Trojanized installers of the Telegram messaging application are
being used to distribute the Windows-based Purple Fox backdoor on
compromised systems.
That’s according to new research published by Minerva Labs,
describing the attack as different from intrusions that typically
take advantage of legitimate software for dropping malicious
payloads.
“This threat actor was able to leave most parts of the attack
under the radar by separating the attack into several small files,
most of which had very low detection rates by [antivirus] engines,
with the final stage leading to Purple Fox rootkit infection,”
researcher Natalie Zargarov said[1].
First discovered in 2018, Purple Fox comes with rootkit
capabilities that allow the malware to be planted beyond the reach
of security solutions and evade detection. A March 2021 report from
Guardicore detailed[2]
its worm-like propagation feature, enabling the backdoor to spread
more rapidly.
Then in October 2021, Trend Micro researchers uncovered[3]
a .NET implant dubbed FoxSocket deployed in conjunction with Purple
Fox that takes advantage of WebSockets[4]
to contact its command-and-control (C2) servers for a more secure
means of establishing communications.
“The rootkit capabilities of Purple Fox make it more capable of
carrying out its objectives in a stealthier manner,” the
researchers noted. “They allow Purple Fox to persist on affected
systems as well as deliver further payloads to affected
systems.”
Last but not least, in December 2021, Trend Micro also shed light[5]
on the later stages of the Purple Fox infection chain, targeting
SQL databases by inserting a malicious SQL common language runtime
(CLR[6]) module to achieve a
persistent and stealthier execution and ultimately abuse the SQL
servers for illicit cryptocurrency mining.
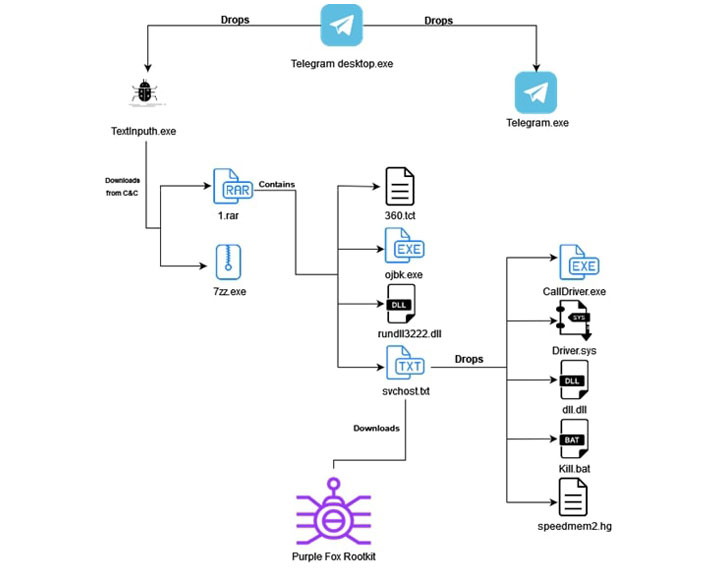
The new attack chain observed by Minerva commences with a
Telegram installer file, an AutoIt script that drops a legitimate
installer for the chat app and a malicious downloader called
“TextInputh.exe,” the latter of which is executed to retrieve
next-stage malware from the C2 server.
Subsequently, the downloaded files proceed to block processes
associated with different antivirus engines, before advancing to
the final stage that results in the download and execution of the
Purple Fox rootkit from a now-shut down remote server.
“We found a large number of malicious installers delivering the
same Purple Fox rootkit version using the same attack chain,”
Zargarov said. “It seems like some were delivered via email, while
others we assume were downloaded from phishing websites. The beauty
of this attack is that every stage is separated to a different file
which are useless without the entire file set.”
References
Read more https://thehackernews.com/2022/01/beware-of-fake-telegram-messenger-app.html