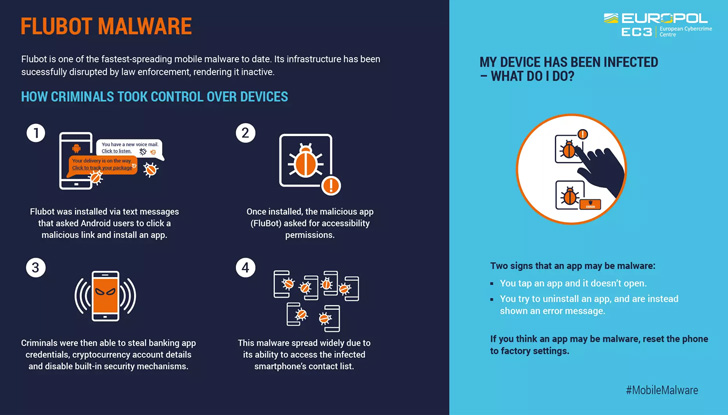
An international law enforcement operation involving 11
countries has culminated in the takedown of a notorious mobile
malware threat called FluBot[1].
“This Android malware has been spreading aggressively through
SMS, stealing passwords, online banking details and other sensitive
information from infected smartphones across the world,” Europol
said[2]
in a statement.
The “complex investigation” included authorities from Australia,
Belgium, Finland, Hungary, Ireland, Romania, Spain, Sweden,
Switzerland, the Netherlands, and the U.S.
FluBot[3], also called Cabassous,
emerged in the wild in December 2020, masking its insidious intent
behind the veneer of seemingly innocuous package tracking
applications such as FedEx, DHL, and Correos.
It primarily spreads via smishing (aka SMS-based phishing)
messages that trick unsuspecting recipients into clicking on a link
to download the malware-laced apps.
Once launched, the app would proceed to request access to
Android’s Accessibility Service to stealthily siphon bank account
credentials and other sensitive information stored in
cryptocurrency apps.
To make matters worse, the malware leveraged its access to
contacts stored in the infected device to propagate the infection
further by sending messages containing links to the FluBot
malware.
FluBot campaigns, while primarily an Android malware, have also
evolved
to target iOS users[4]
in recent months, wherein users attempting to access the infected
links are redirected to phishing sites and subscription scams.
“This FluBot infrastructure is now under the control of law
enforcement, putting a stop to the destructive spiral,” the agency
noted, adding that the Dutch Police orchestrated the seizure last
month.
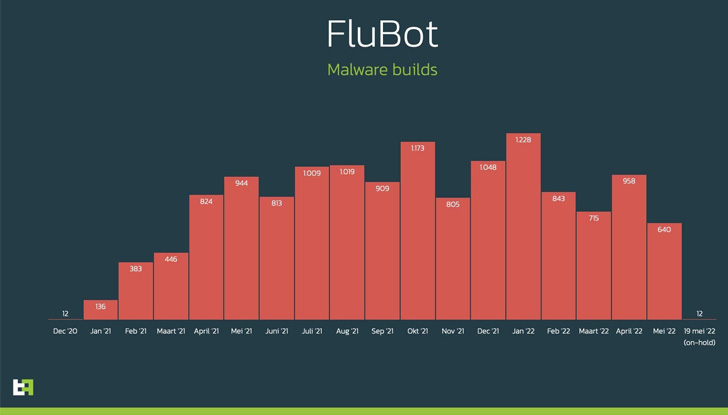
According to ThreatFabric’s mobile threat landscape report[5] for H1 2022, FluBot was
the second most active banking trojan behind Hydra, accounting for
20.9% of the samples observed between January and May.
“ThreatFabric has closely worked with law enforcement on the
case,” founder and CEO Han Sahin told The Hacker News.
“It’s a great win considering FluBot threat actors have or had
one of the most resilient strategies when it comes to distribution
and hosting of their backends with DNS-tunneling through public DNS-over-HTTPS
services[6]. This backend resilience
in C2 hosting and fronting is what makes the efforts of the Dutch digital crime
unit[7] very impressive.”
The Dutch cybersecurity company also noted that unique malware
samples developed by the operators of FluBot stopped after May 19,
coinciding with the takedown, effectively slowing their “worming
efforts.”
“The overall impact [of the dismantling] on the mobile threat
landscape is limited since FluBot is not the strongest Android
banking trojan,” Sahin added. “Exo, Anatsa, Gustuff, those are a
real problem to any user. The power behind FluBot has always been
[its] infection numbers.”
References
- ^
FluBot
(thehackernews.com) - ^
said
(www.europol.europa.eu) - ^
FluBot
(thehackernews.com) - ^
evolved to target iOS users
(www.bitdefender.com) - ^
mobile
threat landscape report (thehackernews.com) - ^
DNS-tunneling through public
DNS-over-HTTPS services (twitter.com) - ^
Dutch digital crime unit
(www.politie.nl)
Read more https://thehackernews.com/2022/06/flubot-android-spyware-taken-down-by.html