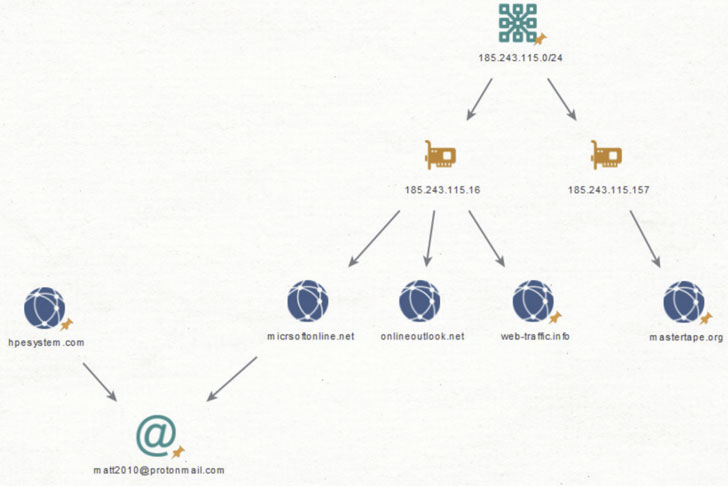
A threat actor, previously known for striking organizations in
the energy and telecommunications sectors across the Middle East as
early as April 2018, has evolved its malware arsenal to strike two
entities in Tunisia.
Security researchers at Kaspersky, who presented their findings
at the VirusBulletin VB2021 conference earlier this month,
attributed the attacks to a group tracked as Lyceum[1]
(aka Hexane), which was first publicly documented[2]
in 2019 by Secureworks.
“The victims we observed were all high-profile Tunisian
organizations, such as telecommunications or aviation companies,”
researchers Aseel Kayal, Mark Lechtik, and Paul Rascagneres
detailed[3]. “Based on the targeted
industries, we assume that the attackers might have been interested
in compromising such entities to track the movements and
communications of individuals of interest to them.”
Analysis of the threat actor’s toolset has shown that the
attacks have shifted from leveraging a combination of PowerShell
scripts and a .NET-based remote administration tool referred called
“DanBot” to two new malware variants written in C++ referred to as
“James” and “Kevin” owing to the recurring use of the names in the
PDB[4]
paths of the underlying samples.
While the “James” sample is heavily based on the DanBot, “Kevin”
comes with major changes in architecture and communication
protocol, with the group predominantly relying on the latter as of
December 2020, indicating an attempt to revamp its attack
infrastructure in response to public disclosure.
That said, both the artifacts support communication with a
remote command-and-server server via custom-designed protocols
tunneled over DNS or HTTP, mirroring the same technique as that of
DanBot. In addition, the attackers are also believed to have
deployed a custom keylogger as well as a PowerShell script in
compromised environments to record keystrokes and plunder
credentials stored in web browsers.
The Russian cybersecurity vendor said that the attack methods
used in the campaign against Tunisian companies resembled
techniques previously attributed to hacking operations associated
with the DNSpionage[5]
group, which, in turn, has exhibited tradecraft overlaps to an
Iranian threat actor dubbed OilRig[6]
(aka APT34), while calling out the “significant similarities”
between lure documents delivered by Lyceum in 2018-2019 and those
used by DNSpionage.
“With considerable revelations on the activity of DNSpionage[7]
in 2018, as well as further data points that shed light on an
apparent relationship with APT34, […] the latter may have changed
some of its modus operandi and organizational structure,
manifesting into new operational entities, tools and campaigns,”
the researchers said. “One such entity is the Lyceum group, which
after further exposure by Secureworks in 2019, had to retool yet
another time.”
References
- ^
Lyceum
(malpedia.caad.fkie.fraunhofer.de) - ^
publicly
documented (www.secureworks.com) - ^
detailed
(securelist.com) - ^
PDB
(en.wikipedia.org) - ^
DNSpionage
(malpedia.caad.fkie.fraunhofer.de) - ^
OilRig
(malpedia.caad.fkie.fraunhofer.de) - ^
activity
of DNSpionage (blog.talosintelligence.com)