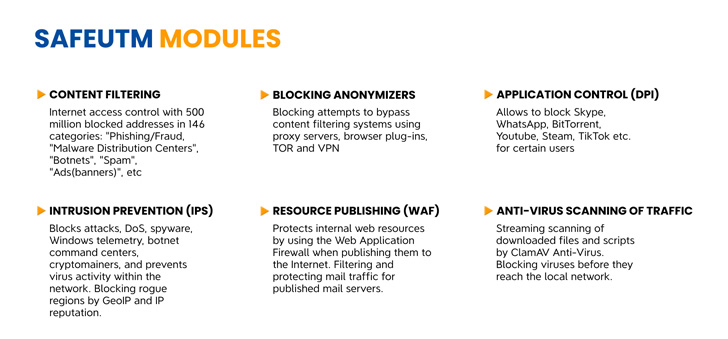
Unified threat management is thought to be a universal solution
for many reasons. First of all, it is compatible with almost any
hardware. As a business or an MSP, you don’t have to bother with
leasing or subleasing expensive equipment. There is no need to
chase your clients to return your costly hardware. The all-in-one
UTM solution will save you money and time & make work routine less
stressful.
However, solely purchasing a sophisticated IT solution might end
up in a waste of money, if the vendor does not tailor it up
specifically for your needs. More troubles occur if your staff does
not have much IT background or simply is not tech-savvy enough.
We put together a compilation of the best use cases of SafeUTM[1]
so you can see how to integrate such a solution into your
infrastructure & help you cut back on unnecessary expenses of all
kinds.
UTM as a lifesaver for enterprise cybersecurity
Large metal industry company of 4,500 users
Among the challenges faced before implementing the solution was
a requirement to have an additional network perimeter protection.
The company was also not receiving enough updates & had poor tech
support for the firewall. We installed SafeUTM as a proxy,
configured content filtering according to corporate standards &
added a built-in web antivirus for additional protection, as the
client requested.
International bank of 2,000 users
Due to a sudden switch to remote & hybrid work mode, the
organization found it hard to keep their cybersecurity layers
strong. They also experienced a downtime due to inoperability of
the solution, and it was crucial to build a distributed
network.
What SafeUTM did was build a VPN network for remote connection
of employees to their workplaces, setting up two-factor
authentication to protect against connecting untrusted users &
site-to-site connection at branch offices via IPSec, and
configuring a fault tolerance cluster.
Large division of a railway company, 2,000 users
Their current solution was way too outdated & desperately needed
replacement. Because such a solution did not meet the game rules of
modern cybersecurity, the company had numerous hacks & other
information security incidents. This caused some misuse of network
resources. Therefore, the entire network configuration was saved
and migrated to the SafeUTM gateway. The use of network bandwidth
was optimized, intrusion prevention system enabled, resulting in
regular requests for unauthorized access to the network.In
addition, we configured application access control in order to
limit the use of unwanted software & corporate email protection
when using SafeUTM gateway as mail relay.
How do smaller organizations benefit with a UTM?
State university of higher education, 500 users
The university had several issues that a UTM could fix: content
filter base was only relevant to English-speaking users, filtering
settings for different user groups were not flexible or
customizable. There were attacks on the published web resource &
the organization did not own a mail server. Respectively, we
configured content filtering using a base relevant to the languages
spoken in the area & based on AD security groups. Web resource was
published through reverse proxy, preconfigured WAF was enabled, and
HTTP requests redirected. As to the mail issue, we configured the
mail server at SafeUTM using integrated filtering and anti-spam
lists.
Small trading company of 200 users
The company had used a generic router to protect the perimeter,
which was not efficeint at all. In addition to that, there was no
reporting system & no ability to update solution settings against
modern threats due to a heavy workload of the system administrator.
What SafeUTM did was configuring modules of content filtering,
application control, intrusion prevention system with automatic
updating of filtering databases & automatic collection and sending
of reports on the passed traffic. As we do for any other client, we
provided all necessary assistance in configuring and implementing
the solution during the pilot phase.
A UTM solution in today’s circumstances is definitely the right
choice for a company that is aware of all the ways lack of
cybersecurity might lead. Feel free to chat with our UTM engineers[2] to learn how exactly
such a solution can be tailored up for your specific case.
References
- ^
SafeUTM
(www.promo.safedns.com) - ^
chat
with our UTM engineers
(www.promo.safedns.com)
Read more https://thehackernews.com/2022/09/how-to-use-utm-solution-win-time-money.html