Encrypt is going to revoke more than 3 million TLS certificates
within the next 24 hours that may have been issued wrongfully due
to a bug in its Certificate Authority software.
The bug, which Let’s Encrypt confirmed[1]
on February 29 and was fixed two hours after discovery, impacted
the way it checked the domain name ownership before issuing new TLS
certificates.
As a result, the bug opened up a scenario where a certificate
could be issued even without adequately validating the holder’s
control of a domain name.
The Certification
Authority Authorization (CAA), an internet security policy,
allows domain name holders to indicate to certificate authorities
(CAs) whether or not they are authorized to issue digital
certificates for a specific domain name.
[2]
Let’s Encrypt considers domain validation results good only for 30
days from the time of validation, after which it rechecks the CAA
record authorizing that domain before issuing the certificate. The
bug — which was uncovered in the code for Boulder, the certificate
signing software used by Let’s Encrypt — is as follows:
“When a certificate request contained N domain names that needed
CAA rechecking, Boulder would pick one domain name and check it N
times.” In other words, when Boulder needed to parse, for example,
a group of 5 domains names that required CAA rechecking, it would
check one domain name 5 times as opposed to checking each of the 5
domains once.
in July 2019.
This means that Let’s Encrypt might have issued certificates
that it shouldn’t have in the first place, as a result of which
it’s revoking all the TLS certificates that were affected by the
bug.
The development comes as Let’s Encrypt project announced last
week that it had issued its one-billionth free
TLS certificate[3]
since its launch in 2015.
approximately 116 million active certificates are affected — about
3,048,289 — out of which about one million are duplicates of other
affected certificates.
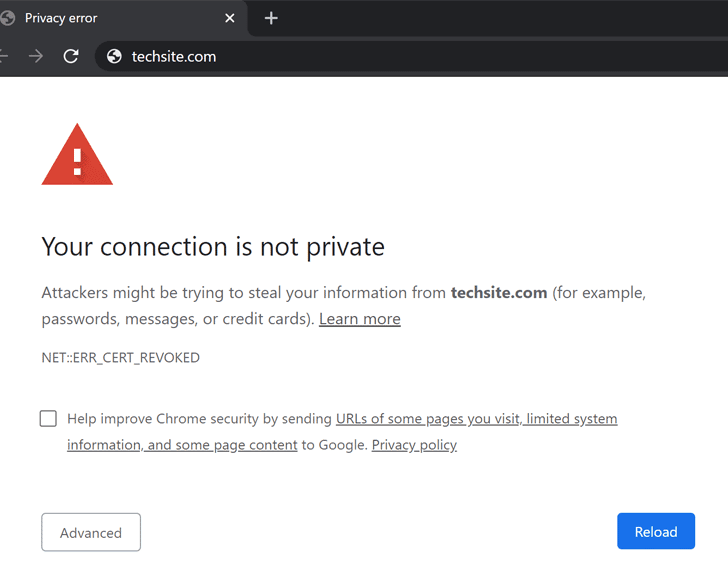
Affected website owners have until 8PM UTC (3PM EST) March 4 to
manually renew and
replace their certificates, failing which visitors to the
websites will be greeted with TLS security warnings — as the
certificates are revoked — until the renewal process is complete.
It’s worth noting that the certificates issued by Let’s Encrypt
are valid for a period of 90 days, and ACME clients such as Certbot
are capable of automatically renewing them.
But with Let’s Encrypt revoking all impacted certificates,
website admins will have to perform a forced renewal to prevent any
interruptions.
Besides using the tool https://checkhost.unboundtest.com/[6] to check if a
certificate needs replacement, Let’s Encrypt has put together a
downloadable list
of affected serial numbers[7], allowing subscribers to
check if their websites rely on an affected certificate.
References
- ^
confirmed
(community.letsencrypt.org) - ^
Certification Authority
Authorization (en.wikipedia.org) - ^
one-billionth free TLS certificate
(thehackernews.com) - ^
2.6 percent
(community.letsencrypt.org) - ^
manually renew and replace their
certificates (certbot.eff.org) - ^
https://checkhost.unboundtest.com/
(checkhost.unboundtest.com) - ^
downloadable list of affected serial
numbers (letsencrypt.org)