An analysis of leaked chats[1]
from the notorious Conti ransomware group[2]
earlier this year has revealed that the syndicate has been working
on a set of firmware attack techniques that could offer a path to
accessing privileged code on compromised devices.
“Control over firmware gives attackers virtually unmatched
powers both to directly cause damage and to enable other long-term
strategic goals,” firmware and hardware security firm Eclypsium
said[3]
in a report shared with The Hacker News.
“Such level of access would allow an adversary to cause
irreparable damage to a system or to establish ongoing persistence
that is virtually invisible to the operating system.”
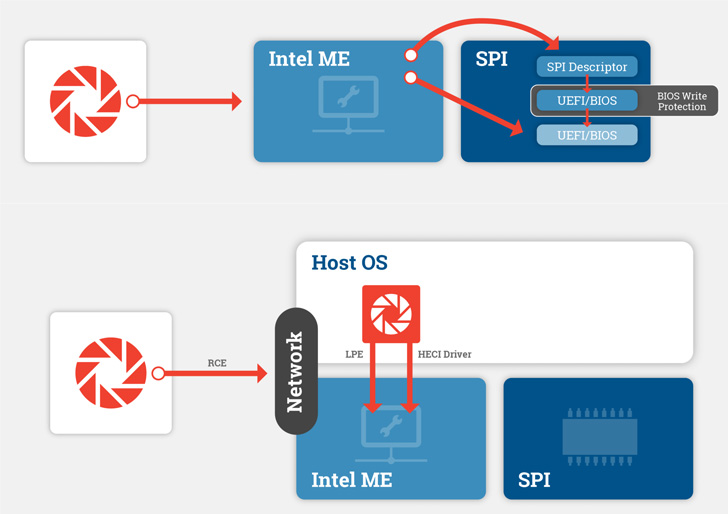
Specifically, this includes attacks aimed at embedded
microcontrollers such as the Intel Management Engine[4]
(ME), a privileged
component that’s part of the company’s processor chipsets and which
can completely bypass the operating system.
The conversations among the Conti members, which leaked after
the group pledged its support to Russia in the latter’s invasion of
Ukraine, have shed light on the syndicate’s attempts to mine for
vulnerabilities related to ME firmware and BIOS write
protection.
This entailed finding undocumented commands and vulnerabilities
in the ME interface, achieving code execution in the ME to access
and rewrite the SPI flash memory, and dropping System Management
Mode (SMM[5])-level implants, which
could be leveraged to even modify the kernel.
The research ultimately manifested in the form of a
proof-of-concept (PoC) code in June 2021 that can gain SMM code
execution by gaining control over the ME after obtaining initial
access to the host by means of traditional vectors like phishing,
malware, or a supply chain compromise, the leaked chats show.
“By shifting focus to Intel ME as well as targeting devices in
which the BIOS is write protected, attackers could easily find far
more available target devices,” the researchers said.
That’s not all. Control over the firmware could also be
exploited to gain long-term persistence, evade security solutions,
and cause irreparable system damage, enabling the threat actor to
mount destructive attacks[6]
as witnessed during the Russo-Ukrainian war.
“The Conti leaks exposed a strategic shift that moves firmware
attacks even further away from the prying eyes of traditional
security tools,” the researchers said.
“The shift to ME firmware gives attackers a far larger pool of
potential victims to attack, and a new avenue to reaching the most
privileged code and execution modes available on modern
systems.”
References
- ^
leaked
chats (thehackernews.com) - ^
Conti
ransomware group (thehackernews.com) - ^
said
(eclypsium.com) - ^
Management Engine
(www.intel.com) - ^
SMM
(thehackernews.com) - ^
destructive attacks
(thehackernews.com)
Read more https://thehackernews.com/2022/06/conti-leaks-reveal-ransomware-gangs.html