Web infrastructure company Cloudflare on Tuesday disclosed at
least 76 employees and their family members received text messages
on their personal and work phones bearing similar characteristics
as that of the sophisticated phishing attack against Twilio[1].
The attack, which transpired around the same time Twilio was
targeted, came from four phone numbers associated with
T-Mobile-issued SIM cards amd was ultimately unsuccessful.
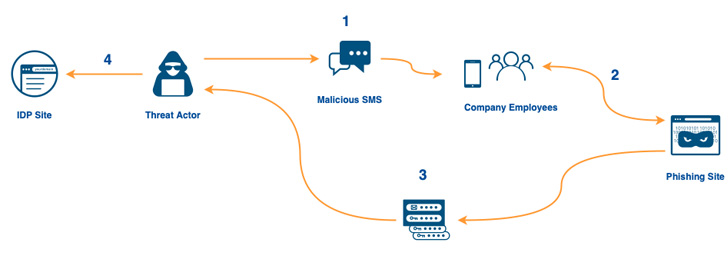
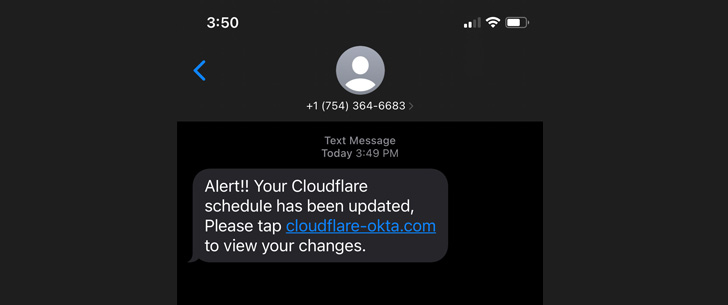
The text messages pointed to a seemingly legitimate domain
containing the keywords “Cloudflare” and “Okta” in an attempt to
deceive the employees into handing over their credentials.
The wave of over 100 smishing messages commenced less than 40
minutes after the rogue domain was registered via Porkbun, the
company noted, adding the phishing page was designed to relay the
credentials entered by unsuspecting users to the attacker via
Telegram in real-time.
This also meant that the attack could defeat 2FA roadblocks, as
the Time-based One Time Password (TOTP[2]) codes inputted on the
fake landing page were transmitted in an analogous manner, enabling
the adversary to sign-in with the stolen passwords and TOTPs.
Cloudflare said three of its employees fell for the phishing
scheme, but noted that it was able to prevent its internal systems
from being breached through the use of FIDO2-compliant physical
security keys required to access its applications.
“Since the hard keys are tied to users and implement origin
binding, even a sophisticated, real-time phishing operation like
this cannot gather the information necessary to log in to any of
our systems,” Cloudflare said.
“While the attacker attempted to log in to our systems with the
compromised username and password credentials, they could not get
past the hard key requirement.”
What’s more, the attacks didn’t just stop at stealing the
credentials and TOTP codes. Should an employee get past the login
step, the phishing page was engineered to automatically download
AnyDesk’s remote access software, which, if installed, could be
used to commandeer the victim’s system.
Besides working with DigitalOcean to shut down the attacker’s
server, the company also said it reset the credentials of the
impacted employees and that it’s tightening up its access
implementation to prevent any logins from unknown VPNs, residential
proxies, and infrastructure providers.
The development comes days after Twilio said unknown hackers
succeeded in phishing the credentials of an undisclosed number of
employees and gained unauthorized access to the company’s internal
systems, using it to get hold of customer accounts.
References
- ^
phishing
attack against Twilio (thehackernews.com) - ^
TOTP
(en.wikipedia.org)
Read more https://thehackernews.com/2022/08/hackers-behind-twilio-breach-also_10.html