Cyberattacks targeting healthcare organizations have spiked by
45% since November 2020 as COVID-19 cases continue to increase
globally.
According to a new report published by Check Point Research
today[1] and shared with The
Hacker News, this increase has made the sector the most targeted
industry by cybercriminals when compared to an overall 22% increase
in cyberattacks across all industry sectors worldwide seen during
the same time period.
The average number of weekly attacks in the healthcare sector
reached 626 per organization in November as opposed to 430 the
previous month, with attack vectors ranging from ransomware,
botnets, remote code execution, and distributed denial-of-service
(DDoS) attacks.
Ransomware attacks against hospitals also marked their biggest
jump, with Ryuk[2]
and Sodinokibi emerging as the primary ransomware variants employed
by various criminal groups.
“The usage of Ryuk emphasizes the trend of having more targeted
and tailored ransomware attacks rather than using a massive spam
campaign, which allows the attackers to make sure they hit the most
critical parts of the organization and have a higher chance of
getting paid,” Omer Dembinsky, Check Point’s manager of data
intelligence, said.
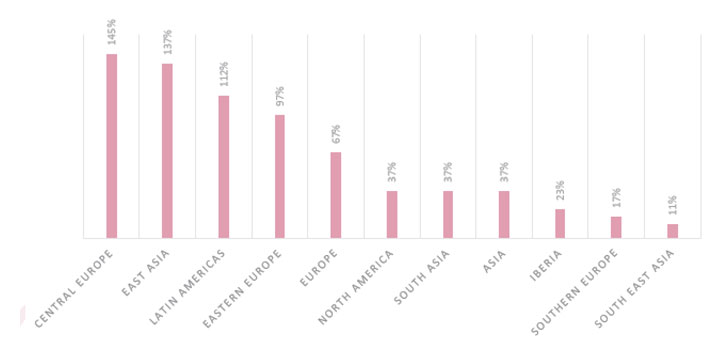
Central Europe topped the list of regions impacted by the
increase in attacks against healthcare organizations with a 145%
uptick in November, followed by East Asia (up 137%) and Latin
America (up 112% increase). Europe and North America saw increases
of 67% and 37% respectively.
The development follows a joint advisory[3]
from the U.S. Cybersecurity and Infrastructure Security Agency
(CISA), the Federal Bureau of Investigation (FBI), and the
Department of Health and Human Services (HHS) last October, warning
of an “increased and imminent cybercrime threat to U.S. hospitals
and healthcare providers.”
The alert cautioned of adversaries targeting the Healthcare and
Public Health (HPH) sector with TrickBot and BazarLoader malware,
resulting in ransomware infections, data theft, and the disruption
of healthcare services.
Over the past two months, state-sponsored actors have ramped up[4]
their cyber assaults[5]
against government health ministries and companies involved in
COVID-19 vaccine distribution, not to mention staging ransomware
attacks on pharmaceutical firms such as Dr. Reddy’s Laboratories
that are engaged in vaccine trials.
Ransomware cases, in particular, have capitalized[6]
on the coronavirus pandemic, not least because it boosts the
likelihood that hospitals will meet attackers’ demands to quickly
recover access to critical systems and provide care to patients.
The University of California paid the hackers 116 bitcoin ($1.14
million) after a NetWalker attack[7]
on its systems back in June.
“Medical services and research organizations [have become]
targets for attacks seeking to steal valuable commercial and
professional information, or to disrupt vital research operations,”
the researchers concluded.
“As the world’s attention continues to focus on dealing with the
pandemic, cybercriminals will also continue to use and try to
exploit that focus for their own illegal purposes — so it’s
essential that both organizations and individuals maintain good
cyber-hygiene to protect themselves against Covid-related online
crime.”
References
- ^
today
(blog.checkpoint.com) - ^
Ryuk
(blog.checkpoint.com) - ^
joint
advisory (us-cert.cisa.gov) - ^
ramped
up (thehackernews.com) - ^
cyber
assaults (thehackernews.com) - ^
capitalized
(thehackernews.com) - ^
NetWalker attack
(www.ucsf.edu)