- https://resources.infosecinstitute.com/data-retention/#gref
- What is record retention?
- How to determine appropriate data retention?
- Types of Data Retention
- How involved should a security practitioner be in data retention dealings?
- What are the best practices when it comes to data retention?
- Reference List
- What is record retention?
- How to determine appropriate data retention?
- What are the best practices when it comes to data retention?
In essence, these questions, along with their accompanying subsections, cover a small portion of one of the CISSP CBK’s domains, namely, the domain entitled Asset Security (Protecting Security of Assets), which consists of the following topics:
- Information and asset classification
- Ownership (e.g. data owners, system owners)
- Protect privacy
- Appropriate retention √
- Data security controls
- Handling requirements (e.g. markings, labels, storage)
For the most part, this article is based on the 7th edition of CISSP Official Study Guide. Note also that there are 5 questions that appear at different places in the text. They are on topics belonging to the same domain and bear some relation to data retention. You can find their respective answers right after the reference list.
-
What is record retention?
Record retention is a process based on the preservation and maintenance of valuable information as long as it necessary, and then discarding it in a safe manner when its existence is no longer necessary.
![]()
-
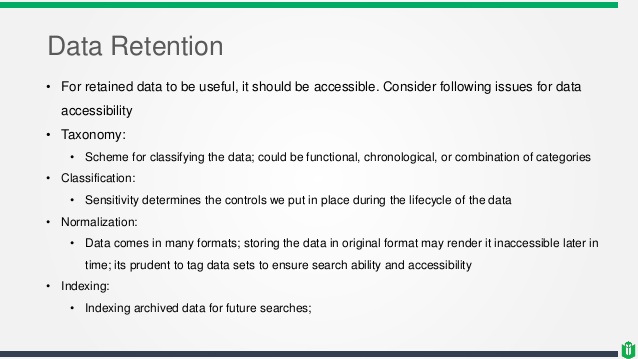
How to determine appropriate data retention?
Retention requirements exist for certain types of sensitive data or records, for example, sensitive data being processed by a computer system, stored on media or accessed by a staffer. While organizations are free to draft their own data retention policy, they must also adhere to a number of data retention laws, especially if these organizations operate within regulated industries. By way of illustration, publicly traded companies in the United States must adhere to a Sarbanes-Oxley Act (SOX) data retention policy, healthcare companies must observe the information retention requirements in the Health Insurance and Portability and Accountability Act (HIPPA), and each organization that deals with credit cards is subject to the Payment Card Industry Data Security Standard (PCI DSS) information retention and disposal policy. Not only laws but also industry standards may specify which records should be retained and for how long.
An excellent illustration of a data retention requirement is the one posed to many organizations to keep all audit logs for a minimum of three years. By doing so, these organization could review past security incidents. Sometimes keeping data indefinitely, however, is not a feasible option as well, because the longer data is retained, the costlier its upkeep will be. Another similar example is provided in the “Official (ISC)2 Guide to the CISSP CBK – Fourth Edition” by Adam Gordon:
“[F]inancial transactions related to a fraud case may need to be retained indefinitely or until ten years after a court judgement. Other information such as system logs may need to be retained for six months or longer to ensure appropriate forensics and incident response capabilities can use the information to reconstruct a past event.”
Although there are some laws which stipulate how long a company should retain data, the company’s security policy or data policy should clearly identify the retention periods even in the absence of external requirements.
The holistic approach might yield good results when used by the security practitioner to create information governance and database archiving policies. It is a step-by-step process which includes:
- Know where the data is stored (i.e., the medium on which the data resides; plus, the logical links among similar pieces of information)
- Classify and label the data – it will show what information need to be archived and for how long, based on retention requirements and business needs.
- Archive and manage data – once the previous step is completed, this process can take place in order to meet all business access needs in line with the defined data retention policies.
Types of Data Retention
Hardware retention – Often hardware products are being replaced every 3-5 years. Hardware retention is likely to refer “to retaining [data] until it has been properly sanitized,” as defined in the “7th edition of CISSP Official Study Guide.”
Personnel retention – On the other hand, the same textbook explains another type of data retention – personnel retention – as “the knowledge that personnel gain while employed by an organization.” Non-disclosure agreements (NDAs) signed by employees upon hiring them prevent these people from sharing proprietary data and trade secrets with others.
In practice, hard- and soft-copy data records are not to be “on hold” beyond its legal or useful lifetime. As to the appropriate formality behind a workable record retention policy, one needs to implement a couple of indispensable steps:
- Document the policy – sometimes simply retaining data is not enough. Federal laws generally require organizations in regulated industries to document the data retention process. Thus, each and every aspect of this process must be written and communicated to everyone who is affected by it
- Attach an activity log of all activities related to the policy, such as training sessions, auditing checks and results, and record destruction processes
- Retention goes hand in hand with security – appropriate security measures are necessary to ward off unauthorized access or inadvertent loss or damage to the information
- Data is to be disposed of properly and securely, in a manner that will render it unusable
Below you can see another interpretation of how one should create a sound record retention policy:
Source: Official (ISC)2 Guide to the CISSP CBK, Fourth Edition by Adam Gordon
How involved should a security practitioner be in data retention dealings?
