At least two research institutes located in Russia and a third
likely target in Belarus have been at the receiving end of an
espionage attack by a Chinese nation-state advanced persistent
threat (APT).
The attacks, codenamed “Twisted Panda,” come in
the backdrop of Russia’s military invasion of Ukraine, prompting a
wide range[1]
of threat actors[2]
to swiftly adapt their campaigns on the ongoing conflict to
distribute malware and stage opportunistic attacks.
They have materialized in the form of social engineering schemes
with topical war and sanctions-themed baits orchestrated to trick
potential victims into clicking malicious links or opening
weaponized documents.
Israeli cybersecurity firm Check Point, which disclosed[3]
details of the latest intelligence-gathering operation, attributed
it a Chinese threat actor, with connections to that of Stone Panda[4]
(aka APT 10[5], Cicada, or Potassium)
and Mustang Panda[6]
(aka Bronze President, HoneyMyte, or RedDelta).
Calling it a continuation of “a long-running espionage operation
against Russian-related entities that has been in operation since
at least June 2021,” most recent traces of the activity is said to
have been observed as recently as April 2022.
Targets included two defense research institutions belonging to
the Russian state-owned defense conglomerate Rostec Corporation and
an unknown entity situated in the Belarusian city of Minsk.
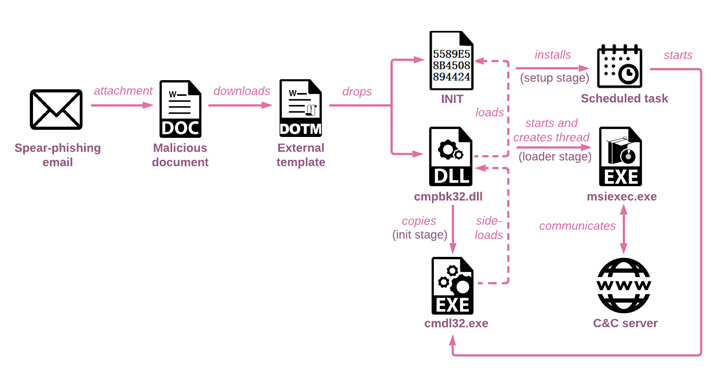
The phishing attacks commenced with emails that contain a link
masquerading as the Health Ministry of Russia, but in reality is an
attacker-controlled domain, as well as a decoy Microsoft Word
document designed to trigger the infection and drop a loader.
The 32-bit DLL (“cmpbk32.dll”), besides establishing persistence
by means of a scheduled task, is also responsible for executing a
second-stage multi-layered loader, which is subsequently unpacked
to run the final payload in memory.
The injected payload, a previously undocumented backdoor named
Spinner, makes use of sophisticated techniques such as control flow flattening[7]
to conceal the program flow, previously identified as put to use by
both Stone Panda[8]
and Mustang Panda[9]
in their attacks.
“These tools are in development since at least March 2021 and
use advanced evasion and anti-analysis techniques such as
multi-layer in-memory loaders and compiler-level obfuscations,”
Check Point said.
Despite its complex code structure, Spinner is a barebones
implant that’s only equipped to enumerate compromised hosts and run
additional payloads retrieved from a remote server.
Check Point noted that its investigation also revealed an
earlier variant of the backdoor that’s distributed in a similar
fashion, indicating that the campaign has been active since June
2021 based on the compilation timestamps of the executables.
But in an interesting twist, while the older version doesn’t
incorporate the anti-reverse engineering methods, it makes up for
it by sporting extra features missing from Spinner, including the
ability to list and manipulate files, exfiltrate valuable data, and
run operating system commands and arbitrary downloaded
payloads.
“In less than a year, the actors significantly improved the
infection chain and made it more complex,” the researchers said.
“All the functionality from the old campaign was preserved, but it
was split between multiple components making it harder to analyze
or detect each stage.”
“The evolution of the tools and techniques throughout this time
period indicates that the actors behind the campaign are persistent
in achieving their goals in a stealthy manner.”
References
- ^
wide
range (thehackernews.com) - ^
threat
actors (thehackernews.com) - ^
disclosed
(research.checkpoint.com) - ^
Stone
Panda (thehackernews.com) - ^
APT
10 (thehackernews.com) - ^
Mustang
Panda (thehackernews.com) - ^
control
flow flattening (news.sophos.com) - ^
Stone
Panda (www.virusbulletin.com) - ^
Mustang
Panda (thehackernews.com)
Read more https://thehackernews.com/2022/05/chinese-twisted-panda-hackers-caught.html