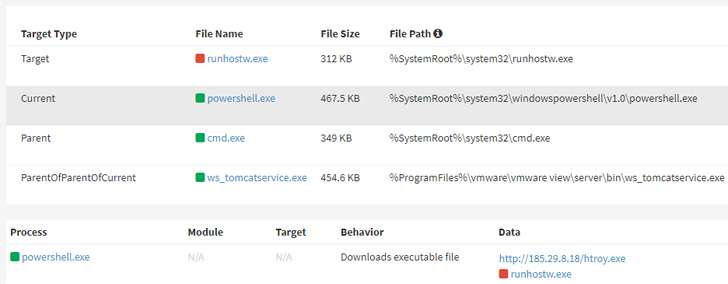
The North Korea-backed Lazarus Group has been observed
leveraging the Log4Shell vulnerability[1]
in VMware Horizon servers to deploy the NukeSped (aka
Manuscrypt) implant against targets located in its southern
counterpart.
“The attacker used the Log4j vulnerability on VMware Horizon
products that were not applied with the security patch,” AhnLab
Security Emergency Response Center (ASEC) said[2] in a new report.
The intrusions are said to have been first discovered in April,
although multiple threat actors[3], including those aligned
with China[4]
and Iran[5], have employed the same
approach to further their objectives over the past few months.
NukeSped is a backdoor that can perform various malicious
activities based on commands received from a remote
attacker-controlled domain. Last year, Kaspersky disclosed a
spear-phishing campaign aimed at stealing critical data from
defense companies using a NukeSped variant called ThreatNeedle[6].
Some of the key functions of the backdoor range from capturing
keystrokes and taking screenshots to accessing the device’s webcam
and dropping additional payloads such as information stealers.
The stealer malware, a console-based utility, is designed to
exfiltrate accounts and passwords saved in web browsers like Google
Chrome, Mozilla Firefox, Internet Explorer, Opera, and Naver Whale
as well as information about email accounts and recently opened
Microsoft Office and Hancom files.
“The attacker collected additional information by using backdoor
malware NukeSped to send command line commands,” the researchers
said. “The collected information can be used later in lateral
movement attacks.”
References
- ^
Log4Shell vulnerability
(thehackernews.com) - ^
said
(asec.ahnlab.com) - ^
multiple
threat actors (thehackernews.com) - ^
China
(thehackernews.com) - ^
Iran
(thehackernews.com) - ^
ThreatNeedle
(thehackernews.com)
Read more https://thehackernews.com/2022/05/hackers-exploiting-vmware-horizon-to.html