A new spam email campaign has emerged as a conduit for a
previously undocumented malware loader that enables the attackers
to gain an initial foothold into enterprise networks and drop
malicious payloads on compromised systems.
“These infections are also used to facilitate the delivery of
additional malware such as Qakbot and Cobalt Strike, two of the
most common threats regularly observed targeting organizations
around the world,” said[1]
researchers with Cisco Talos in a technical write-up.
The malspam campaign is believed to have commenced in
mid-September 2021 via laced Microsoft Office documents that, when
opened, triggers an infection chain that leads to the machines
getting infected with a malware dubbed SQUIRRELWAFFLE.
Mirroring a technique that’s consistent with other phishing
attacks of this kind, the latest operation leverages stolen email
threads to give it a veil of legitimacy and trick unsuspecting
users into opening the attachments.
What’s more, the language employed in the reply messages matches
the language used in the original email thread, demonstrating a
case of dynamic localization put in place to increase the
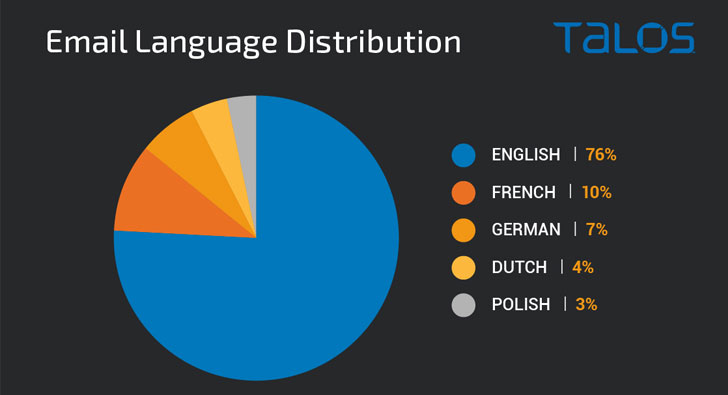
likelihood of success of the campaign. The top five languages used
to deliver the loader are English (76%), followed by French (10%),
German (7%), Dutch (4%), and Polish (3%).
Email distribution volumes capitalizing on the new threat peaked
around September 26, based on data compiled by the cybersecurity
firm.
While previously compromised web servers, primarily running
versions of the WordPress content management system (CMS), function
as the malware distribution infrastructure, an interesting
technique observed is the use of “antibot” scripts to block web
requests that originate from IP addresses not belonging to victims
but rather automated analysis platforms and security research
organizations.
The malware loader, besides deploying Qakbot and the infamous
penetration testing tool Cobalt Strike on the infected endpoints,
also establishes communications with a remote attacker-controlled
server to retrieve secondary payloads, making it a potent
multi-purpose utility.
“After the Emotet botnet takedown[2]
earlier this year, criminal threat actors are filling that void,”
Zscaler noted[3]
in an analysis of the same malware last month. “SQUIRRELWAFFLE
appears to be a new loader taking advantage of this gap. It is not
yet clear if SQUIRRELWAFFLE is developed and distributed by a known
threat actor or a new group. However, similar distribution
techniques were previously used by Emotet.”