prey on internet users.
Even the disastrous spread of SARS-COV-II (the virus), which
causes COVID-19 (the disease), is becoming an opportunity for them
to likewise spread malware or launch cyber attacks.
Reason Cybersecurity recently released a threat analysis
report[1] detailing a new attack
that takes advantage of internet users’ increased craving for
information about the novel coronavirus that is wreaking havoc
worldwide.
The attack specifically targets those who are looking for
cartographic presentations of the spread of COVID-19.
New Threat With An Old Malware Component
The latest threat discovered and analyzed by Shai Alfasi, a
cybersecurity researcher at Reason Labs, is designed to steal
information from unwitting victims.
It involves a malware identified as AZORult, an
information-stealing malicious software discovered in 2016. AZORult
malware collects information stored in web browsers, particularly
cookies, browsing histories, user IDs, passwords, and even
cryptocurrency keys.
With these data drawn from browsers, it is possible for
cybercriminals to steal credit card numbers, login credentials, and
various other sensitive information.
AZORult is reportedly discussed in Russian underground forums as
a tool for gathering sensitive data from computers. It comes with a
variant that is capable of generating a hidden administrator
account in infected computers to enable connections via the remote
desktop protocol (RDP).
Sample Analysis
Alfasi provides technical details upon studying the
malware, which is embedded in the file, usually named as
Corona-virus-Map.com.exe. It’s a small Win32 EXE file with a
payload size of only around 3.26 MB.
Double-clicking the file opens a window that shows various
information about the spread of COVID-19. The centerpiece is a “map
of infections” similar to the one from ArcGIS_Online.
Numbers of confirmed cases in different countries are presented
on the left side while stats on deaths and recoveries are on the
right. The window appears to be interactive, with tabs for various
other related information and links to sources.
It presents a convincing GUI not many would suspect to be
harmful. The information presented is not an amalgamation of random
data. It is actual COVID-19 information pooled from the web.
The malicious software utilizes some layers of packing along
with a multi-sub-process technique infused to make it challenging
for researchers to detect and analyze. Additionally, it employs a
task scheduler so it can continue operating.
Signs of Infection
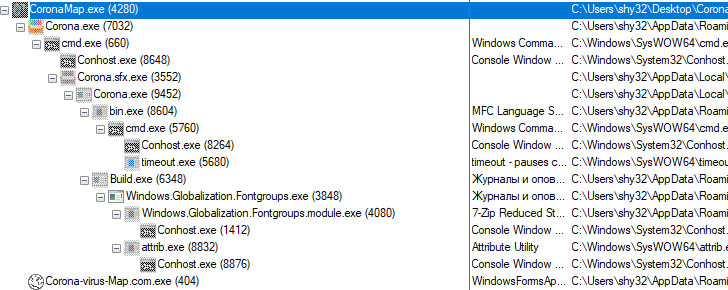
Executing the Corona-virus-Map.com.exe results in the creation of
duplicates of the Corona-virus-Map.com.exe file and multiple
Corona.exe, Bin.exe, Build.exe, and
Windows.Globalization.Fontgroups.exe files.
ZoneMap and LanguageList. Several mutexes are also created.
Execution of the malware activates the following processes:
Bin.exe, Windows.Globalization.Fontgroups.exe, and
Corona-virus-Map.com.exe. These attempt to connect to several
URLs.
These processes and URLs are only a sample of what the attack
entails. There are many other files generated and processes
initiated. They create various network communication activities as
malware tries to gather different kinds of information.
How the Attack Steals Information
Alfasi presented a detailed account of how he dissected the malware
in a blog post on the Reason Security blog. One highlight detail is
his analysis of the Bin.exe process with Ollydbg. Accordingly, the
process wrote some dynamic link libraries (DLL). The DLL “nss3.dll”
caught his attention as it is something he was acquainted with from
different actors.
These APIs appeared to facilitate the decryption of saved passwords
as well as the generation of output data.
This is a common approach used by data thieves. Relatively
simple, it only captures the login data from the infected web
browser and moves it to the C:\Windows\Temp folder. It’s one of the
hallmarks of an AZORult attack, wherein the malware extracts data,
generates a unique ID of the infected computer, applies XOR
encryption, then initiates C2 communication.
The malware makes specific calls in an attempt to steal login
data from common online accounts such as Telegram and Steam.
To emphasize, malware execution is the only step needed for it
to proceed with its information-stealing processes. Victims don’t
need to interact with the window or input sensitive information
therein.
Cleaning and Prevention
It may sound promotional, but Alfasi suggests Reason Antivirus
software as the solution to fix infected devices and prevent
further attacks. He is affiliated with Reason Security, after all.
Reason is the first to find and scrutinize this new threat, so they
can handle it effectively.
Other security firms are likely to have already learned about
this threat, since Reason made it public on March 9. Their
antiviruses or malware protection tools will have been updated as
of publication time.
As such, they may be similarly capable of detecting and
preventing the new threat.
The key to removing and stopping the opportunistic “coronavirus
map” malware is to have the right malware protection system. It
will be challenging to detect it manually, let alone remove the
infection without the right software tool.
It may not be enough to be cautious in downloading and running
files from the internet, as many tend to be overeager in accessing
information about the novel coronavirus nowadays.
The pandemic level dispersion of COVID-19 merits utmost caution
not only offline (to avoid contracting the disease) but also
online. Cyber attackers are exploiting the popularity of
coronavirus-related resources on the web, and many will likely fall
prey to the attacks.
References
- ^
threat analysis report
(blog.reasonsecurity.com) - ^
studying the malware
(www.virustotal.com)
Read more http://feedproxy.google.com/~r/TheHackersNews/~3/eV1tKt-2FJY/coronavirus-maps-covid-19.html