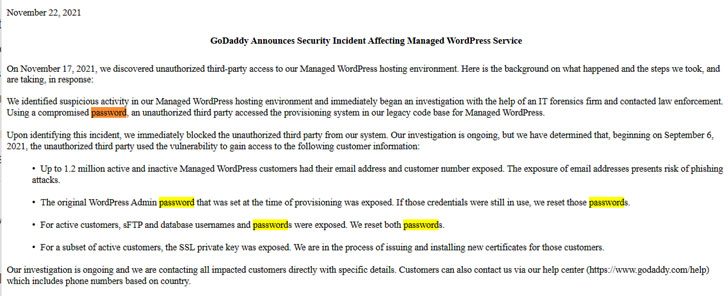
Web hosting giant GoDaddy on Monday disclosed a data breach that
resulted in the unauthorized access of data belonging to a total of
1.2 million active and inactive customers, making it the third[1]
security incident[2]
to come to light since 2018.
In a filing with the U.S. Securities and Exchange Commission
(SEC), the world’s largest domain registrar said[3]
that a malicious third-party managed to gain access to its Managed WordPress[4]
hosting environment on September 6 with the help of a compromised
password, using it to obtain sensitive information pertaining to
its customers. It’s not immediately clear if the compromised
password was secured with two-factor authentication.
The Arizona-based company claims[5]
over 20 million customers, with more than 82 million domain names
registered using its services.
GoDaddy revealed it discovered the break-in on November 17. An
investigation into the incident is ongoing and the company said
it’s “contacting all impacted customers directly with specific
details.” The following information is believed to have been
accessed by the intruder —
- Email addresses and customer numbers of up to 1.2 million
active and inactive Managed WordPress customers - Original WordPress Admin password that was set at the time of
provisioning was exposed - sFTP[6]
and database usernames and passwords associated with its active
customers, and - SSL private keys for a subset of active customers
GoDaddy said it’s in the process of issuing and installing new
certificates for the impacted customers. As a precautionary
measure, the company also stated it has reset the affected
passwords and it’s bolstering its provisioning system with added
security protections.
According to Wordfence CEO Mark Maunder[7], “GoDaddy stored sFTP
passwords in such a way that the plaintext versions of the
passwords could be retrieved, rather than storing salted hashes of
these passwords, or providing public key authentication, which are
both industry best practices.”
While data breaches are no longer a sporadic occurrence, the
exposure of email addresses and passwords presents risk of phishing
attacks, not to mention enable the attackers to breach the
vulnerable WordPress sites to upload malware and access other
personally identifiable information stored in them.
“On sites where the SSL private key was exposed, it could be
possible for an attacker to decrypt traffic using the stolen SSL
private key, provided they could successfully perform a
man-in-the-middle (MITM) attack that intercepts encrypted traffic
between a site visitor and an affected site,” Maunder said.
References
- ^
third
(www.upguard.com) - ^
security
incident (www.bleepingcomputer.com) - ^
said
(www.sec.gov) - ^
Managed
WordPress (in.godaddy.com) - ^
claims
(aboutus.godaddy.net) - ^
sFTP
(in.godaddy.com) - ^
Mark
Maunder (www.wordfence.com)
Read more https://thehackernews.com/2021/11/godaddy-data-breach-exposes-over-1.html