protect your devices leave backdoors open for hackers or turn into
malware?
Researchers today revealed that a security app that comes
pre-installed on more than 150 million devices manufactured by
Xiaomi, China’s biggest and world’s 4th largest smartphone company,
was suffering from multiple issues that could have allowed remote
hackers to compromise Xiaomi smartphones.
According to CheckPoint, the reported issues resided in one of
the pre-installed application called, Guard Provider, a
security app developed by Xiaomi that includes three different
antivirus programs packed inside it, allowing users to choose
between Avast, AVL, and Tencent.
Since Guard Provider has been designed to offer multiple 3rd-party
programs within a single app, it uses several Software Development
Kits (SDKs), which according to researchers is not a great idea
because data of one SDK cannot be isolated and any issue in one of
them could compromise the protection provided by others.
“The hidden disadvantages in using several SDKs within the same app
lie in the fact that they all share the app context and
permissions,” the security firm says.
“While minor bugs in each individual SDK can often be a
standalone issue, when multiple SDKs are implemented within the
same app it is likely that even more critical vulnerabilities will
not be far off.”
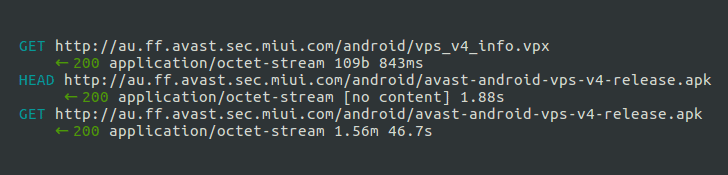
was downloading antivirus signature updates through an unsecured
HTTP connection, allowing man-in-the-middle attackers sitting on
open WiFi network to intercept your device’s network connection and
push malicious updates.
“Once connected to the same Wi-Fi network as the victim – say, in
public places i.e. at restaurants, coffee shops, or malls – the
attacker would be able to gain access to the phone owner’s
pictures, videos, and other sensitive data, or inject malware,”
CheckPoint told The Hacker News.
However, the actual attack scenario is not as straightforward as
it may sound.
As explained[1]
by CheckPoint, researchers successfully achieved remote code
execution on the targeted Xiaomi device after exploiting four
separate issues in two different SDKs available in the app.
The attack basically leveraged the use of unsecured HTTP
connection, a path-traversal vulnerability and lack of digital
signature verification while downloading and installing an
antivirus update on the device.
“It is completely understandable that users would put their trust
in smartphone manufacturers’ preinstalled apps, especially when
those apps claim to protect the phone itself,” the firm says.
Xiaomi has now fixed the issues in the latest version of its Guard
Provider app.
So, if you own a Xiaomi smartphone you should make sure your
security software is up-to-date.
Read more http://feedproxy.google.com/~r/TheHackersNews/~3/fTKNVNbpDV8/xiaomi-antivirus-app.html