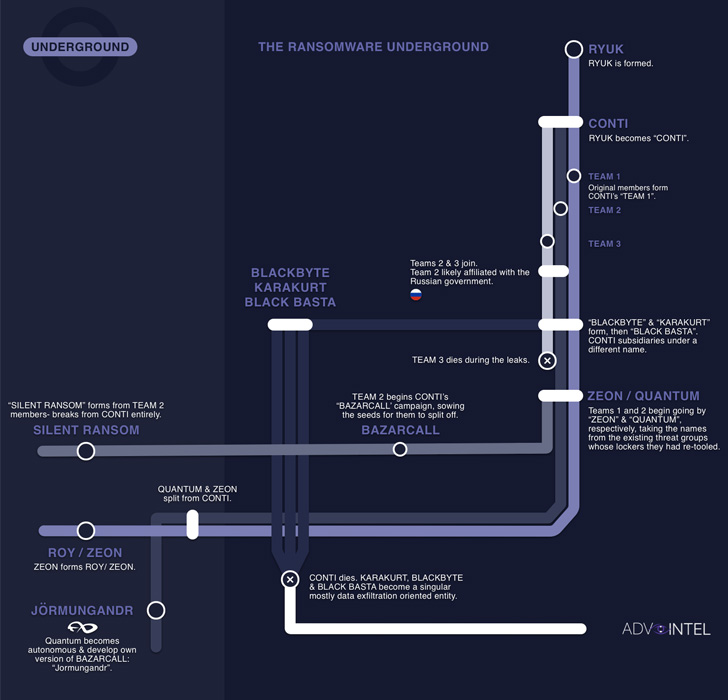
Three different offshoots of the notorious Conti cybercrime
cartel have resorted to the technique of call-back phishing as an
initial access vector to breach targeted networks.
“Three autonomous threat groups have since adopted and
independently developed their own targeted phishing tactics derived
from the call back phishing methodology,” cybersecurity firm
AdvIntel said[1]
in a Wednesday report.
These targeted campaigns “substantially increased” attacks
against entities in finance, technology, legal, and insurance
sectors, the company added.
The actors in question include Silent Ransom, Quantum, and
Roy/Zeon, all of which have split from Conti after the latter
orchestrated its shutdown[2] in May 2022 following
its public support for Russia in the ongoing Russo-Ukrainian
conflict.
The advanced social engineering tactic, also called BazaCall[3]
(aka BazarCall), came under the spotlight in 2020/2021 when it was
put to use by operators of the Ryuk ransomware, which later
rebranded to Conti.
It’s said to have received substantial operational improvements
in May, around the same time the Conti team was busy coordinating
an organization-wide restructuring while simulating the movements
of an active group.
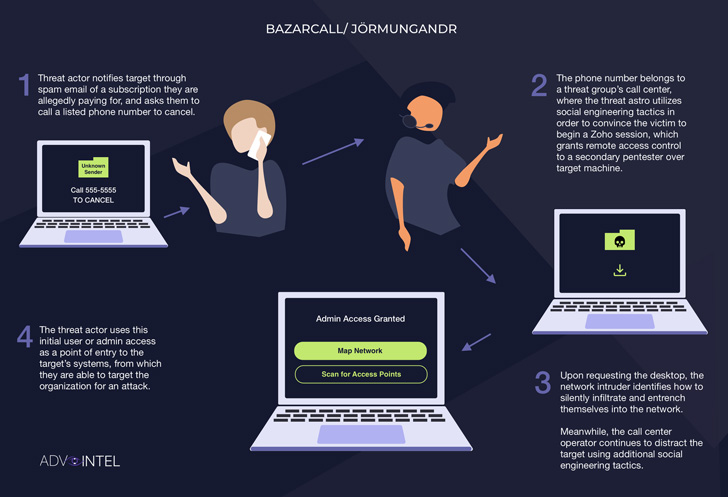
The phishing attack is also unique in that it forgoes malicious
links or attachments in email messages in favor of phone numbers
that recipients are tricked into calling by alerting them of an
upcoming charge on their credit card for a premium
subscription.
If a target recipient falls for the scheme and decides to call
the phone number indicated in the email, a real person from a
fraudulent call center set up by BazaCall’s operators attempts to
convince the victim to grant the customer service person remote
desktop control to help cancel the supposed subscription.
With access to the desktop, the threat actor stealthily takes
steps to infiltrate the user’s network as well as establish
persistence for follow-on activities such as data exfiltration.
“Call back phishing was the tactic that enabled a widespread
shift in the approach to ransomware deployment,” AdvIntel said,
adding the “attack vector is intrinsically embedded into the Conti
organizational tradition.”
Silent Ransom, the first Conti subgroup to move away from the
cybercrime gang in March 2022, has since been linked to data
extortion attacks after gaining initial access through subscription
expiry emails that claim to notify users of pending payment for
Zoho Masterclass and Duolingo services.
“These attacks can be categorized as data breach ransom attacks,
in which the main focus of the group is to gain access to sensitive
documents and information, and demand payment to withhold
publication of the stolen data,” Sygnia noted[4]
last month, describing the infection procedure.
The Israeli cybersecurity company is tracking the activities of
Silent Ransom under the moniker Luna Moth.
Quantum and Roy/Zeon are the two other Conti spin-offs to follow
the same approach starting June 2022. While Quantum has been
implicated[5]
in the devastating ransomware attacks on the Costa Rican government networks[6] in May, Roy/Zeon
consists of members “responsible for the creation of Ryuk
itself.”
“As threat actors have realized the potentialities of weaponized
social engineering tactics, it is likely that these phishing
operations will only continue to become more elaborate, detailed,
and difficult to parse from legitimate communications as time goes
on,” the researchers said.
The findings come as industrial cybersecurity company Dragos
disclosed[7]
the number of ransomware attacks on industrial infrastructures
decreased from 158 in the first quarter of 2022 to 125 in the
second quarter, a drop it attributed with low confidence to Conti
closing shop.
That’s not all. Blockchain analytics firm Elliptic revealed[8]
this week that the now-defunct Conti group has laundered over $53
million in crypto assets through RenBridge, a cross-chain bridge
that allows virtual funds to be transferred between blockchains,
between April 2021 and July 2022.
References
Read more https://thehackernews.com/2022/08/conti-cybercrime-cartel-using-bazarcall.html