security crisis. The movement to modern software such as cloud
technologies and microservice architectures is essential to
innovate quickly. Yet, nearly three in four developers say that
security slows down Agile and DevOps.
Neither developers nor security teams are to blame. DevOps speed
is held back by a 15-year-old, scan-based application security
(AppSec) model designed for the early 2000s. Traditional security
tools cannot keep up with today’s rapid development pace or modern
application portfolio scale.
However, sacrificing security for development speed places
critical and confidential personal and business information at
risk—from financial to healthcare data—and can disrupt operations
or even cause outages.
Code Scanners Cannot Meet Modern DevOps
Legacy AppSec approaches that rely on point-in-time scanning are
plagued by development delays and highly inaccurate results. Scans
take many hours, if not days—not ideal timelines for agile teams
that ship code multiple times a day.
Imagine a server bug on an e-commerce platform serving millions
of customers; the company will lose thousands of dollars every
second the bug remains. Teams simply cannot wait for these security
scans to complete. Moreover, once they do complete, the security
results naively, yet unintentionally, cause more harm than
good.
Inaccurate findings take the form of false positives and false
negatives. These are foundational weaknesses of code scanners
because they waste developers’ critical time on security problems
that actually do not even exist.
Code scanners cannot tell the difference between false positives
and true positives because they are “blind” to the runtime context
of applications, such as the entirety of data and control flows,
internal logic, configuration and architecture, presentation view,
libraries and frameworks, and application server.
The runtime context, which escapes code scanners, contains the
critical pieces of information required to differentiate false
positives from the vulnerabilities that are real.
Transforming AppSec with Security Instrumentation
Contrast Security transforms AppSec by offering a radically
different approach. Leveraging the same type of software
instrumentation approach used in other areas of modern software
development such as application performance monitoring (APM),
Contrast embeds security sensors in the packaged binary upon
application startup.
Data flow through the application, in conjunction with other
important runtime context, activates an intelligent
pattern-matching engine that produces accurate security
insights.
Rather than focusing on time-consuming and frustrating security
bottlenecks and interruptions to writing code, developers can focus
on creating innovative and secure applications. Contrast creates a
comprehensive AppSec platform approach that virtually eliminates
the bombardment of security alerts from false-positive
vulnerabilities.
Security instrumentation is an excellent fit for modern software
and DevOps because it is scalable. Functional tests now also serve
as security tests, replacing expensive security experts with
developer-friendly security products and development delays with
accelerated time-to-market timelines.
Democratizing Modern AppSec
Aspiring to make modern AppSec available to all developers
regardless of their ability to pay, Contrast launched Community
Edition, the only free DevOps-Native AppSec Platform designed with
developers in mind. Community Edition offers near full access to
Contrast’s products (Assess, OSS, and Protect), with developers
receiving interactive application security testing (IAST), software
composition analysis (SCA), and runtime application self-protection
(RASP) solutions—all for free.
As a starting point, Community Edition allows developers to
focus only on fixing vulnerabilities derived from custom code that
actually matter using Contrast Assess. It also offers unparalleled
visibility into and management of security risks from
vulnerabilities introduced through open-source and third-party
libraries using Contrast OSS, an open-source security or software
composition analysis (SCA) solution.
Contrast Protect, a runtime application self-protection (RASP)
solution, allows developers to extend instrumented security into
product runtime. Contrast Protect monitors and automatically blocks
attacks on applications using instrumentation from within the
application—even if the vulnerability still exists in self-written
code or open-source libraries.
Think about that. The three foundational use cases of a modern
application security program are supported in a single platform—the
Contrast DevOps-Native AppSec Platform. Developers can [1]
for a free account, access the entire platform, and secure their
application within an hour.
The main limitation with Community Edition is that developers
can only instrument and secure one Java or .NET Core application.
Also, broader programming language support and some enterprise
features such as role-based access control (RBAC) and packaged
reporting are reserved for paid users.
Developers can hit the ground running with Contrast Community
Edition, integrating AppSec directly into the modern DevOps tools
they already use. Using the flexibility and extensibility of the
Contrast DevOps-Native AppSec Platform, developers can deploy
Community Edition onto one of several Platform-as-a-Service (PaaS)
clouds of choice.
They can be the first to know about newly discovered
vulnerabilities through chat tools, add security gates to
continuous integration/continuous deployment (CI/CD) pipelines,
track remediation through ticketing systems.
Most importantly, developers can learn about remediation options
in integrated development environments (IDEs) and code editors.
Meet the Contrast Portal
The following screenshots depict core capabilities in Community
Edition and intend to help developers gain greater familiarity with
the product and its introductory user interfaces.
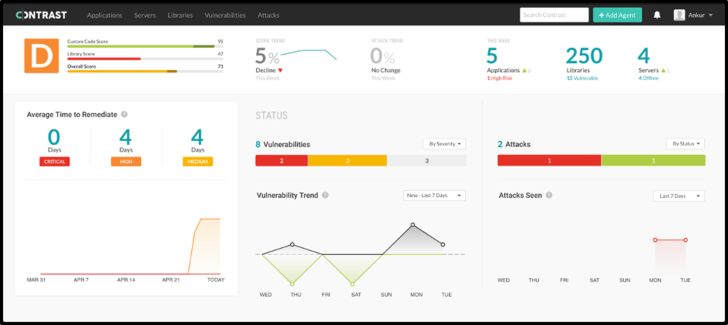
posture of a user’s entire application portfolio. Developers
receive a single letter grade that indicates the general health of
their portfolio as well as security scores for custom code and
library usage. They also can learn about remediation metrics,
vulnerability status breakdowns, and attack history.
