Infection chains associated with the multi-purpose Qakbot
malware have been broken down into “distinct building blocks,” an
effort that Microsoft said will help to detect and block the threat
in an effective manner proactively.
The Microsoft 365 Defender Threat Intelligence Team dubbed[1]
Qakbot a “customizable chameleon that adapts to suit the
needs of the multiple threat actor groups that utilize it.”
Qakbot[2]
is believed to be the creation of a financially motivated
cybercriminal threat group known as Gold Lagoon[3]. It is a prevalent
information-stealing malware that, in recent years, has become a
precursor to many critical and widespread ransomware attacks,
offering a malware installation-as-a-service that enables many
campaigns.
First discovered in 2007, the modular malware — like TrickBot[4]
— has evolved[5]
from its early roots as a banking trojan to become a Swiss Army
knife capable of data exfiltration and acting as a delivery
mechanism for the second stage payloads, including ransomware. Also
notable is its tactic of hijacking victims’ legitimate email
threads from Outlook clients via an Email Collector component and
using those threads as phishing lures to infect other machines.
“Compromising IMAP services and email service providers (ESPs),
or hijacking email threads allows attackers to leverage the trust a
potential victim has in people they have corresponded with before,
and it also allows for the impersonation of a compromised
organization,” Trend Micro researchers Ian Kenefick and Vladimir
Kropotov detailed[6]
last month. “Indeed, intended targets will be much more likely to
open emails from a recognized sender.”
Qakbot activity tracked by the cybersecurity firm over a seven
month period between March 25, 2021, and October 25, 2021, show
that the U.S., Japan, Germany, India, Taiwan, Italy, South Korea,
Turkey, Spain, and France are the top targeted countries, with the
intrusions primarily striking telecommunications, technology, and
education sectors.
More recently, spam campaigns have resulted in the deployment of
a new loader called SQUIRRELWAFFLE[7]
that enables the attackers to gain an initial foothold into
enterprise networks and drop malicious payloads, such as Qakbot and
Cobalt Strike, on infected systems.
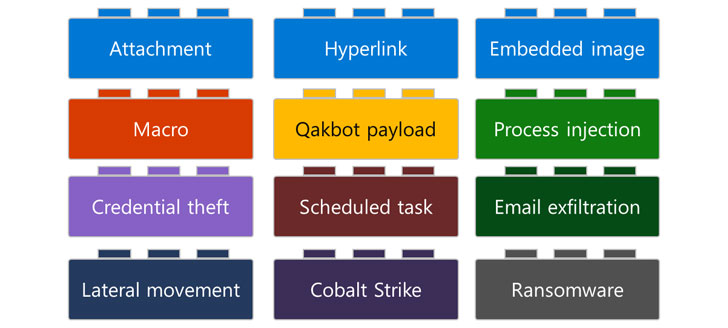
Now according to Microsoft, the attack chains involving Qakbot
comprise of several building blocks that chart the various stages
of the compromise, right from the methods adopted to distribute the
malware — links, attachments, or embedded images[8]
— before carrying out an array of post-exploitation activities such
as credential theft, email exfiltration, lateral movement, and the
deployment of Cobalt Strike beacons and ransomware.
The Redmond-based company noted that Qakbot-related emails sent
by the attackers may, at times, come with a ZIP archive file
attachment that includes a spreadsheet containing Excel 4.0 macros[9], an initial access
vector that’s widely abused in phishing attacks. Regardless of the
mechanism employed to deliver the malware, the campaigns have in
common their use of malicious Excel 4.0 macros.
While macros are turned off by default in Microsoft Office,
recipients of the email messages are prompted to enable the macro
to view the document’s actual content. This triggers the next phase
of the onslaught to download the malicious payloads from one or
more attacker-controlled domains.
More often than not, Qakbot is just the first step in what’s
part of a larger attack, with the threat actors using the initial
foothold facilitated by the malware to install additional payloads
or sell the access to the highest bidder on underground forums who
can then leverage it for their own ends. In June 2021, enterprise
security company Proofpoint revealed[10] how ransomware actors
are increasingly shifting from using email messages as an intrusion
route to purchasing access from cybercriminal enterprises that have
already infiltrated major entities.
“Qakbot’s modularity and flexibility could pose a challenge for
security analysts and defenders because concurrent Qakbot campaigns
could look strikingly different on each affected device,
significantly impacting how these defenders respond to such
attacks,” the researchers said. “Therefore, a deeper understanding
of Qakbot is paramount in building a comprehensive and coordinated
defense strategy against it.”
References
- ^
dubbed
(www.microsoft.com) - ^
Qakbot
(thehackernews.com) - ^
Gold
Lagoon (www.secureworks.com) - ^
TrickBot
(thehackernews.com) - ^
evolved
(thehackernews.com) - ^
detailed
(www.trendmicro.com) - ^
SQUIRRELWAFFLE
(thehackernews.com) - ^
embedded
images (www.inky.com) - ^
Excel
4.0 macros (thehackernews.com) - ^
revealed
(thehackernews.com)
Read more https://thehackernews.com/2021/12/microsoft-details-building-blocks-of.html