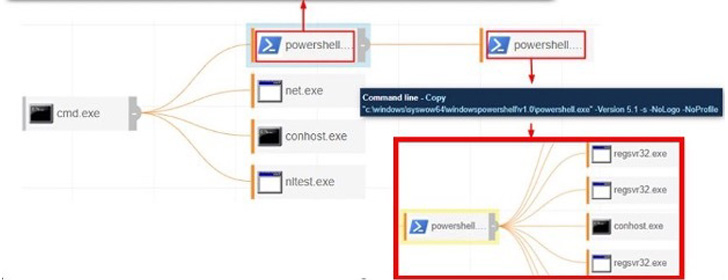
The attack infrastructure used to target Cisco[1]
in the May 2022 incident was also employed against an attempted
compromise of an unnamed workforce management solutions holding
company a month earlier in April 2022.
Cybersecurity firm Sentire, which disclosed[2]
the findings, raised the possibility that the intrusions could be
the work of a criminal actor known as mx1r, who is said to be a
member of the Evil Corp affiliate cluster dubbed UNC2165[3].
Evil Corp, the progenitors of the infamous Dridex banking
trojan, have, over the years, refined their modus operandi to run a
series of ransomware operations to sidestep sanctions imposed by
the U.S. Treasury in December 2019.
Initial access to the company’s IT network was made possible by
using stolen Virtual Private Network (VPN) credentials, followed by
leveraging off-the-shelf tools for lateral movement and gaining
deeper access into the victim’s environment.
“Using Cobalt Strike, the attackers were able to gain an initial
foothold and hands-on-actions were immediate and swift from the
time of initial access to when the attacker was able to register
their own Virtual Machine on the victim’s VPN network,” eSentire
noted.
mx1r’s ties to UNC2165 stems from overlaps in tactics and
techniques with that of UNC2165, including staging a Kerberoasting attack[4]
against the Active Directory service and the use of Remote Desktop
Protocol (RDP) access for propagating within the company’s
network.
The connections notwithstanding, the Cobalt Strike “HiveStrike”
infrastructure used to mount the attack is said to match that of a
Conti ransomware[5]
affiliate previously known to deploy Hive and Yanluowang[6]
strains, the latter of which has since posted files stolen from the
Cisco breach in late May 2022 to its data leak site.
The networking equipment maker attributed the incident to an
initial access broker (IAB) with links to three different
collectives: UNC2447[7], LAPSUS$[8], and Yanluowang ransomware[9].
“It seems unlikely — but not impossible — that Conti would
lend its infrastructure to Evil Corp,” eSentire said. In light of
UNC2165’s recent pivot to LockBit ransomware, the company said “it
is more plausible that the Evil Corp affiliate/UNC2165 may be
working with one of Conti’s new subsidiaries.”
“It’s also possible that initial access was brokered by an Evil
Corp affiliate but ultimately sold off to Hive operators and its
affiliates,” it further added.
References
- ^
target
Cisco (thehackernews.com) - ^
disclosed
(www.esentire.com) - ^
UNC2165
(thehackernews.com) - ^
Kerberoasting attack
(www.crowdstrike.com) - ^
Conti
ransomware (thehackernews.com) - ^
Hive and
Yanluowang (www.esentire.com) - ^
UNC2447
(thehackernews.com) - ^
LAPSUS$
(thehackernews.com) - ^
Yanluowang ransomware
(symantec-enterprise-blogs.security.com)
Read more https://thehackernews.com/2022/09/infra-used-in-cisco-hack-also-targeted.html