The notorious Android banking trojan known as SharkBot[1]
has once again made an appearance on the Google Play Store by
masquerading as antivirus and cleaner apps.
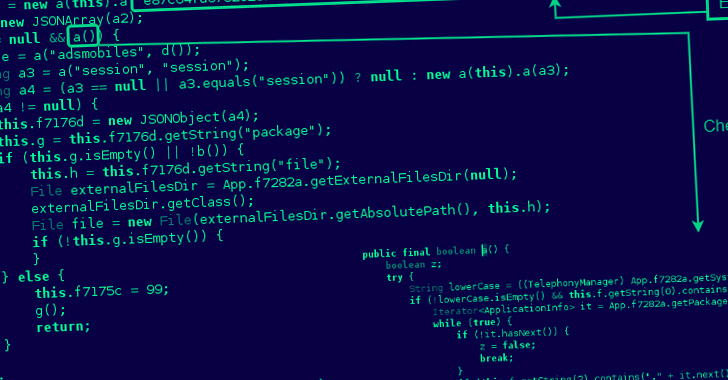
“This new dropper doesn’t rely on Accessibility permissions to
automatically perform the installation of the dropper Sharkbot
malware,” NCC Group’s Fox-IT said[2]
in a report. “Instead, this new version asks the victim to install
the malware as a fake update for the antivirus to stay protected
against threats.”
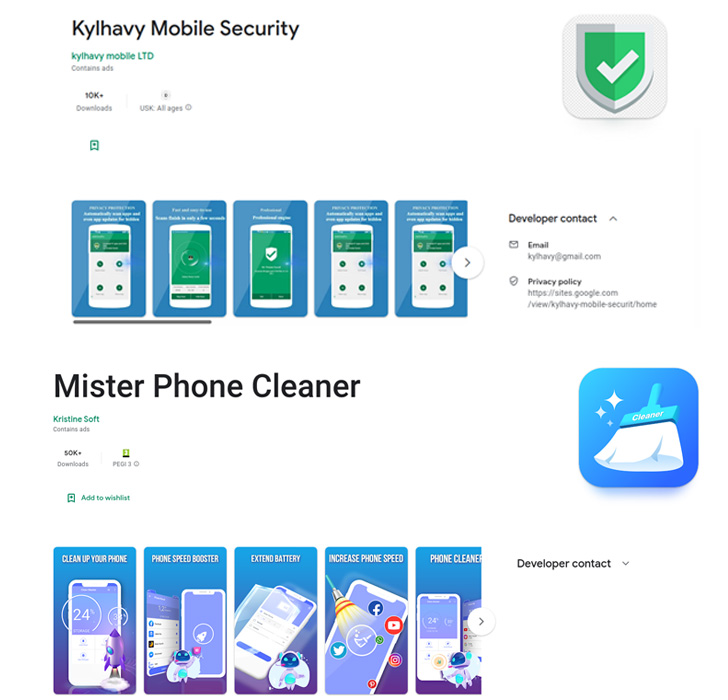
The apps in question, Mister Phone Cleaner and Kylhavy Mobile
Security, have over 60,000 installations between them and are
designed to target users in Spain, Australia, Poland, Germany, the
U.S., and Austria –
- Mister Phone Cleaner (com.mbkristine8.cleanmaster, 50,000+
downloads) - Kylhavy Mobile Security (com.kylhavy.antivirus, 10,000+
downloads)
The droppers[3]
are designed to drop a new version of SharkBot, dubbed V2[4]
by Dutch security firm ThreatFabric, which features an updated
command-and-control (C2) communication mechanism, a domain
generation algorithm (DGA), and a fully refactored codebase.
Fox-IT said it discovered a newer version 2.25 on August 22,
2022, that introduces a function to siphon cookies when victims log
in to their bank accounts, while also removing the ability to
automatically reply to incoming messages with links to the malware
for propagation.
By eschewing the Accessibility permissions for installing
SharkBot, the development highlights that the operators are
actively tweaking their techniques to avoid detection, not to
mention find alternative methods in the face of Google’s newly imposed restrictions[5] to curtail the abuse of
the APIs.
Other notable information stealing capabilities include
injecting fake overlays to harvest bank account credentials,
logging keystrokes, intercepting SMS messages, and carrying out
fraudulent fund transfers using the Automated Transfer System
(ATS[6]).
It’s no surprise that malware poses an evolving and omnipresent
threat, and despite continued efforts on the part of Apple and
Google, app stores are vulnerable to unknowingly being abused for
distribution, with the developers of these apps trying every trick
in the book to dodge security checks.
“Until now, SharkBot’s developers seem to have been focusing on
the dropper in order to keep using Google Play Store to distribute
their malware in the latest campaigns,” researchers Alberto Segura
and Mike Stokkel said.
References
Read more https://thehackernews.com/2022/09/fake-antivirus-and-cleaner-apps-caught.html