security vulnerabilities in Intel processors, as well as to the
endless ‘performance killing’ patches that resolve them.
Modern Intel CPUs have now been found vulnerable to a new attack
that involves reversely exploiting Meltdown-type data leak
vulnerabilities to bypass existing defenses, two separate teams of
researchers told The Hacker News.
Tracked as CVE-2020-0551, dubbed “Load Value
Injection in the Line Fill Buffers” or LVI-LFB for
short, the new speculative-execution attack could let a less
privileged attacker steal sensitive information—encryption keys or
passwords—from the protected memory and subsequently, take
significant control over a targeted system.
According to experts at Bitdefender[1]
and academic
researchers[2] from a couple of
universities, the new attack is particularly devastating in
multi-tenant environments such as enterprise workstations or cloud
servers in the datacenter.
And, that’s because a less-privileged rouge tenant could exploit
this issue to leak sensitive information from a more privileged
user or from a different virtualized environment on top of the
hypervisor.
Intel CPUs ‘Load Value Injection’ Vulnerability
Unlike previously disclosed Intel chipset vulnerabilities—including
Meltdown,
Spectre[3], and MDS[4]—where an attacker
speculatively accesses the memory or sniffs the data when the
victim accesses it, the new LVI-LFB attack involves attacker
injecting malicious data into the buffers that victim program
unwillingly uses during the speculative execution.
“The attacker sprays the LFBs with the address of a malicious
function, and when the victim issues an indirect branch through
memory which requires a microcode assist, the address of the
malicious function is loaded from the LFBs, thus leading to the
attacker function being speculatively executed,” Bitdefender
researchers told The Hacker News.
mitigated with existing patches for previously disclosed Meltdown,
Foreshadow[5], ZombieLoad[6], RIDL, or Fallout
speculative-execution attacks.
“It combines Spectre-style code gadgets in the victim application
with Meltdown-type illegal data flow from faulting or assisted
memory load instructions to bypass existing defenses and inject
attacker-controlled data into a victim’s transient execution,” the
researcher Jo Van Bulck and his team said in a detailed
paper.
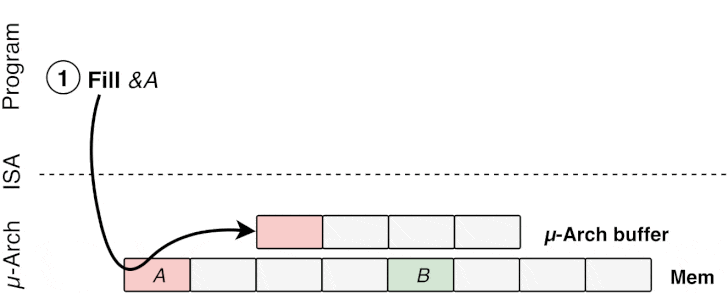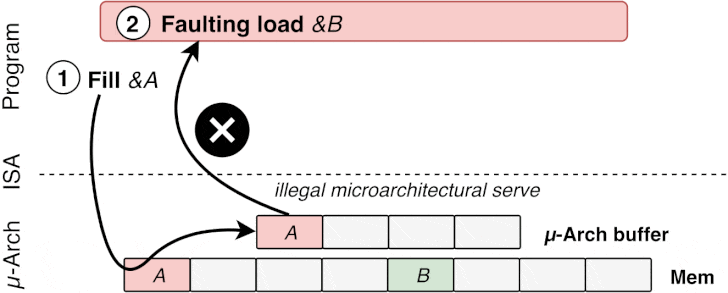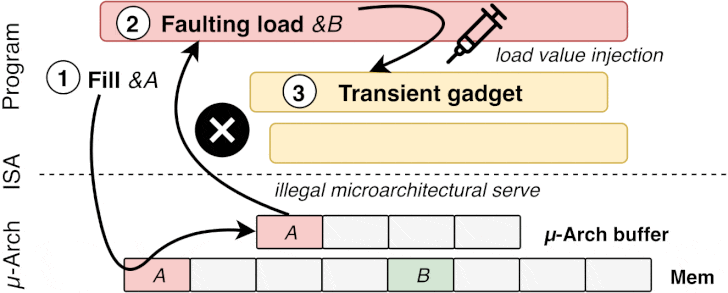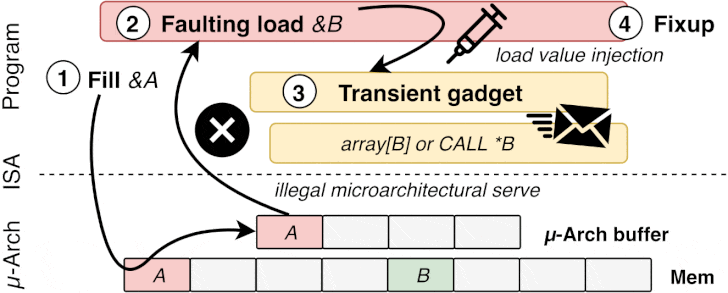
in 4 simple steps:
- Poison a hidden processor buffer with attacker values,
- Induce faulting or assisted load in the victim program,
- The attacker’s value is transiently injected into code gadgets
following the faulting load in the victim program, - Side channels may leave secret-dependent traces before the
processor detects the mistake and rolls back all operations.
In other words, when the victim actively tries to execute some
code, the attacker can actively fill the MDS buffers with carefully
chosen values to influence the execution of the victim’s thread.
PoC Exploit Demo and Security Patches
According to the researchers, there are several possible scenarios
to exploit the LVI-LFB based control flow hijacking attack, such
as: influencing an address that is accessed, the offset within an
accessed buffer, the result of a conditional branch, or affecting
the destination of an indirect branch.
“LVI based control flow hijacking allows an attacker to trick the
victim into speculatively executing a function of his choosing.
This works, theoretically, across all security boundaries: process
to process, user-mode to kernel-mode, guest-mode to root-mode, and
perhaps even user-mode to enclave,” Bitdefender researchers said.
Both teams of researchers have also developed proof-of-concept
exploits[7], one of which could let
attackers compromise the security of Intel SGX enclaves is now
available on
GitHub[8].
Though researchers haven’t tested AMD or ARM processors, they
hinted “in principle, any processor that is vulnerable to
Meltdown-type data leakage would also be vulnerable to LVI-style
data injection.”
Jo Van Bulck led team reported this flaw to the Intel team
almost a year ago, whereas Bitdefender reported it just last month
immediately after discovering it independently.
Intel has acknowledged these findings and today released a list
of all affected products on its website along with the information
on microcode security patch updates.
However, since the hardware flaws cannot be eradicated with
software patches and flushing affected buffers are no longer
sufficient, researchers suggest affected users to either disable
rich performance features like hyper-threading, or replace the
hardware to completely avoid such vulnerabilities.
References
- ^
Bitdefender
(www.bitdefender.com) - ^
academic researchers
(lviattack.eu) - ^
Meltdown, Spectre
(thehackernews.com) - ^
MDS
(thehackernews.com) - ^
Foreshadow
(thehackernews.com) - ^
ZombieLoad
(thehackernews.com) - ^
proof-of-concept exploits
(github.com) - ^
available on GitHub
(github.com)
Read more http://feedproxy.google.com/~r/TheHackersNews/~3/wo34EcDLabQ/intel-load-value-injection.html