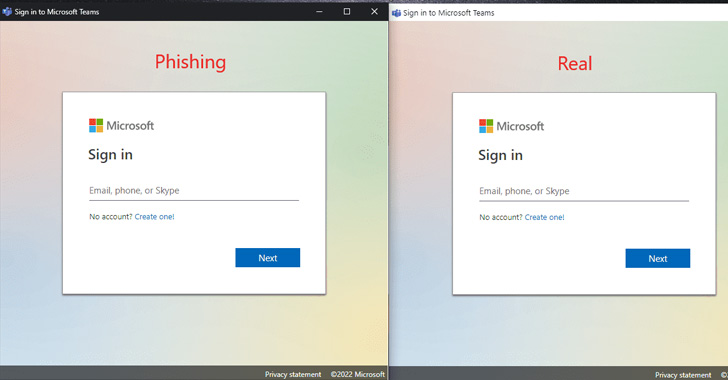
In what’s a new phishing technique, it has been demonstrated
that the Application Mode feature in Chromium-based web browsers
can be abused to create “realistic desktop phishing
applications.”
Application Mode is designed to offer native-like experiences in
a manner that causes the website to be launched in a separate
browser window, while also displaying the website’s favicon and
hiding the address bar.
According to security researcher mr.d0x – who also devised the
browser-in-the-browser (BitB[1]) attack method earlier
this year – a bad actor can leverage this behavior to resort to
some HTML/CSS trickery and display a fake address bar on top of the
window and fool users into giving up their credentials on rogue
login forms.
“Although this technique is meant more towards internal
phishing, you can technically still use it in an external phishing
scenario,” mr.d0x said[2]. “You can deliver these
fake applications independently as files.”
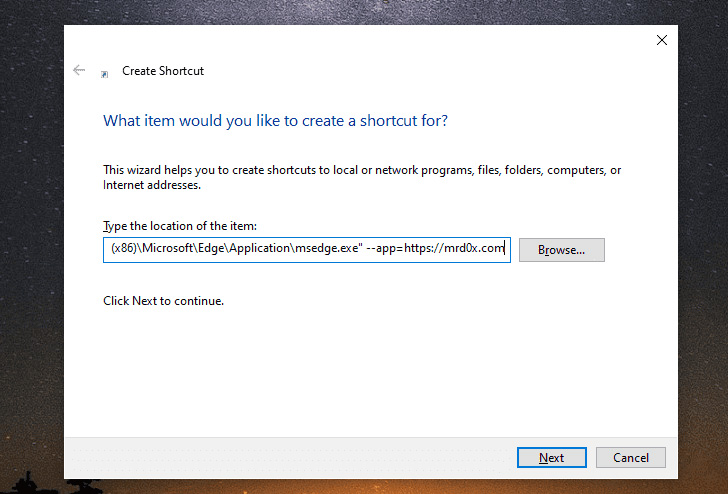
This is achieved by setting up a phishing page with a fake
address bar at the top, and configuring the –app parameter[3]
to point to the phishing site hosting the page.
On top of that, the attacker-controlled phishing site can make
use of JavaScript to take more actions, such as closing the window
immediately after the user enters the credentials or resizing and
positioning it to achieve the desired effect.
It’s worth noting that the mechanism works on other operating
systems, such as macOS and Linux, making it a potential
cross-platform threat. However, the success of the attack is
predicated on the fact that the attacker already has access to the
target’s machine.
That said, Google is phasing out[4]
support for Chrome apps in favor of Progressive Web Apps (PWAs) and
web-standard technologies, and the feature is expected to be fully
discontinued in Chrome 109 or later on Windows, macOS, and
Linux.
The findings come as new findings Trustwave SpiderLabs show[5]
that HTML smuggling[6]
attacks are a common occurrence, with .HTML (11.39%) and .HTM
(2.7%) files accounting for the second most spammed file attachment
type after .JPG images (25.29%).
References
- ^
BitB
(thehackernews.com) - ^
said
(mrd0x.com) - ^
–app
parameter (manpages.ubuntu.com) - ^
phasing
out (support.google.com) - ^
show
(www.trustwave.com) - ^
HTML
smuggling (thehackernews.com)
Read more https://thehackernews.com/2022/10/hackers-can-use-app-mode-in-chromium.html