, but not before an extended
reconnaissance period to understand the back-end operations.
This is substantiated by the fact that the threat actor has been
observed spending anywhere between three to 12 months from initial
intrusion to making fraudulent transactions to withdraw money from
ATMs.
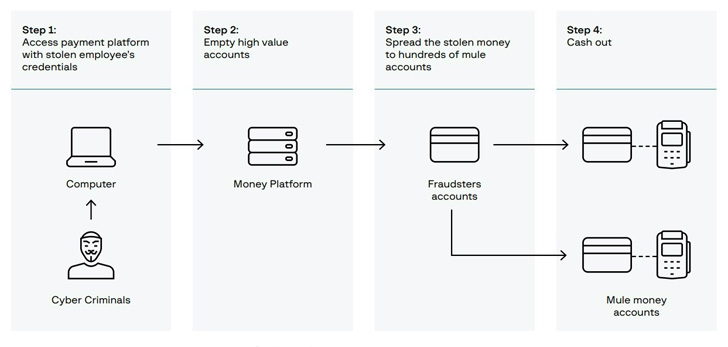
The final phase of the attack involves breaking into the
victim’s digital banking backend, enabling the adversary to move
funds from high value accounts to hundreds of rogue accounts, and
ultimately cash them out via ATMs with the help of a network of
money mules hired in advance.
“Here clearly the attack and theft of funds were possible
because the bad actors managed to accumulate different levels of
access rights to the system by stealing the login credentials of
various operator users,” Group-IB explained.
In one instance, over 400 mule subscriber accounts were employed
to illicitly siphon the money, indicating that the “attack was very
sophisticated, organized, coordinated, and planned over a long
period of time”
The findings – carried out in collaboration with telecom giant
Orange – that OPERA1ER managed to pull off the banking fraud
operation by solely relying on publicly available malware
highlights the effort that has gone into studying the internal
networks of the organizations.
“There are no zero-day threats in OPERA1ER’s arsenal, and the
attacks often use exploits for vulnerabilities discovered three
years ago,” the company noted. “By slowly and careful inching their
way through the targeted system, they were able to successfully
carry out at least 30 attacks all around the world in less than
three years.”
Read more https://thehackernews.com/2022/11/researchers-detail-opera1er-apt-attacks.html