A financially-motivated malware campaign has compromised over
800 WordPress websites to deliver a banking trojan dubbed
Chaes targeting Brazilian customers of Banco do Brasil, Loja
Integrada, Mercado Bitcoin, Mercado Livre, and Mercado Pago.
First documented by Cybereason[1]
in November 2020, the info-stealing malware is delivered via a
sophisticated infection chain that’s engineered to harvest
sensitive consumer information, including login credentials, credit
card numbers, and other financial information.
“Chaes is characterized by the multiple-stage delivery that
utilizes scripting frameworks such as JScript, Python, and NodeJS,
binaries written in Delphi, and malicious Google Chrome
extensions,” Avast researchers Anh Ho and Igor Morgenstern said[2]. “The ultimate goal of
Chaes is to steal credentials stored in Chrome and intercept logins
of popular banking websites in Brazil.”
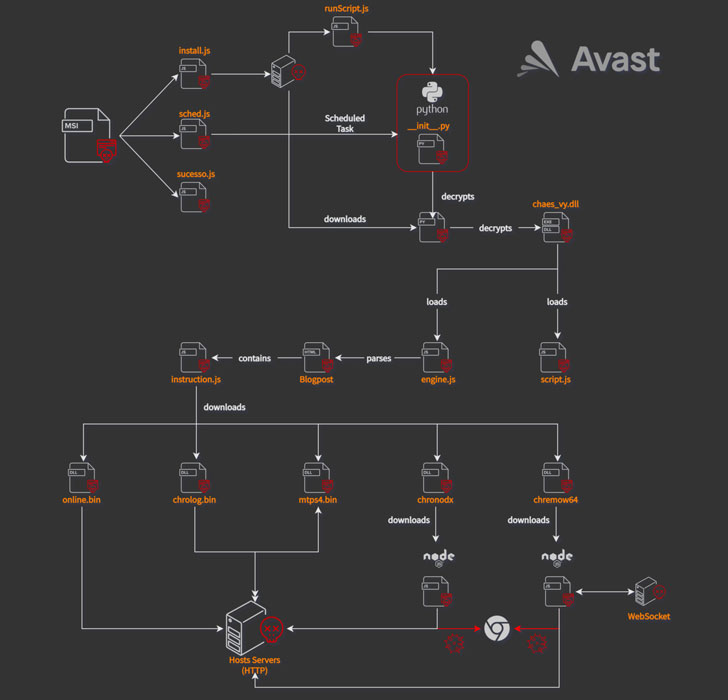
The attack sequence is triggered when users visit one of the
infected websites, upon which a pop-up is displayed, urging them to
install a fake Java Runtime application. Should the user follow
through the instructions, the rogue installer initiates a complex
malware delivery routine that culminates in the deployment of
several modules.
Some of the intermediary payloads are not only encrypted but
also hidden as commented-out code inside the HTML page of a Blogger
blogspot domain (“awsvirtual[.]blogspot.com”). In the final stage,
a JavaScript dropper downloads and installs as many as five Chrome
extensions —
- Online – A Delphi module used to fingerprint
the victim and transmit the system information to a
command-and-control (C2) server - Mtps4 (MultiTela Pascal) – A Delphi-based
backdoor whose main purpose is to connect to the C2 server and wait
for a responding Pascal Script[3]
to execute - Chrolog (ChromeLog) – A Google Chrome password
stealer written in Delphi - Chronodx (Chrome Noder) – A JavaScript trojan
that, upon detecting the launch of Chrome browser by the victim,
closes it immediately and reopens its own instance of Chrome
containing a malicious module that steals banking information - Chremows (Chrome WebSocket) – A JavaScript
banking trojan that records keypresses and mouse clicks on Chrome
with the goal of plundering login credentials from users of Mercado
Livre and Mercado Pago
Stating that the attacks are ongoing, Avast said that it had
shared its findings with the Brazilian CERT to disrupt the
malware’s spread. That said, Chaes-related artifacts continue to
remain on some of the infected websites.
“Chaes exploits many websites containing CMS WordPress to serve
malicious installers,” the researchers concluded. “The Google
Chrome extensions are able to steal users’ credentials stored in
Chrome and collect users’ banking information from popular banking
websites.”
References
- ^
Cybereason
(www.cybereason.com) - ^
said
(decoded.avast.io) - ^
Pascal
Script (en.wikipedia.org)
Read more https://thehackernews.com/2022/01/chaes-banking-trojan-hijacks-chrome.html