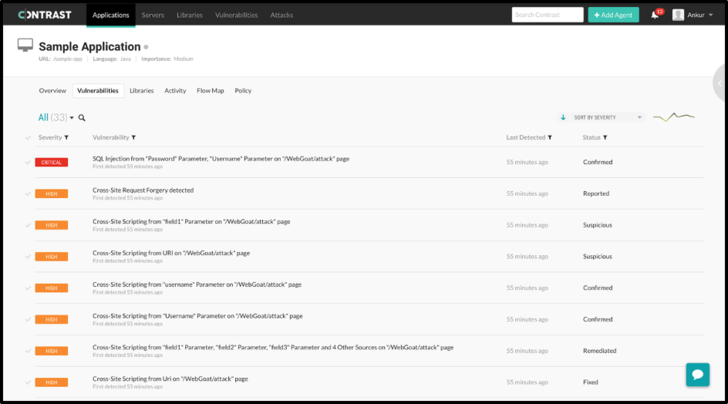
application’s security posture by viewing a list of the
vulnerabilities found in custom-source code during application
runtime. Filterable by severity and status, the list gives quick
descriptions of the vulnerability types found along with the first
and last detected timestamps.
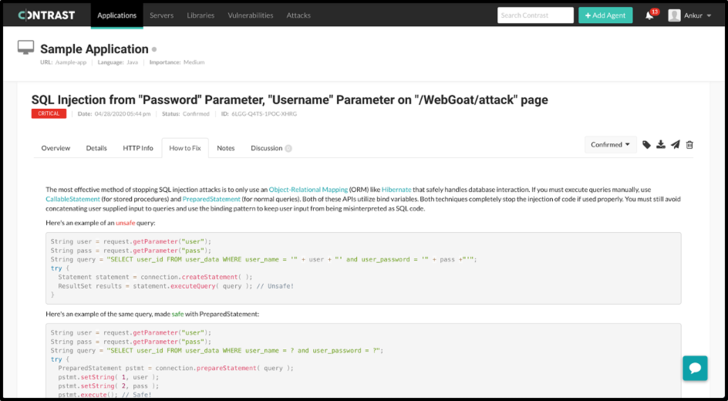
detailed information about any vulnerabilities found in
custom-source code during application runtime. Learn about what
exactly was found, understand the security risk, track the data
flow, or even replay the HTTP request. Most importantly, obtain
clear and actionable remediation guidance.
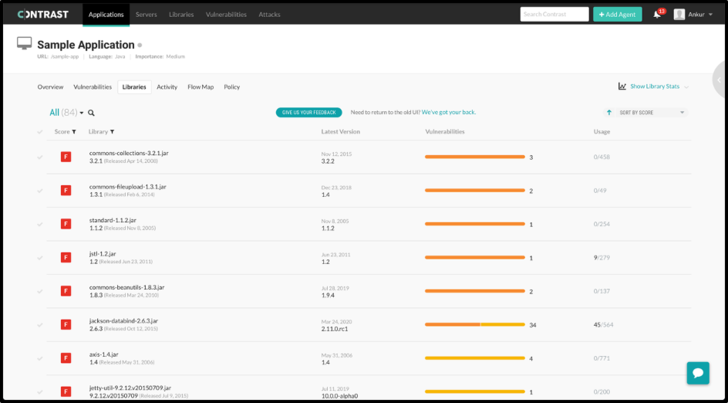
application’s security posture by viewing a list of all open-source and
third-party libraries used by the application. Filterable by
severity and status, the list gives letter grades indicating the
safety of that library while communicating the number of library
classes instantiated and the latest library version to which the
developer needs to upgrade to reduce security risk.
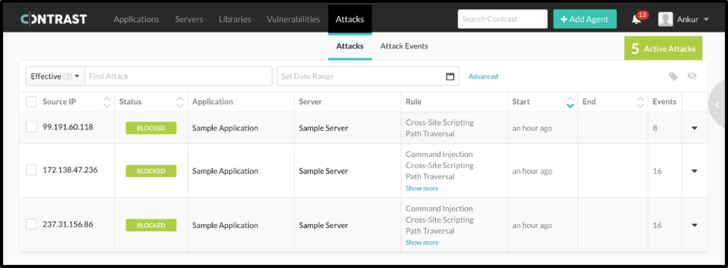
application while learning about the attacker’s IP address, the
vulnerability exploited, and attack timelines. Use Contrast Protect
to automatically block and prevent these attacks, both known and
unknown (zero-day), from succeeding either at the perimeter of the
application or just before the malicious action is taken from
within the application.
Get the Power of Innovative, Accurate AppSec
Traditional application security tools such as code scanners cannot
keep up with today’s rapid pace of application development, which
is the cornerstone of innovating quickly.
Contrast Community Edition democratizes AppSec, enabling DevOps
to accelerate to the speed of the business through security
instrumentation. Developers can gain first-hand experience by
signing up for Community Edition today. Get a [3] today and start to
write secure code faster.
References
- ^
(bit.ly)
- ^
open-source and third-party
libraries (www.contrastsecurity.com) - ^
(bit.ly)
Read more http://feedproxy.google.com/~r/TheHackersNews/~3/hFSzwevgFlk/devops-appsec-cybersecurity.html