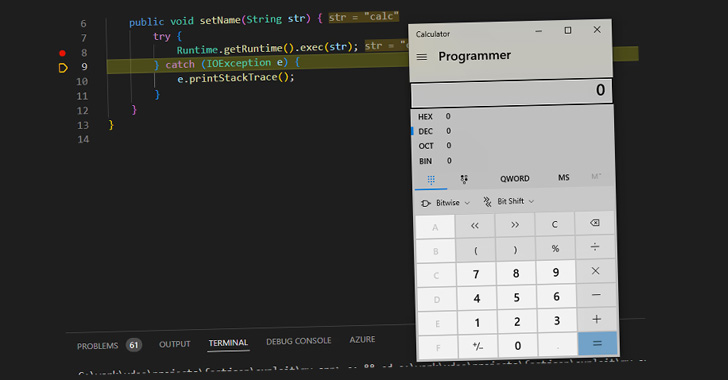
Cybersecurity researchers have detailed a recently patched
high-severity security vulnerability in the popular Fastjson
library that could be potentially exploited to achieve remote
code execution.
Tracked as CVE-2022-25845[1]
(CVSS score: 8.1), the issue[2]
relates to a case of deserialization of untrusted data[3] in a supported feature
called “AutoType.” It was patched by the project maintainers in
version 1.2.83[4]
released on May 23, 2022.
“This vulnerability affects all Java applications that rely on
Fastjson versions 1.2.80 or earlier and that pass user-controlled
data to either the JSON.parse or JSON.parseObject APIs without
specifying a specific class[5]
to deserialize,” JFrog’s Uriya Yavnieli said[6]
in a write-up.
Fastjson[7]
is a Java library that’s used to convert Java Objects into their
JSON[8]
representation and vice versa. AutoType[9], the function vulnerable
to the flaw, is enabled by default and is designed to specify a
custom type when parsing a JSON input that can then be deserialized[10] into an object of the
appropriate class.
“However, if the deserialized JSON is user-controlled, parsing
it with AutoType enabled can lead to a deserialization security
issue, since the attacker can instantiate any class that’s
available on the Classpath[11], and feed its
constructor with arbitrary arguments,” Yavnieli explained.
While the project owners previously introduced a safeMode that
disables AutoType and started maintaining a blocklist of classes[12] to defend against
deserialization flaws, the newly discovered flaw gets around the
latter of these restrictions to result in remote
code execution[13].
Users of Fastjson are recommended to update to version 1.2.83 or
enable safeMode, which turns off the function regardless of the
allowlist and blocklist used, effectively closing variants of the
deserialization attack.
“Although a public PoC exploit[14] exists and the
potential impact is very high (remote code execution) the
conditions for the attack are not trivial (passing untrusted input
to specific vulnerable APIs) and most importantly — target-specific
research is required to find a suitable gadget class to exploit,”
Yavnieli said.
References
- ^
CVE-2022-25845
(nvd.nist.gov) - ^
issue
(github.com) - ^
deserialization of untrusted data
(cwe.mitre.org) - ^
version
1.2.83 (github.com) - ^
class
(en.wikipedia.org) - ^
said
(jfrog.com) - ^
Fastjson
(github.com) - ^
JSON
(en.wikipedia.org) - ^
AutoType
(medium.com) - ^
deserialized
(snyk.io) - ^
Classpath
(en.wikipedia.org) - ^
blocklist of classes
(github.com) - ^
result
in remote code execution (github.com) - ^
public
PoC exploit (github.com)
Read more https://thehackernews.com/2022/06/high-severity-rce-vulnerability.html