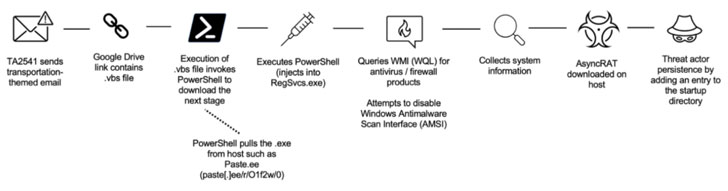
Entities in the aviation, aerospace, transportation,
manufacturing, and defense industries have been targeted by a
persistent threat group since at least 2017 as part of a string of
spear-phishing campaigns mounted to deliver a variety of remote
access trojans (RATs) on compromised systems.
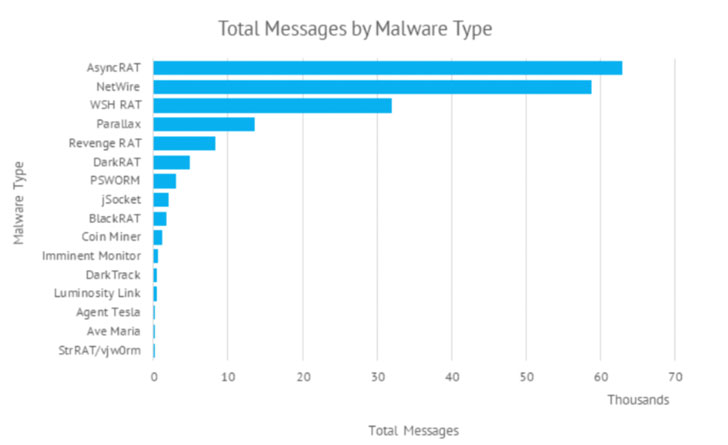
The use of commodity malware such as AsyncRAT and NetWire, among
others, has led enterprise security firm Proofpoint to a
“cybercriminal threat actor” codenamed TA2541[1]
that employs “broad targeting with high volume messages.” The
ultimate objective of the intrusions is unknown as yet.
Social engineering lures used by the group does not rely on
topical themes but rather leverages decoy messages related to
aviation[2], logistics,
transportation, and travel. That said, TA2541 did briefly pivot to
COVID-19-themed lures[3]
in the spring of 2020, distributing emails concerning cargo
shipments of personal protective equipment (PPE) or testing
kits.
“While TA2541 is consistent in some behaviors, such as using
emails masquerading as aviation companies to distribute remote
access trojans, other tactics such as delivery method, attachments,
URLs, infrastructure, and malware type have changed,” Sherrod
DeGrippo, vice president of threat research and detection at
Proofpoint, told The Hacker News.
While earlier versions of the campaign utilized macro-laden
Microsoft Word attachments to drop the RAT payload, recent attacks
include links to cloud services[4]
hosting the malware. The phishing attacks are said to strike
hundreds of organizations globally, with recurring targets observed
in North America, Europe, and the Middle East.
The repeated use of the same themes aside, select infection
chains have also involved the use of Discord app URLs that point to
compressed files containing AgentTesla or Imminent Monitor malware,
indicative of the malicious use of content delivery networks to
distribute information gathering implants for remotely controlling
compromised machines.
“Mitigating threats hosted on legitimate services continues to
be a difficult vector to defend against as it likely involves
implementation of a robust detection stack or policy-based blocking
of services which might be business-relevant,” DeGrippo said.
Other techniques of interest employed by TA2541 include the use
of Virtual Private Servers (VPS) for their email sending
infrastructure and dynamic DNS for command-and-control (C2)
activities.
With Microsoft announcing plans to turn off macros[5]
by default for internet-downloaded files starting April 2022, the
move is expected to cause threat actors to step up and shift to
other methods should macros become an inefficient method of
delivery.
“While macro-laden Office documents are among the most
frequently used techniques leading to download and execution of
malicious payloads, abuse of legitimate hosting services is also
already widespread,” DeGrippo explained.
“Further, we regularly observe actors ‘containerize’ payloads,
using archive and image files (e.g., .ZIP, .ISO, etc.) which also
can impact ability to detect and analyze in some environments. As
always, threat actors will pivot to use what is effective.”
References
- ^
TA2541
(www.proofpoint.com) - ^
aviation
(thehackernews.com) - ^
COVID-19-themed lures
(thehackernews.com) - ^
cloud
services (thehackernews.com) - ^
turn off
macros (thehackernews.com)
Read more https://thehackernews.com/2022/02/experts-warn-of-hacking-group-targeting.html