An effective cybersecurity strategy can be challenging to
implement correctly and often involves many layers of security.
Part of a robust security strategy involves performing what is
known as a penetration test (pen test). The penetration test helps
to discover vulnerabilities and weaknesses in your security
defenses before the bad guys discover these. They can also help
validate remedial efforts and solutions put in place to overcome
previously discovered security vulnerabilities.
Let’s look more closely at the pen test. What is included in a
penetration test? How are they performed, and by whom? What steps
should be taken after a penetration test?
What is a penetration test?
1 — Simulated cyberattack
A penetration test is, for all practical purposes, a simulated
cyberattack on your business. However, it is carried out by the
“good guys.” An outside resource often conducts a penetration test,
whether a third-party security consulting company or another
security entity. Security consultants generally have the security
expertise and are staying current with tactics and techniques used
by today’s threat actors.
2 — Arranged beforehand
Penetration tests are arranged with a security consultant days
or weeks in advance. Before the penetration test takes place, there
is usually an engagement call to understand the scope of the
penetration test. Pen tests can be general or can be focused on a
specific area or technology for more thorough testing. When
arranging for a pen test, a scoping call will help establish the
details of the penetration testing and the scope of vulnerabilities
being tested.
3 — Establish guidelines to prevent disrupting
business-critical activities
There is always a chance when stressing production
infrastructure to cause issues with business-critical production
activities. So, while it is good with a pen test to test against
your production infrastructure to ensure all potential
cybersecurity vulnerabilities are found, it is also good to
establish boundaries. For example, there may need to be “blackout”
periods where no disruptive pen testing or intrusive activities
occur.
4 — Establish cybersecurity goals for the pen test
There are various reasons for performing a pen test. These can
range from compliance requirements, overall bolstering of
cybersecurity defenses, establishing a security baseline,
validating security changes or new cybersecurity implementations,
and many others.
The company carrying out the pen test will generally gather
information needed for the pen test. This information may include
network names, resources, pertinent user accounts, and other
information required to simulate routine day-to-day workflows.
These are used to validate the security measures, potential
escalation of privileges, weak cybersecurity controls, and other
discovery tasks.
5 — Stages of the pen test
The stages of a pen test can include but are not limited to the
following:
- Scope of work, reconnaissance – The goals and
scope of the pen test are established, and initial reconnaissance
is carried out - Automated pen testing – Automated scanners and
other tools may first be used to find open ports, vulnerabilities,
and other weaknesses - Manual pen testing – Subject matter experts
may manually perform certain attacks against known technologies and
systems. - The exploitation of vulnerabilities – If a
vulnerability is found, the scope of the vulnerability will be
assessed. How far-reaching is the vulnerability? What is
criticality? - Analysis and report – Pen testers will usually
deliver an analysis of the pen test results, ranking the
criticality of any vulnerabilities found. Once these are analyzed,
a report is usually a part of the deliverables from the pen
test.
Top-rated penetration testing firms
According to Cybersecurity Ventures[1], the following companies
provide top-rated penetration testing services:
Look for reputable pen test companies with a solid track record
that aligns with your business.
Steps to take after a penetration test
1 — Consider and review the pen test results
Usually, one of the deliverables with a pen test is a detailed
report of any findings in the environment. These reports provide
businesses with the necessary information to move forward with any
remediations necessary to close major or critical security gaps. It
also helps businesses with bolstering their overall cybersecurity
posture.
In addition, as many compliance regulations require proof of
penetration testing, the delivery of the pen test report provides
the documentation needed for compliance audits if requested.
The pen test results ultimately provide organizations with the
information needed to help ensure any chinks in their cybersecurity
armor are resolved with the appropriate measures and cybersecurity
solutions if required. In addition, if it is the first pen test
performed for the organization, it helps establish the security
baseline that is a starting point for improvement. Each subsequent
pen test can then gauge the progress of improving overall
security.
2 — Remediate findings from the pen test
Pen test results usually are prioritized based on the
criticality or likelihood the discovered vulnerability will be
exploited. However, it is also wise for businesses to examine the
potential repercussions of a successful exploit on the business. In
other words, how major would it be for the company if a particular
vulnerability is exploited? What systems would be impacted? How
will business continuity be affected?
Businesses can use the prioritization of any security findings
in the pen test report to prioritize the remediation of the
vulnerabilities. However, the number and criticality of pen test
findings may affect the time needed to remediate the findings.
3 — Repeat the process
Cybersecurity is constantly changing. New threats and risks
appear on the scene each day. As a result, bolstering cybersecurity
defenses and posture is never-ending. Pen tests are part of the
overall process needed to continue checking for vulnerabilities in
the environment. Scheduling regular pen tests of the environment
allow gaining visibility to new exploits or new findings that may
not have existed when the last pen test was performed.
