Sam is working as a system administrator in an organization . He captured the principle characteristics of a vulnerability and produced a numerical score to …
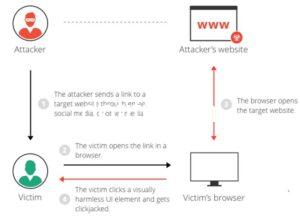
Scenaro : 1. Victim opens the attacker’s web site.
Scenaro : 1. Victim opens the attacker’s web site. 2. Attacker sets up a web site which contain interesting and attractive content like ‘Do you …