web application firewall (WAF) is the first line of defense and a
necessary part of organizations’ cybersecurity strategies.
WAFs are getting more sophisticated all the time, but as its
core protection starts with efficient pattern matching, typically
using Regular Expressions, and classifying malicious traffic to
block cyber attacks.
Evading pattern matching
However, unfortunately, this technique is no silver bullet against
determined attackers. Once it’s known that there is a protection
layer enabled, malicious actors find ways to bypass it, and most of
the time, they even succeed.
It usually can be achieved when the same attacking payload,
blocked by WAF, can be
disguised to make it ‘invisible’ to the pattern matching mechanism
to evade security.
[1]
Context-Specific Obfuscation
The web uses many technologies, and they all have different rules
for what comprises valid syntax in their grammar, e.g., the browser
itself has (at least) 3 different grammars – HTML, CSS, and
JavaScript.
Depending on the context where the attack is targeted, payloads
using mixed case, whitespace, comments work in the same way as the
original payload.
Encodings
There are numerous ways to encode the requests sent, including
standard encodings like URL, Hex, Base64, character encoding, etc.
The parameter/payload can be encoded multiple times with any
combination of encodings allowing the encoded attack payload to
slip through.
A flavor of some of the evasions

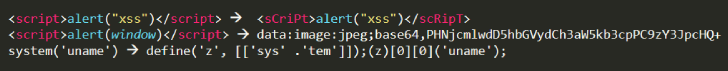 These evasions are not
These evasions are not
hypothetical, and there are known cases of commercial WAFs being
bypassed by things like Unicode encoding.
How does AppTrana handle evasions
Real-world attacks often include multiple steps, including
reconnaissance and a combination of attacks, so behavior profiling,
anomaly scoring provide automated mitigation, and security experts,
like the Indusface
security research team, can quickly see if the attack is new or
unique and take appropriate action.
Some of the anti-evasion techniques used are listed
below.
Transformation
Evasions like the obfuscations and encodings above are handled by
AppTrana using transformation functions and canonicalization on the
data before running the inspection/pattern matching phase. The
order in which transformations are applied matters much and can
vary by context.
Anomaly scoring and Behavior profiling
Some patterns are too small or too common to make complete security
decisions. AppTrana has rules that treat certain occurrences as
indicators, and, using scoring mechanisms, it makes confident
decisions.
Data including metrics are tracked during a user session, and
the risk score of that session is calculated. e.g., in a travel
site, if a user moves unusually fast to booking, it is likely to be
a bot, and a captcha could be thrown up.
Custom rules
AppTrana out of the box protection blocks a broad set of attacks
and handles most of the evasions. Indusface Managed service
included with the AppTrana WAF augments this with customized
protection developed after understanding the specific customer
application in detail.
Attacks leveraging application behavior/features that can be
misused/quirks can be handled only in this way.
How to evaluate WAF
Any security solution should be regularly evaluated in terms of
blocking attacks, FPs, and performance. One, not so good, way of
evaluating a WAF is to try all sorts of invalid requests, including
trivial payloads, and see if the WAF blocks all of them. This is
overly simplistic as it ignores the motivation of real-world
attacks and the application’s vulnerabilities.
There are also old or obscure attacks on technologies or
versions that are no longer in use, so blocking or allowing such
attacks do not give much information about the WAF capability.
How does Indusface evaluate AppTrana efficacy
As the attack and application landscape changes, the Indusface
security research team continually evaluates its protection to
enhance coverage and improve performance. It includes quickly
reacting to new 0-days, handling attacks like DDOS, and any new
attack techniques.
Included as part of AppTrana
WAF[3] service are a cutting
edge automated scanner and on-demand manual Penetration Testing
service. The expert manual pen testing team evaluates thousands of
real-world sites and is always up-to-date to tackle the latest
threats, tools, and techniques. They also feed this information to
the scanner and AppTrana WAF.
The WAF + PT + automated scanner is a unique and powerful
combination that helps the company evaluate AppTrana WAF from a
real-world standpoint using the same tools and techniques that
attackers use.
Indusface evaluates AppTrana WAF frequently and comprehensively,
including testing for evasions. Integration with the scanner tunes
protection to vulnerabilities safely balancing security, usability,
and performance.
Using Indusface’s AppTrana Managed WAF gives the customer
confidence that protection is being tested, evaluated, and updated
by experts based on attackers’ real-world techniques and tools.
References
Read more http://feedproxy.google.com/~r/TheHackersNews/~3/MTAPHToiWN4/apptrana-managed-cloud-waf.html
