Cisco on Friday rolled out fixes for a medium-severity
vulnerability affecting IOS XR Software that it said has been
exploited in real-world attacks.
Tracked as CVE-2022-20821 (CVSS score: 6.5), the issue relates
to an open port vulnerability that could be abused by an
unauthenticated, remote attacker to connect to a Redis instance and
achieve code execution.
“A successful exploit could allow the attacker to write to the
Redis in-memory database, write arbitrary files to the container
filesystem, and retrieve information about the Redis database,”
Cisco said[1]
in an advisory.
“Given the configuration of the sandboxed container that the
Redis instance runs in, a remote attacker would be unable to
execute remote code or abuse the integrity of the Cisco IOS XR
Software host system.”
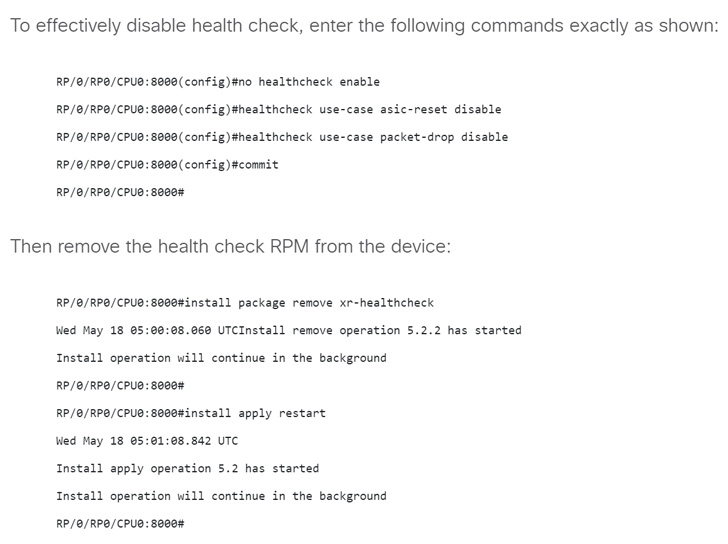
The flaw, which it said was identified during the resolution of
a technical assistance center (TAC) case, impacts Cisco 8000 Series
routers running IOS XR Software that has the health check RPM
installed and active.
The networking equipment maker also cautioned that it’s aware of
the attempted exploitation of the zero-day bug earlier this month.
“Cisco strongly recommends that customers apply suitable
workarounds or upgrade to a fixed software release to remediate
this vulnerability,” it added.
Read more https://thehackernews.com/2022/05/cisco-issues-patches-for-new-ios-xr.html