A zero-day flaw in a WordPress plugin called BackupBuddy[1] is being actively
exploited, WordPress security company Wordfence has disclosed.
“This vulnerability makes it possible for unauthenticated users
to download arbitrary files from the affected site which can
include sensitive information,” it said[2].
BackupBuddy allows users to back up their entire WordPress
installation from within the dashboard, including theme files,
pages, posts, widgets, users, and media files, among others.
The plugin is estimated to have around 140,000 active
installations, with the flaw (CVE-2022-31474, CVSS score: 7.5)
affecting versions 8.5.8.0 to 8.7.4.1. It’s been addressed in
version 8.7.5 released on September 2, 2022.
The issue is rooted in the function called “Local Directory
Copy” that’s designed to store a local copy of the backups.
According to Wordfence, the vulnerability is the result of the
insecure implementation, which enables an unauthenticated threat
actor to download any arbitrary file on the server.
Additional details about the flaw have been withheld in light of
active in-the-wild abuse and its ease of exploitation.
“This vulnerability could allow an attacker to view the contents
of any file on your server that can be read by your WordPress
installation,” the plugin’s developer, iThemes, said[3]. “This could include the
WordPress wp-config.php file and, depending on your server setup,
sensitive files like /etc/passwd.”
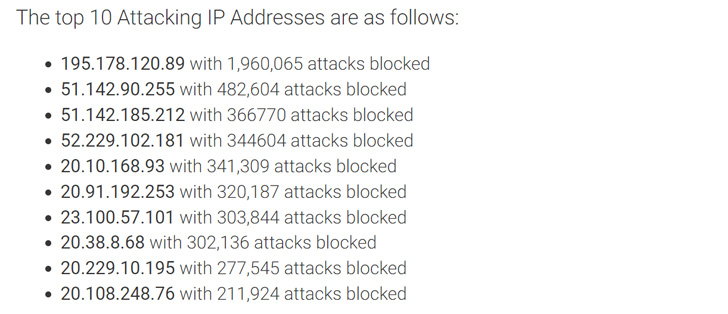
Wordfence noted that the targeting of CVE-2022-31474 commenced
on August 26, 2022, and that it has blocked nearly five million
attacks in the intervening time period. Most of the intrusions have
attempted to read the below files –
- /etc/passwd
- /wp-config.php
- .my.cnf
- .accesshash
Users of the BackupBuddy plugin are advised to upgrade to the
latest version. Should users determine that they may have been
compromised, it’s recommended to reset the database password,
change WordPress Salts, and rotate API keys stored in
wp-config.php.
Read more https://thehackernews.com/2022/09/hackers-exploit-zero-day-in-wordpress.html