With each pen test, the process continues to repeat. Businesses
prioritize the findings, learn from these, and remediate the issues
based on the criticality and importance assigned. Performing pen
tests regularly helps to ensure cybersecurity is not an
afterthought, but rather it is a regular part of the overall risk
assessment process.
Credentials and pen tests
Pen test companies often ask for valid credentials to access
your environment. It may include credentialed resources. Why? It
helps shed light on any potential for access to data they shouldn’t
have or other risks. Second, attackers often attack environments
using legitimate credentials.
In fact, according to the IBM Cost of a Data
Breach Report 2021[2]:
Compromised credentials were the most common initial attack
vector, responsible for 20% of breaches.
They also take the longest to identify and contain:
Breaches caused by stolen/compromised credentials took the
longest number of days to identify (250) and contain (91) on
average, for an average total of 341 days.
Today, businesses must have strong password policies to help
protect against weak or overused passwords and actively protect
their environment from breached passwords. How can this be done
effectively?
Specops Password Policy[3]
provides strong Active Directory password policies, allowing
organizations to extend the Active Directory password policy
capabilities far beyond what is included by default. In addition,
with Specops Breached Password Protection,
organizations receive continuous protection from breached
passwords, helping businesses to protect against end-users using
passwords found on breach password lists.
Specops Breached Password Protection also protects against newly
discovered passwords using brute force or password spraying.
Specops integrates newly discovered breached passwords into the
Breached Password Protection module using its network of honeypots
worldwide that capture breached password telemetry data. The data
collected is used to bolster the Breached Password protection
provided in Specops Password Policy.
Breached Password Protection Express list can:
- Prevent users from changing to a leaked password
- Continuously check for leaked passwords and force users to
change them - Notify users if passwords become breached, and they need to
change their password
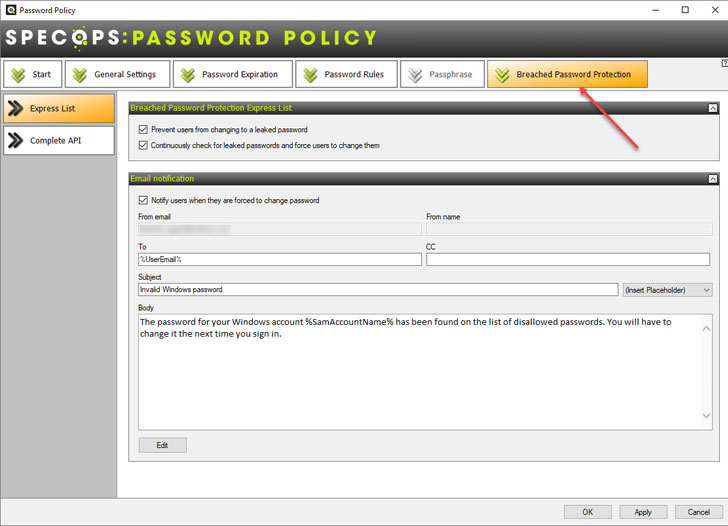 |
| Specops Breached Password Protection |
In addition to the Express List, the Specops Complete API
solution provides additional capabilities.
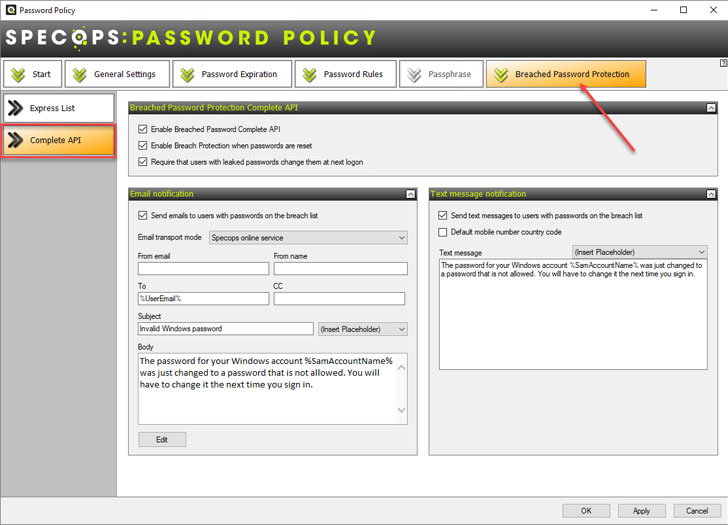 |
| Specops Breached Password Protection Complete API |
As pen tests often show, credentialed access can have more
privileges than needed or access to data they shouldn’t have. On
top of ensuring the least privileged access for users,
organizations must protect passwords in the environment with strong
password policies and breached password protection. Learn more about Specops Password Policy
tools[4] and see how you can
bolster Active Directory password protection in your
environment.
References
- ^
Cybersecurity Ventures
(cybersecurityventures.com) - ^
IBM Cost
of a Data Breach Report 2021 (www.ibm.com) - ^
Specops
Password Policy (specopssoft.com) - ^
Learn
more about Specops Password Policy tools
(specopssoft.com)
