A financially motivated cybercrime group has been linked to an
ongoing wave of attacks aimed at hospitality, hotel, and travel
organizations in Latin America with the goal of installing malware
on compromised systems.
Enterprise security firm Proofpoint, which is tracking the group
under the name TA558 dating all the way back to April 2018, called
it a “small crime threat actor.”
“Since 2018, this group has used consistent tactics, techniques,
and procedures to attempt to install a variety of malware including
Loda RAT, Vjw0rm, and Revenge RAT,” the company’s threat research
team said[1]
in a new report.
The group has been operational at a higher tempo in 2022 than
usual, with intrusions mainly geared towards Portuguese and Spanish
speakers in Latin America, and to a lesser extent in Western Europe
and North America.
Phishing campaigns mounted by the group involve sending
malicious spam messages with reservation-themed lures such as hotel
bookings that contain weaponized documents or URLs in a bid to
entice unwitting users into installing trojans capable of
reconnaissance, data theft, and distribution of follow-on
payloads.
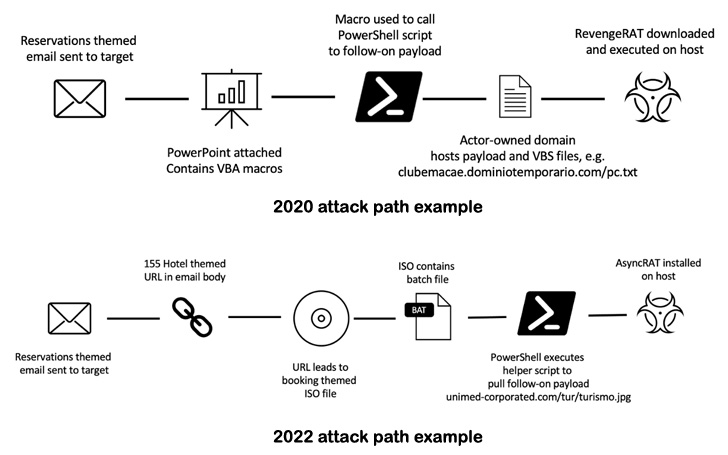
The attacks have subtly evolved over the years: The ones spotted
between 2018 and 2021 leveraged emails with Word documents that
either contained VBA macros or exploits for flaws such as CVE-2017-11882[2]
and CVE-2017-8570[3]
to download and install a mixture of malware such as AsyncRAT, Loda
RAT, Revenge RAT, and Vjw0rm.
In recent months, however, TA558 has been observed pivoting away
from macro-laden Microsoft Office attachments in favor of URLs and
ISO files to achieve initial infection, a move likely in response
to Microsoft’s decision to block
macros[4] in files downloaded from
the web by default.
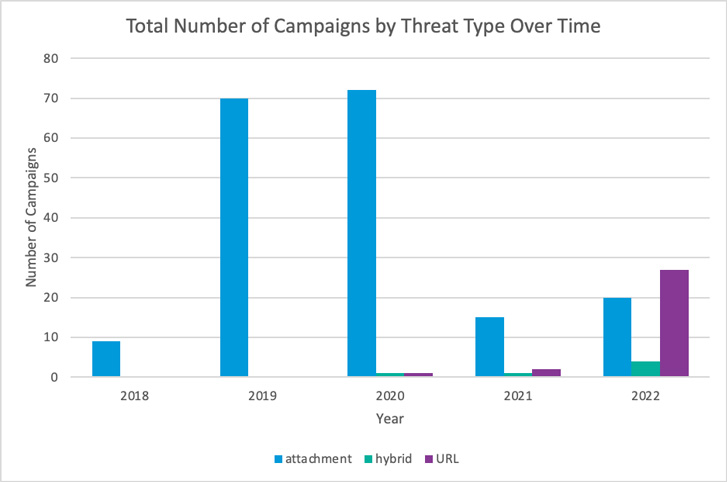
Of the 51 campaigns carried out by the group so far this year,
27 of them are said to have incorporated URLs pointing to ISO files
and ZIP archives, in comparison to just five campaigns altogether
from 2018 through 2021.
Proofpoint further noted that the intrusions chronicled under
TA558 are part of a broader[5]
set[6]
of malicious[7]
activities[8]
focusing on victims[9]
in the Latin American region. But in the absence of any
post-compromise activity, it’s suspected that TA558 is a
financially motivated cybercriminal actor.
“The malware used by TA558 can steal data including hotel
customer user and credit card data, allow lateral movement, and
deliver follow-on payloads,” the researchers said. “Activity
conducted by this actor could lead to data theft of both corporate
and customer data, as well as potential financial losses.”
References
- ^
said
(www.proofpoint.com) - ^
CVE-2017-11882
(msrc.microsoft.com) - ^
CVE-2017-8570
(msrc.microsoft.com) - ^
Microsoft’s decision to block
macros (thehackernews.com) - ^
broader
(unit42.paloaltonetworks.com) - ^
set
(blog.talosintelligence.com) - ^
malicious
(blog.talosintelligence.com) - ^
activities
(www.uptycs.com) - ^
victims
(thehackernews.com)
Read more https://thehackernews.com/2022/08/cybercrime-group-ta558-targeting.html