A new analysis of tools put to use by the Black Basta ransomware
operation has identified ties between the threat actor and the
FIN7[1]
(aka Carbanak) group.
This link “could suggest either that Black Basta and FIN7
maintain a special relationship or that one or more individuals
belong to both groups,” cybersecurity firm SentinelOne said[2]
in a technical write-up shared with The Hacker News.
Black Basta, which emerged[3]
earlier this year, has been attributed to a ransomware spree that
has claimed over 90 organizations as of September 2022, suggesting
that the adversary is both well-organized and well-resourced.
One notable aspect that makes the group stand out, per
SentinelOne, is the fact that there have been no signs of its
operators attempting to recruit affiliates or advertising the
malware as a RaaS on darknet forums or crimeware marketplaces.
This has raised the possibility that the Black Basta developers
either cut out affiliates from the chain and deploy the ransomware
through their own custom toolset or alternatively work with a close
set of affiliates without the need to market their warez.
Attack chains involving Black Basta are known to leverage QBot
(aka Qakbot), which, in turn, is delivered by means of phishing
emails containing macro-based Microsoft Office documents, with
newer infections taking advantage of ISO images and LNK droppers to
get around Microsoft’s decision to block macros[4] in files downloaded from
the web by default.
Once Qakbot obtains a persistent foothold in the target
environment, the Black Basta operator enters the scene to conduct
reconnaissance by connecting to the victim through the backdoor,
followed by exploiting known vulnerabilities (e.g., ZeroLogon[5], PrintNightmare[6], and NoPac[7]) to escalate
privileges.
Also put to use at this stage are backdoors such as SystemBC[8]
(aka Coroxy) for data exfiltration and the download of additional
malicious modules, before the conducting lateral movement and
taking steps to impair defenses by disabling installed security
solutions.
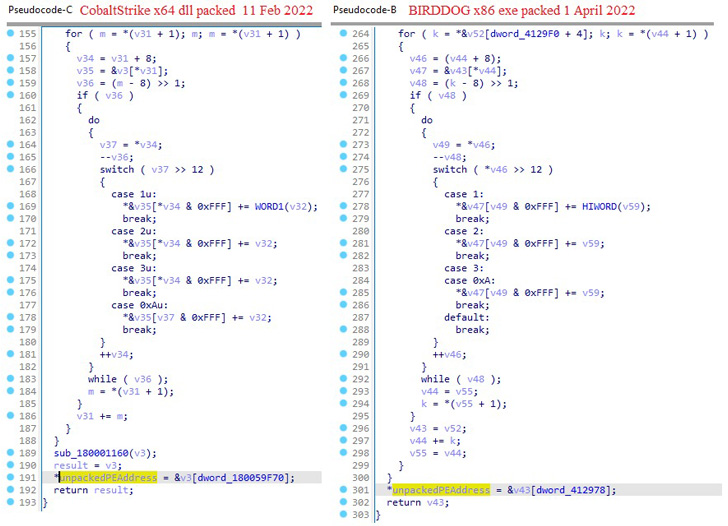
This also includes a custom EDR evasion tool that’s been
exclusively put to use in Black Basta incidents and comes embedded
with a backdoor dubbed BIRDDOG, also called as SocksBot[9]
and which has been utilized in several attacks previously
attributed to the FIN7 group.
The FIN7 cybercrime syndicate[10], active since 2012, has
a track record of mounting large-scale malware campaigns targeting
the point-of-sale (PoS) systems aimed at the restaurant, gambling,
and hospitality industries for financial fraud.
Over the past two years, however, the group has switched to
ransomware for illicitly generating revenues, first as Darkside[11] and then as BlackMatter[12] and BlackCat[13], not to mention
establishing fake front
companies[14] to recruit unwitting
penetration testers to stage ransomware attacks.
“At this point, it’s likely that FIN7 or an affiliate began
writing tools from scratch in order to disassociate their new
operations from the old,” researchers Antonio Cocomazzi and Antonio
Pirozzi said. “It is likely that the developer(s) behind their
tools to impair victim defenses is, or was, a developer for
FIN7.”
The findings come weeks after the Black Basta actor was observed[15] using the Qakbot trojan
to deploy Cobalt Strike and Brute Ratel C4 frameworks as a
second-stage payload in recent attacks.
“The crimeware ecosystem is constantly expanding, changing, and
evolving,” the researchers concluded. “FIN7 (or Carbanak) is often
credited with innovating in the criminal space, taking attacks
against banks and PoS systems to new heights beyond the schemes of
their peers.”
The disclosure also arrives as the U.S. Financial Crimes
Enforcement Network (FinCEN) reported[16] a surge in ransomware
attacks targeting domestic entities from 487 in 2020 to 1,489 in
2021, incurring a total cost of $1.2 billion, a 188% jump from $416
million the previous year.
References
- ^
FIN7
(thehackernews.com) - ^
said
(www.sentinelone.com) - ^
emerged
(thehackernews.com) - ^
decision
to block macros (thehackernews.com) - ^
ZeroLogon
(thehackernews.com) - ^
PrintNightmare
(thehackernews.com) - ^
NoPac
(thehackernews.com) - ^
SystemBC
(thehackernews.com) - ^
SocksBot
(malpedia.caad.fkie.fraunhofer.de) - ^
FIN7
cybercrime syndicate (thehackernews.com) - ^
Darkside
(thehackernews.com) - ^
BlackMatter
(thehackernews.com) - ^
BlackCat
(thehackernews.com) - ^
establishing fake front companies
(thehackernews.com) - ^
observed
(thehackernews.com) - ^
reported
(www.fincen.gov)
Read more https://thehackernews.com/2022/11/researchers-find-links-bw-black-basta.html