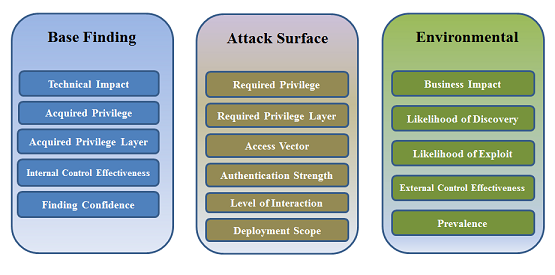
Common Weakness Scoring System (CWSS) is organized into three metric groups: Base Finding, Attack Surface, and Environmental. Each group contains multiple metrics – also known as factors – that are used to compute a CWSS score for a weakness.
CVSS (Common Vulnerability Scoring System) and CWSS (Common Weakness Scoring System) are both frameworks used to assess the severity of security vulnerabilities. However, they serve different purposes and have different scoring methodologies.
CVSS is used to score individual vulnerabilities based on their characteristics, such as the type of vulnerability, the exploitability of the vulnerability, and the impact of the vulnerability. The CVSS score ranges from 0 to 10, with higher scores indicating more severe vulnerabilities.
CWSS is used to score software weaknesses, which are patterns of coding errors that can lead to vulnerabilities. The CWSS score ranges from 0 to 100, with higher scores indicating more severe weaknesses.
CVSS is a reactive framework, meaning that it is used to score vulnerabilities that have already been discovered. CWSS is a proactive framework, meaning that it is used to identify and prioritize weaknesses in software before they are exploited.
Here is a table summarizing the key differences between CVSS and CWSS:
| Feature | CVSS | CWSS |
|---|---|---|
| Purpose | Score individual vulnerabilities | Score software weaknesses |
| Scoring range | 0 to 10 | 0 to 100 |
| Approach | Reactive | Proactive |
When to use CVSS
- Use CVSS to assess the severity of vulnerabilities that have already been discovered.
- Use CVSS to prioritize remediation efforts.
- Use CVSS to communicate the severity of vulnerabilities to stakeholders.
When to use CWSS
- Use CWSS to identify and prioritize weaknesses in software before they are exploited.
- Use CWSS to inform coding practices and improve software security.
- Use CWSS to track the effectiveness of security training and awareness programs.
Both CVSS and CWSS are valuable tools for improving software security. By using both frameworks, organizations can take a more comprehensive approach to vulnerability management and risk mitigation.
Making Sense of Vulnerabilities and Software Weaknesses with CVE, CWE, CVSS, and CWSS
In the infosec world, abbreviations and acronyms abound. But what do they all mean? In this blog post, we’ll go over the differences between some commonly confused acronyms – namely, CVE, CWE, CVSS, and CWSS.
It’s easy to see where the confusion comes in, especially because these terms are all somewhat related. They’re all terms that relate to system vulnerabilities and software weaknesses – and if you keep tabs on patch management, you’ve probably seen them.
CVE and CWE are both acronyms that are used by MITRE, a government-funded organization that creates standards for the infosec industry. But there are some key differences between them.
What is the difference between CVE and CWE?
Simply put, CVE is a list of known security vulnerabilities maintained by the National Vulnerability Database (NVD) while CWE is a list of common software weaknesses.
CWE provides an in-depth look at the underlying causes of security vulnerabilities and helps organizations create prevention efforts to reduce their risk of attack.
- CVE stands for Common Vulnerabilities and Exposures. When you see CVE, it refers to a specific instance of a vulnerability within a product or system. For example, Microsoft Outlook Elevation of Privilege Vulnerability is CVE-2023-23397.
- CWE stands for Common Weakness Enumeration. CWE refers to the types of software weaknesses, rather than specific instances of vulnerabilities within products or systems.
In other words, CVE is a list of known instances of vulnerability for specific products or systems, while CWE acts as a dictionary (so to speak) of software vulnerability types.
The National Vulnerability Database (NVD) actually uses CWEs to score CVEs. According to NVD:
So, you can see CVE and CWE are related – but are quite different.
What is the difference between CVSS and CWSS?
CVSS (Common Vulnerability Scoring System) is a standard method used by security professionals to measure and score the severity of a vulnerability. At the same time, CWSS (Common Weakness Scoring System) is a scoring system used to identify and prioritize software weaknesses most likely to be exploited by attackers.
CVSS and CWSS are two more related, but different terms.
- CVSS stands for Common Vulnerability Scoring System. As you might have guessed, CVSS is used to score the severity of a vulnerability numerically. The value is then used to help form a qualitative measurement (such as “moderate” or “critical”). For a deeper dive into CVSS scoring, check out this blog from our friends at Vulcan about CVSS v4.0.
- CWSS stands for Common Weakness Scoring System, which ranks the severity of software weaknesses.
CVSS and CWSS are two distinctly different things but can be used together when assessing a security threat.
Uncovering the Difference Between CVE, CWE, CVSS and CWSS
CVE and CWE are two different types of security tools used for different purposes, while CVSS and CWSS are used to measure and score the severity of a vulnerability. Understanding the differences between these four security tools helps organizations manage their risk and create more secure code. Additionally, they should use both CVSS and CWSS to understand the risks posed by their vulnerabilities.
Using CVE, CWE, CVSS, and CWSS together can create a robust system to detect, identify, assess, and prioritize security vulnerabilities. These tools allow organizations to identify common software weaknesses, measure the severity of a vulnerability, and create prevention efforts tailored to their needs. By taking advantage of these tools, organizations can be sure they’re secure and compliant with industry regulations.
In addition to using CVE, CWE, CVSS, and CWSS, organizations should practice secure development and coding practices to help prevent weaknesses in their software. Education and training for developers are essential for creating secure code, as well as regularly testing for vulnerabilities and patching any issues that arise.
Additionally, regular security scans of the organization’s entire IT infrastructure can ensure that any newly discovered vulnerabilities are quickly identified and addressed. By employing these best practices, organizations can stay ahead of attackers and prevent their systems from being breached.
Understanding CVE, CWE, CVSS, and CWSS, securing development practices, and scanning for vulnerabilities is the best way for organizations to stay secure. That way, they can make sure systems are protected and data is safe.
CVE, CWE, CVSS, and CWSS for vulnerability management gives organizations the tools they need to identify security vulnerabilities, measure the severity of a vulnerability, prioritize fixes, and create prevention efforts. By taking the time to understand and use these tools, organizations can ensure that their systems are secure and compliant – giving them peace of mind in a world where security is paramount.
CVE clarity matters
Vulnerabilities and software weaknesses are issues that should be rectified as soon as possible. For tech professionals, just keeping track of all the acronyms can be hard enough. However, automated patch management solutions can help organizations identify and address threats that require immediate attention, and much more.
To learn more about specific types of vulnerabilities, check out the following blogs:
Reducing Your Risk of Breach with CVE, CWE, CVSS and CWSS
No security strategy is perfect, and organizations need to stay aware of the latest threats and update their strategies accordingly. However, regular reviews of existing procedures and policies can help keep organizations up-to-date on the latest vulnerabilities and ensure that their security measures are comprehensive and effective.
By taking a proactive approach to vulnerability management, organizations can reduce their attack surface and protect themselves from attackers.
Base Finding
Attack Surface
Environmental