Microsoft on Tuesday warned that it recently spotted a malicious
campaign targeting SQL Servers that leverages a built-in PowerShell
binary to achieve persistence on compromised systems.
The intrusions, which leverage brute-force attacks as an initial
compromise vector, stand out for their use of the utility “sqlps.exe[1],” the tech giant
said[2]
in a series of tweets.
The ultimate goals of the campaign are unknown, as is the
identity of the threat actor staging it. Microsoft is tracking the
malware under the name “SuspSQLUsage[3].”
The sqlps.exe utility, which comes by default with all versions
of SQL Servers, enables an SQL Agent — a Windows service to run
scheduled tasks — to run jobs using the PowerShell subsystem.
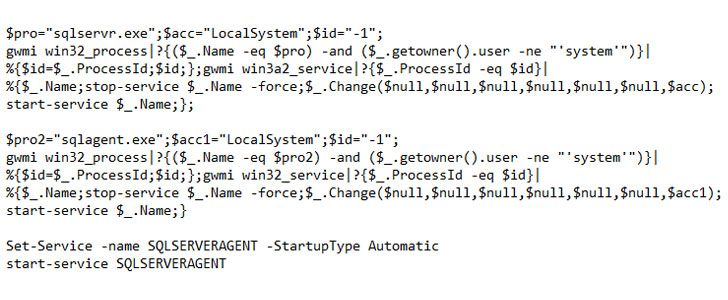
“The attackers achieve fileless persistence by spawning the
sqlps.exe utility, a PowerShell wrapper for running SQL-built
cmdlets, to run recon commands and change the start mode of the SQL
service to LocalSystem,” Microsoft noted.
Additionally, the attackers have also been observed using the
same module to create a new account with sysadmin role[4], effectively making it
possible to seize control over the SQL Server.
This is not the first time threat actors have weaponized
legitimate binaries[5]
already present in an environment, a technique called
living-off-the-land (LotL), to achieve their nefarious goals.
An advantage offered by such attacks is that they tend to be
fileless[6]
because they do not leave any artifacts behind and the activities
are less likely to be flagged by antivirus software owing to them
using trusted software.
The idea is to allow the attacker to blend in with regular
network activity and normal administrative tasks, while remaining
hidden for extended periods of time.
“The use of this uncommon living-off-the-land binary (LOLBin)
highlights the importance of gaining full visibility into the
runtime behavior of scripts in order to expose malicious code,”
Microsoft said.
References
- ^
sqlps.exe
(docs.microsoft.com) - ^
said
(twitter.com) - ^
SuspSQLUsage
(www.microsoft.com) - ^
sysadmin
role (docs.microsoft.com) - ^
legitimate binaries
(thehackernews.com) - ^
fileless
(docs.microsoft.com)
Read more https://thehackernews.com/2022/05/hackers-gain-fileless-persistence-on.html