In a sign that malicious actors continue to find ways to work
around Google Play Store security protections, researchers have
spotted a previously undocumented Android dropper trojan that’s
currently in development.
“This new malware tries to abuse devices using a novel
technique, not seen before in Android malware, to spread the
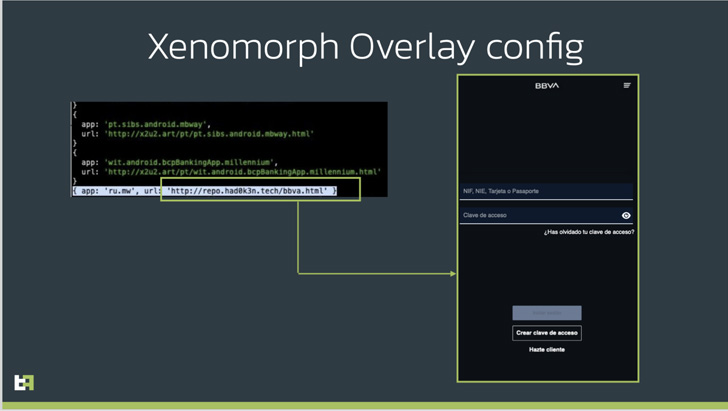
extremely dangerous Xenomorph[1]
banking trojan, allowing criminals to perform On-Device Fraud on
victim’s devices,” ThreatFabric’s Han Sahin said in a statement
shared with The Hacker News.
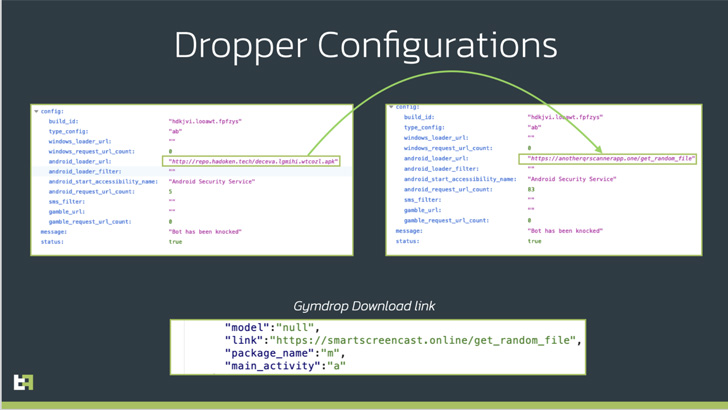
Dubbed BugDrop[2]
by the Dutch security firm, the dropper app[3]
is explicitly designed to defeat new features introduced in the
upcoming version of Android that aim to make it difficult for
malware to request Accessibility Services privileges from
victims.
ThreatFabric attributed the dropper to a cybercriminal group
known as “Hadoken Security,” which is also behind the creation and
distribution of the Xenomorph and Gymdrop[4]
Android malware families.
Banking trojans[5]
are typically deployed on Android devices through innocuous dropper
apps that pose as productivity and utility apps, which, once
installed, trick users into granting invasive permissions.
Notably, the Accessibility API, which lets apps read the
contents of the screen and perform actions on behalf of the user,
has come under heavy abuse[6], enabling malware
operators to capture sensitive data such as credentials and
financial information.
This is achieved by means of what’s called overlay attacks
wherein the trojan injects a fake lookalike login form retrieved
from a remote server when a desired app such as a cryptocurrency
wallet is opened by the victim.
Given that most of these malicious apps are sideloaded[7]
– something that’s only possible if the user has allowed
installation from unknown sources – Google, with Android 13, has
taken the step of blocking accessibility API access[8] to apps installed from
outside of an app store.
But that hasn’t stopped adversaries from attempting to
circumvent this restricted security setting. Enter BugDrop, which
masquerades as a QR code reader app and is being tested by its
authors to deploy malicious payloads via a session-based
installation process.
“What is likely happening is that actors are using an already
built malware, capable of installing new APKs on an infected
device, to test a session-based installation method, which would
then later be incorporated in a more elaborate and refined
dropper,” the researchers said.
The changes, should it become a reality, could make the banking
trojans a more dangerous threat capable of bypassing security
defenses even before they are in place.
“With the completion and resolution of all the issues currently
present in BugDrop, criminals will have another efficient weapon in
the war against security teams and banking institutions, defeating
solutions that are currently being adopted by Google, which are
clearly not sufficient to deter criminals,” the company noted.
Users are advised to avoid falling victim to malware hidden in
official app stores by only downloading applications from known
developers and publishers, scrutinizing app reviews, and checking
their privacy policies.
References
- ^
Xenomorph
(thehackernews.com) - ^
BugDrop
(www.threatfabric.com) - ^
dropper
app (thehackernews.com) - ^
Xenomorph and Gymdrop
(thehackernews.com) - ^
Banking
trojans (thehackernews.com) - ^
heavy
abuse (thehackernews.com) - ^
sideloaded
(en.wikipedia.org) - ^
blocking
accessibility API access (blog.esper.io)
Read more https://thehackernews.com/2022/08/cybercriminals-developing-bugdrop.html