As if the exponential rise in phishing scams and malware attacks
in the last five years wasn’t enough, the COVID-19 crisis has
worsened it further.
The current scenario has given a viable opportunity to
cybercriminals to find a way to target individuals, small and large
enterprises, government corporations.
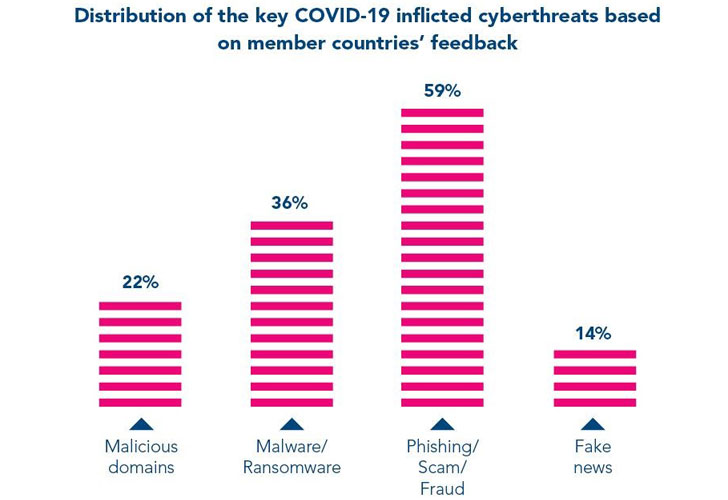
According to Interpol’s COVID-19 Cybercrime Analysis
Report[1], based on the feedback
of 194 countries, phishing/scam/fraud, malware/ransomware,
malicious domains, and fake news have emerged as the biggest
digital threats across the world in the wake of the pandemic.
 |
| Image source: interpol.int |
There are primarily two reasons for emerging cyber threats in
2020:
- Most of the population is working, learning, shopping, or
running their business from home, where they’re using personal
devices from the home/public internet connection, which are usually
unsafe and hence highly vulnerable to cybercrimes. - The cybercriminals are using the COVID-19 theme to exploit
people and enterprises through malicious e-mails and domains. For
example, many scammers have rolled out campaigns offering COVID-19
vaccines, free medical tests and testing kits, tax rebates for
donation to pandemic relief funds, information on COVID-19 cases,
and new job opportunities due to the economic downturn. Some have
even launched fake e-commerce websites selling COVID-19 safety,
health, and sanitization products.
Let’s take a look at a few examples of cyber threats and
security breaches that have taken place in 2020.
Scams
- In April 2020[2], swindlers impersonated
the World Health Organization (WHO) to send e-mails to the public
seeking donations to a fictitious COVID-19 fund. - In March 2020[3], the Department of
Justice in the United States filed a legal appeal in the federal
court to shut down a website called coronavirusmedicalkit[.]com,
which claimed to sell free vaccine kits.
Phishing
- A phishingscam campaign[4]
sent out fake Zoom invites to employees from HR. The idea was to
phish out their passwords. - Several UK citizens[5]
received an e-mail from a fake government ID telling them to claim
a tax refund to protect against the COVID-19 crisis.
Malware
- The Powershell malware attacks in 2020 have witnessed a sharp
increase of 117%[6]
in North America. - Ryuk[7]
has emerged as one of the biggest malware threats to US hospitals
and healthcare providers in 2020.
Ways to Safeguard Against COVID-19 Digital Threats
Cyber risk management calls for both preventive and detective
measures listed below:
1 — Educate Your Staff
Most phishing e-mails appear so legitimate that your employees
are likely to open the attachment or embedded link without
verifying the sender’s e-mail id or the information in the
message’s body.
Create cybersecurity awareness among your employees to help them
identify unauthenticated e-mails. Tell them to double-check the
sender’s e-mail address and look for grammatical errors or unusual
requests. If they suspect anything, they should immediately get in
touch with the IT team instead of forwarding the e-mail to
co-workers.
2 — Encrypt and Backup
Data
You must use full-disk encryption software to encrypt all
sensitive data of your company, customers, and employees.
It is also always a good idea to take a system backup of your
databases, files, and databases at regular intervals.
The general rule of backup is 3-2-1: create at least
three copies, two of which should be on different
mediums (devices/cloud), and one copy should be off-site
for disaster recovery.
3 — Fortify Cybersecurity Policy for
Remote Working
It is crucial to create a strict rulebook for your employees,
laying down the protocol for using home computing devices and
internet connection. They should use a secure internet connection,
avoid the use of office devices for personal use, and store
official files/information only on company storage systems.
Also, make sure that your company implements robust firewall
rules and multi-layer authentication for VPN, critical business
systems, and any other remote network connections. Let your
employees know the company-approved applications and collaboration
tools they have to use.
4 — Use Anti-Virus
Solutions
This may sound like basic security protocol, but it is extremely
important to install sophisticated and trustworthy anti-virus
software on your company servers and devices.
5 — Secure Your Web and Mobile
Applications
With COVID-19 pushing the world to embrace digital on every
front, your web and mobile applications are more at risk from cyber
threats and security violations. Hence, you must proactively
monitor application security risks and take preventive measures to
mitigate them.
You can do so by implementing AppTrana[8], a risk-based, fully
managed application security solution offered by Indusface.
AppTrana provides real-time protection against OWASP exploits, DDOS
attacks, Bot Mitigation, and Zero-Day attacks.
You can also consider Indusface WAS[9], which is a
comprehensive web application vulnerability detection solution. It
provides Automated DAST Scanner combined with on-demand Manual
Penetration Testing[10] and false-positive
removal via manual verification.
If you are looking for mobile security solutions, then Indusface
MAS runs in-depth Pen-testing with multiplatform coverage,
including iOS, Android, and Windows, for vulnerability
detection.
Conclusion
COVID-19 has put the pressing need on organizations to
re-strategize their cybersecurity policy to keep digital threats at
bay.
It is also essential to understand that cyber threats are here
to stay even after the ongoing pandemic because global digital
usage is expected to increase continuously in the coming years.
Hence, it would help if you get prepared on all fronts to combat
the cyber-attacks effectively.
References
- ^
COVID-19
Cybercrime Analysis Report
(www.interpol.int) - ^
April
2020 (www.who.int) - ^
March
2020 (www.justice.gov) - ^
phishingscam campaign
(www.forbes.com) - ^
UK
citizens (www.gov.uk) - ^
117%
(www.mcafee.com) - ^
Ryuk
(thehackernews.com) - ^
AppTrana
(www.indusface.com) - ^
Indusface WAS
(www.indusface.com) - ^
Penetration Testing
(www.indusface.com)