The main goals of a security expert are, as follows:
1) To help the people in the company understand the retention requirements pursuant to various types of data throughout the company – he must involve all stakeholders in this process (e.g., data owners);
2) To create a records schedule in order to describe the retention requirements for each type of information;
3) To synchronize the systems, processes, and individuals of the company so that the data is kept in accordance with terms described in the schedule and no longer than the schedule envisages – the security practitioner establishes common objectives for supporting the data retention policy enforced by the organizational personnel and diligently followed by all affected users;
4) Monitor, review, update, and improve the policy on an annual basis.
Perhaps the most important objective of the security practitioner with respect to data retention is to ensure that data security is always considered and that a policy on archiving/retention/destruction of data will reflect upon organizational needs. Data archives encryption, for example, is among the most reliable security methods for any solution on the market that aspires to meet regulatory compliance requirements.
-
What are the best practices when it comes to data retention?
Ideally, a data retention policy should take into account data retention laws a company may be subject to, as well as the value of data over time. With a 2006 decision, the U.S. Supreme Court recognized that it is not economically viable for an entity to keep all of its data indefinitely. Nevertheless, companies are more or less obliged to demonstrate that they only destroy what is no longer needed to be kept, as far as laws, regulations and business goals are concerned, and the company is doing so in a consistent and predictable fashion. Consequently, it would be perfectly normal if there is a discrepancy between the length of retention of different types of data. Let’s think, for instance, of what should be the adequate hospital’s retention period with respect to employee emails and patient records. It would be very logical to add more margin of error in handling patient data, since this information almost always have greater value.
To summarize, it is considered bad practice when companies tailor their retention schedule based on the longest retention period they identify, applying it as a cure-all to all retention records. This not only consumes much space and other resources but also creates significant “noise” in cases when employees search or process records.
A successful data retention policy comes along with a sound business rationale for retaining particular records and destroying others. Among the appropriate grounds of such a rationale are aspects ranging from easy access and search in the current corporate database to saving storage space but also keeping backup copies as a precaution against loss of data. For every kind of record, a company, in consultation with the personnel engaged in that matters, should determine clearly defined rules on its detention and destruction. Some of the records are subject to immediate deletion; an example of such data is junk mail. In contrast, no data record is to be deleted if it is of relevance to an anticipated or ongoing litigation process. Provided that there is no legal obligation to keep certain records, a company is free to choose how long to keep them.
As a rule of thumb, an organization’s data records should be disposed of properly when the records’ age exceeds that of the corporate data retention policy. Although no laws compel organizations to discard outdated data, they do so due to resource and capacity constraints, on the one hand, and the unpleasant prospect of this outdated data being subpoenaed in the event of litigation, on the other hand.
One of the downsides of not having a data retention policy in the event of a court order, which orders a company to release a certain type of data, is that this fact in itself may result in a tremendous amount of labour involved in the examination of an entire unstructured database in order to locate this specific data set. It should be noted that the current trend with regard to data retention policies is implementing short email retention policies out of desire to reduce legal liabilities. So, if you happen to be served with a subpoena for email records, you can announce with an open heart something like: “It’s too bad that I deleted the emails. But, hey, they were not classified nor were they even important. These emails were nothing more than family chit-chat. Besides, their retention period required by law and our data retention policy has already passed” – and you will have a legal argument to back up your decision to get rid of the data.
CISSP Instant Pricing- Resources
A record retention policy should be flexible so as to continue to be effective even when it has to undergo changes. An organization’s business needs are shifting and so are the laws. Therefore, this organization, as well as its data retention policy, must be ready to evolve. In addition, experiences and feedback from employees may contribute to a partial or considerable alteration of the record retention policy. When that occurs, it should be accompanied by a training session as soon as possible.
Presumably, all initial efforts will be pointless without proper training right from the outset on the procedures incorporated into the data retention policy. In addition to performing an overall assessment of the effectiveness of this policy, security experts are to be encouraged to get involved in the data retention training of his colleagues. In this regard, the security practitioner should ensure that company staff remain vigilant concerning record retention obligations they may have, but most of all that they are aware of the main rule – e.g., “Do Not delete records unless you are specifically allowed to do that!”
Furthermore, the security professional is responsible for performing periodic audits to ensure that records are either being retained or destroyed in accordance with the corporate data retention policy. The audit will include both paper files and electronic storage media. Retaining data is a continuous process which transcends the mere possession of data, as the security personnel need to ensure the data is accurate and relevant; hence, a periodic review of retained data is a conditio sine qua non.
In the healthcare sector, data is still often kept in archives in so many different forms – in paper, electronic form, and on media (e.g., laboratory samples). Best practices with regard to Data Retention (and Destruction) are often provided by important federal institutions. For instance, the U.S. Department of Health and Human Services Office advises organizations to: destroy paper records in a way that would prevent their reconstruction (fine cross-cut shredding and pulping); for data on media – concerning a prescription bottle, for example, the guidance recommends storing the bottle in an opaque bag and placing it in a secure zone until it is time for its appropriate destruction set out by the company’s security policy; last but not least, protected health information in electronic form can be wiped out when the person entrusted with this tasks employs methods such as clearing and purging (More information here).
How about Europe’s data retention legislation? In a landmark judgement on 8 April 2014 (Digital Rights Ireland (C-293/12)), the European Court of Justice (ECJ) invalidated the EU Data Retention Directive 2006/24/EC. In a nutshell, providers of publicly available communications are no longer obliged to retain certain data on their customers because such data retention was disproportionate in scope and ran counter to the Charter of Fundamental rights of the European Union.