A new strain of Android malware has been spotted in the wild
targeting online banking and cryptocurrency wallet customers in
Spain and Italy, just weeks after a coordinated law enforcement
operation dismantled FluBot[1].
The information stealing trojan, codenamed
MaliBot by F5 Labs, is as feature-rich as its
counterparts[2], allowing it to steal
credentials and cookies, bypass multi-factor authentication (MFA)
codes, and abuse Android’s Accessibility Service to monitor the
victim’s device screen.
MaliBot is known to primarily disguise itself as cryptocurrency
mining apps such as Mining X or The CryptoApp that are distributed
via fraudulent websites designed to attract potential visitors into
downloading them.
It also takes another leaf out of the mobile banking trojan
playbook in that it employs smishing as a distribution vector to
proliferate the malware by accessing an infected smartphone’s
contacts and sending SMS messages containing links to the
malware.
“MaliBot’s command-and-control (C2) is in Russia and appears to
use the same servers that were used to distribute the Sality malware[3],” F5 Labs researcher Dor
Nizar said[4]. “It is a heavily
modified re-working of the SOVA malware, with different
functionality, targets, C2 servers, domains, and packing
schemes.”
SOVA (meaning “Owl” in Russian), which was first detected in August 2021[5], is notable for its
ability to conduct overlay attacks, which work by displaying a
fraudulent page using WebView with a link provided by the C2 server
should a victim open a banking app included in its active target
list.
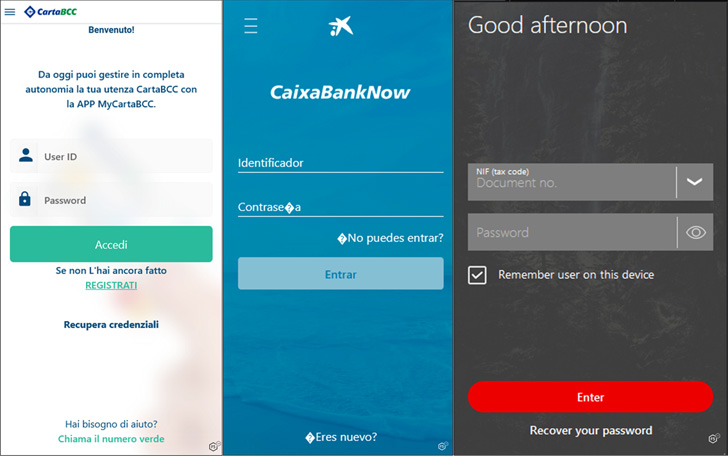
Some of the banks targeted by MaliBot using this approach
include UniCredit, Santander, CaixaBank, and CartaBCC.
Accessibility Service is a background service running in Android
devices to assist users with disabilities. It has long been
leveraged by spyware and trojans[6] to capture the device
contents and intercept credentials entered by unsuspecting users on
other apps.
Besides being able to siphon passwords and cookies of the
victim’s Google account, the malware is designed to swipe 2FA codes
from the Google Authenticator app as well as exfiltrate sensitive
information such as total balances and seed phrases from Binance
and Trust Wallet apps.
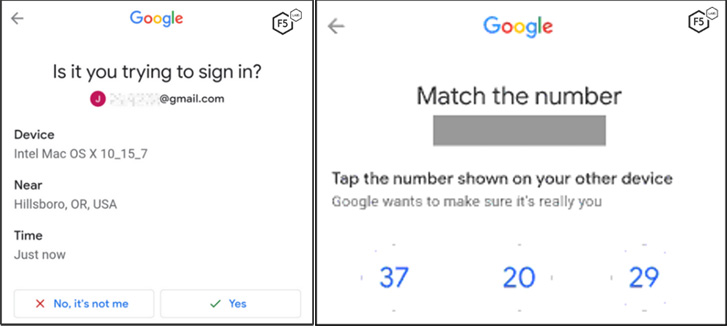
What’s more, Malibot is capable of weaponizing its access to the
Accessibility API to defeat Google’s two-factor authentication
(2FA) methods, such as Google prompts[7], even in scenarios where
an attempt is made to sign in to the accounts using the stolen
credentials from a previously unknown device.
“The versatility of the malware and the control it gives
attackers over the device mean that it could, in principle, be used
for a wider range of attacks than stealing credentials and
cryptocurrency,” the researchers said.
“In fact, any application which makes use of WebView is liable
to having the users’ credentials and cookies stolen.”
References
- ^
FluBot
(thehackernews.com) - ^
counterparts
(thehackernews.com) - ^
Sality
malware (malpedia.caad.fkie.fraunhofer.de) - ^
said
(www.f5.com) - ^
first
detected in August 2021 (thehackernews.com) - ^
leveraged by spyware and trojans
(thehackernews.com) - ^
Google
prompts (support.google.com)
Read more https://thehackernews.com/2022/06/malibot-new-android-banking-trojan.html