Even as the operators of Conti threatened to overthrow the Costa Rican
government[1], the notorious
cybercrime gang officially took down their infrastructure in favor
of migrating their criminal activities to other ancillary
operations, including Karakurt and BlackByte.
“From the negotiations site, chatrooms, messengers to servers
and proxy hosts – the Conti brand, not the organization itself, is
shutting down,” AdvIntel researchers Yelisey Bogusalvskiy and
Vitali Kremez said[2]
in a report. “However, this does not mean that the threat actors
themselves are retiring.”
The voluntary termination, with the exception of its
name-and-shame blog, is said to have occurred on May 19, 2022,
while an organizational rejig was happening simultaneously to
ensure a smooth transition of the ransomware group’s members.
AdvIntel said Conti, which is also tracked under the moniker
Gold Ulrick[3], orchestrated its own
demise by utilizing information warfare techniques.
The disbanding also follows the group’s public allegiance to
Russia in the country’s invasion of Ukraine, dealing a huge blow to
its operations and provoking the leak[4]
of thousands of private chat logs as well as its toolset, making it
a “toxic brand.”
The Conti team is believed to have been actively creating
subdivisions for over two months. But in tandem, the group began
taking steps to control the narrative, sending out “smoke signals”
in an attempt to simulate the movements of an active group.
“The attack on Costa Rica indeed brought Conti into the
spotlight and helped them to maintain the illusion of life for just
a bit longer, while the real restructuring was taking place,” the
researchers said.
“The only goal Conti had wanted to meet with this final attack
was to use the platform as a tool of publicity, performing their
own death and subsequent rebirth in the most plausible way it could
have been conceived.”
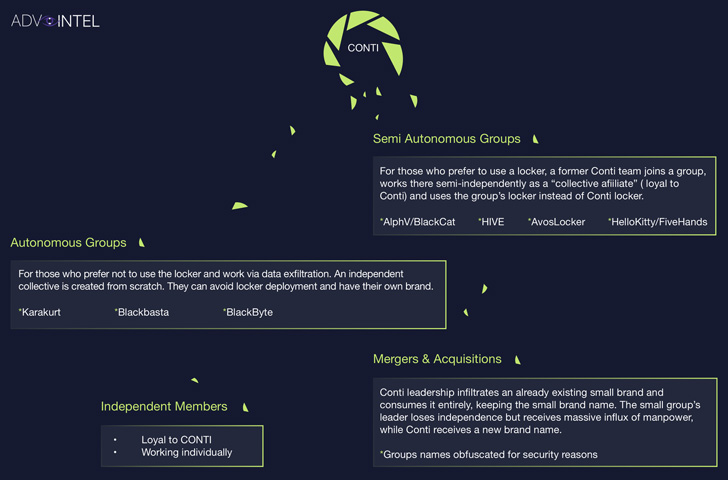
The diversion tactics aside, Conti’s infiltration specialists
are also said to have forged alliances with other well-known
ransomware groups such as BlackCat[5], AvosLocker[6], Hive[7], and HelloKitty[8]
(aka FiveHands).
Additionally, the cybersecurity firm said it had seen internal
communication alluding to the fact that Russian law enforcement
agencies had been putting pressure[9]
on Conti to halt its activities in the wake of increased scrutiny[10] and the high-profile
nature of the attacks conducted by the criminal syndicate.
Conti’s affiliation with Russia has also had other unintended
consequences, chief among them being its inability to extract
ransom payments from victims in light of severe economic sanctions
imposed by the West on the country.
That said, although the brand may cease to exist, the group has
adopted what’s called a decentralized hierarchy that involves
multiple subgroups with different motivations and business models
ranging from data theft (Karakurt[11], BlackBasta[12], and BlackByte[13]) to working as
independent affiliates.
This is not the first time Gold Ulrick has revamped its inner
workings. TrickBot[14], whose elite Overdose division[15] spawned the creation of
Ryuk and its successor Conti, has since been shut down[16] and absorbed into the
collective, turning TrickBot into a Conti subsidiary. It has also
taken over BazarLoader[17] and Emotet[18].
“The diversification of Conti’s criminal portfolio paired with
its shockingly swift dissolution does bring into question whether
their business model will be repeated among other groups,” AdvIntel
noted[19] last week.
“Ransomware Inc. is less like the gangs they are often called
and much more like cartels as time goes on,” Sam Curry, chief
security officer at Cybereason, said in a statement shared with The
Hacker News.
“This means partner agreements, specialized roles, business-like
R&D and marketing groups and so on. And because Conti is
beginning to mirror the sorts of activities we see among legitimate
companies, it’s no surprise they are changing.”
References
- ^
overthrow the Costa Rican
government (thehackernews.com) - ^
said
(www.advintel.io) - ^
Gold
Ulrick (thehackernews.com) - ^
provoking the leak
(thehackernews.com) - ^
BlackCat
(thehackernews.com) - ^
AvosLocker
(thehackernews.com) - ^
Hive
(thehackernews.com) - ^
HelloKitty
(thehackernews.com) - ^
putting
pressure (thehackernews.com) - ^
increased scrutiny
(thehackernews.com) - ^
Karakurt
(www.advintel.io) - ^
BlackBasta
(www.trendmicro.com) - ^
BlackByte
(blog.talosintelligence.com) - ^
TrickBot
(thehackernews.com) - ^
Overdose division
(www.advintel.io) - ^
shut
down (thehackernews.com) - ^
BazarLoader
(thehackernews.com) - ^
Emotet
(thehackernews.com) - ^
noted
(www.advintel.io)
Read more https://thehackernews.com/2022/05/conti-ransomware-gang-shut-down-after.html