Threat actors have been discovered distributing a new credential
stealer written in AutoHotkey (AHK) scripting language as part of
an ongoing campaign that started early 2020.
Customers of financial institutions in the US and Canada are
among the primary targets for credential exfiltration, with a
specific focus on banks such as Scotiabank, Royal Bank of Canada,
HSBC, Alterna Bank, Capital One, Manulife, and EQ Bank. Also
included in the list is an Indian banking firm ICICI Bank.
AutoHotkey[1]
is an open-source custom scripting language for Microsoft Windows
aimed at providing easy hotkeys for macro-creation and software
automation that allows users to automate repetitive tasks in any
Windows application.
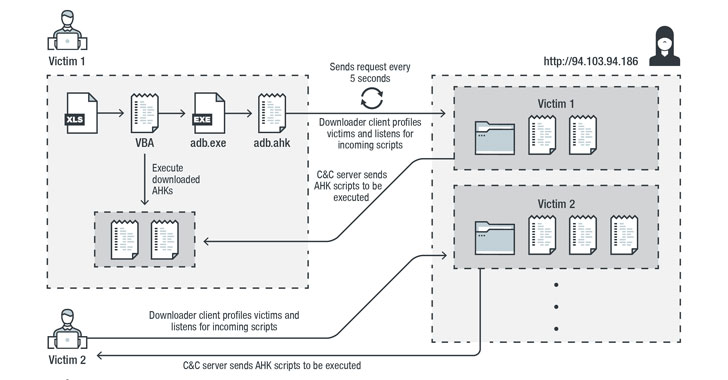
The multi-stage infection chain commences with a malware-laced
Excel file that’s embedded with a Visual Basic for Applications
(VBA) AutoOpen[2]
macro, which is subsequently used to drop and execute the
downloader client script (“adb.ahk”) via a legitimate portable AHK
script compiler executable (“adb.exe”).
The downloader client script is also responsible for achieving
persistence, profiling victims, and downloading and running
additional AHK scripts from command-and-control (C&C) servers
located in the US, the Netherlands, and Sweden.
What makes this malware different is that instead of receiving
commands directly from the C&C server, it downloads and
executes AHK scripts to accomplish different tasks.
“By doing this, the attacker can decide to upload a specific
script to achieve customized tasks for each user or group of
users,” Trend Micro researchers said[3]
in an analysis. “This also prevents the main components from being
revealed publicly, specifically to other researchers or to
sandboxes.”
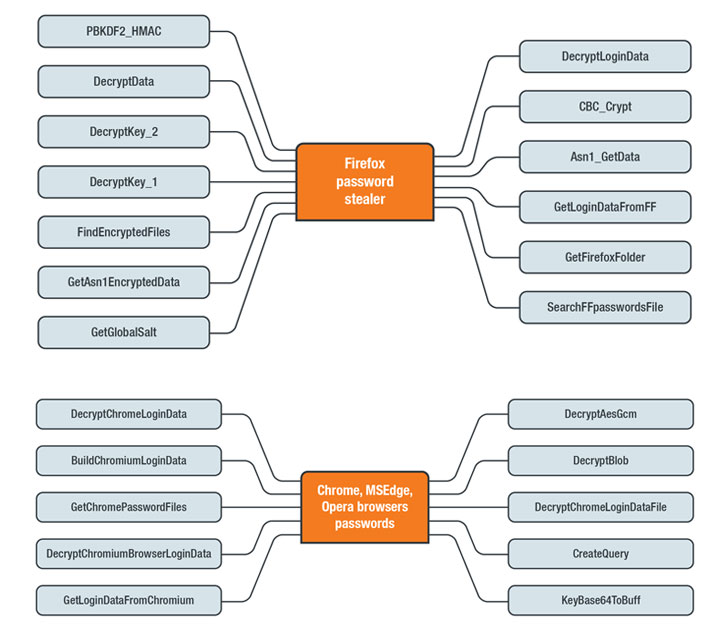
Chief among them is a credential stealer that targets various
browsers such as Google Chrome, Opera, Microsoft Edge, and more.
Once installed, the stealer also attempts to download an SQLite
module (“sqlite3.dll”) on the infected machine, using it to perform
SQL queries against the SQLite databases within browsers’ app
folders.
In the final step, the stealer collects and decrypts credentials
from browsers and exfiltrates the information to the C&C server
in plaintext via an HTTP POST request.
Noting that the malware components are “well organized at the
code level,” the researchers suggest the inclusion of usage
instructions (written in Russian) could imply a “hack-for-hire”
group that’s behind the attack chain’s creation and is offering it
to others as a service.
“By using a scripting language that lacks a built-in compiler
within a victim’s operating system, loading malicious components to
achieve various tasks separately, and changing the C&C server
frequently, the attacker has been able to hide their intention from
sandboxes,” the researchers concluded.
References
Read more http://feedproxy.google.com/~r/TheHackersNews/~3/euJWmSKh42k/autohotkey-based-password-stealer.html