operating system, you need to be extra careful and avoid
downloading any “.desktop” or “.directory” file for a while.
A cybersecurity researcher has disclosed an unpatched zero-day
vulnerability in the KDE software framework that could allow
maliciously crafted .desktop and .directory files to silently run
arbitrary code on a user’s computer—without even requiring the
victim to actually open it.
KDE Plasma is one of the most popular open-source widget-based
desktop environment for Linux users and comes as a default desktop
environment on many Linux distributions, such as Manjaro, openSUSE,
Kubuntu, and PCLinuxOS.
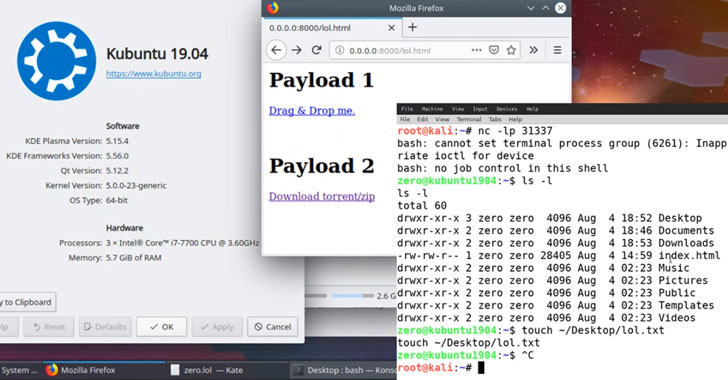
Security researcher Dominik Penner who discovered the
vulnerability contacted The Hacker News, informing that there’s a
command injection vulnerability in KDE 4/5 Plasma desktop due to
the way KDE handles .desktop and .directory files.
“When a .desktop or .directory file is instantiated, it unsafely
evaluates environment variables and shell expansions using
KConfigPrivate::expandString() via the KConfigGroup::readEntry()
function,” Penner
said[1].
Exploiting this flaw, which affects KDE Frameworks package 5.60.0
and below, is simple and involves some social engineering as an
attacker would need to trick KDE user into downloading an archive
containing a malicious .desktop or .directory file.
“Using a specially crafted .desktop file a remote user could be
compromised by simply downloading and viewing the file in their
file manager, or by dragging and dropping a link of it into their
documents or desktop,” the researcher explained.
“Theoretically, if we can control config entries and trigger
their reading, we can achieve command injection / RCE.”
vulnerability along with two videos that successfully demonstrate
the attack scenarios exploiting the KDE KDesktopFile Command
Injection vulnerability.
Apparently, the researcher did not report the vulnerability to the
KDE developers before publishing the details and PoC exploits, said
KDE Community while acknowledging the vulnerability and assuring
users that a fix is on its way.
“Also, if you discover a similar vulnerability, it is best to send
an email security@kde.org before making it public. This will give
us time to patch it and keep users safe before the bad guys try to
exploit it,” KDE Community said.
downloading .desktop or .directory files and extracting archives
from untrusted sources,” for a while until the vulnerability gets
patched.
References
- ^
Penner said
(gist.githubusercontent.com)
Read more http://feedproxy.google.com/~r/TheHackersNews/~3/O1lNoV_h2bI/kde-desktop-linux-vulnerability.html