Microsoft on Wednesday disclosed details of a now-patched “high
severity vulnerability” in the TikTok app for Android that could
let attackers take over accounts when victims clicked on a
malicious link.
“Attackers could have leveraged the vulnerability to hijack an
account without users’ awareness if a targeted user simply clicked
a specially crafted link,” Dimitrios Valsamaras of the Microsoft
365 Defender Research Team said[1]
in a write-up.
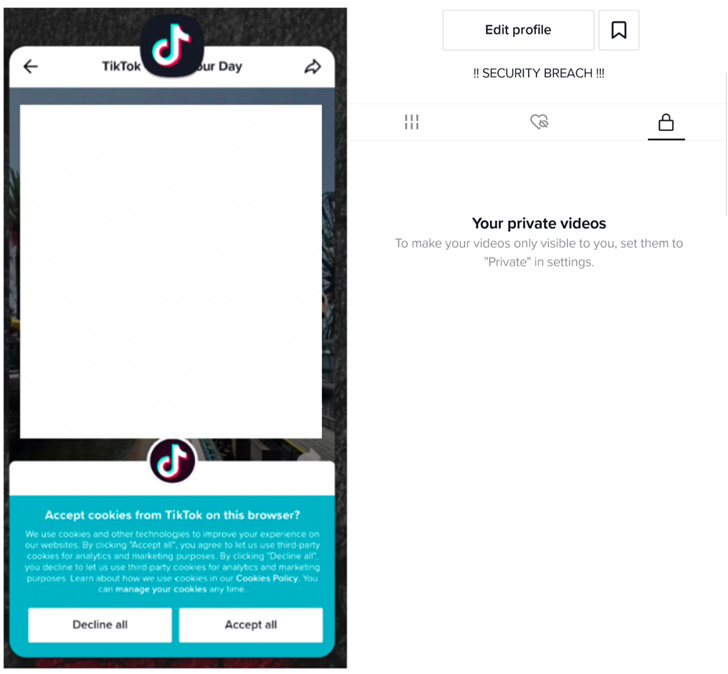
Successful exploitation of the flaw could have permitted
malicious actors to access and modify users’ TikTok profiles and
sensitive information, leading to the unauthorized exposure of
private videos. Attackers could also have abused the bug to send
messages and upload videos on behalf of users.
The issue, addressed in version 23.7.3, impacts two flavors of
its Android app com.ss.android.ugc.trill (for East and Southeast
Asian users) and com.zhiliaoapp.musically (for users in other
countries except for India, where it’s banned). Combined, the apps
have more than 1.5 billion installations between them.
Tracked as CVE-2022-28799[2]
(CVSS score: 8.8), the vulnerability has to do with the app’s
handling of what’s called a deeplink, a special hyperlink that
allows apps to open a specific resource within another app
installed on the device rather than directing users to a
website.
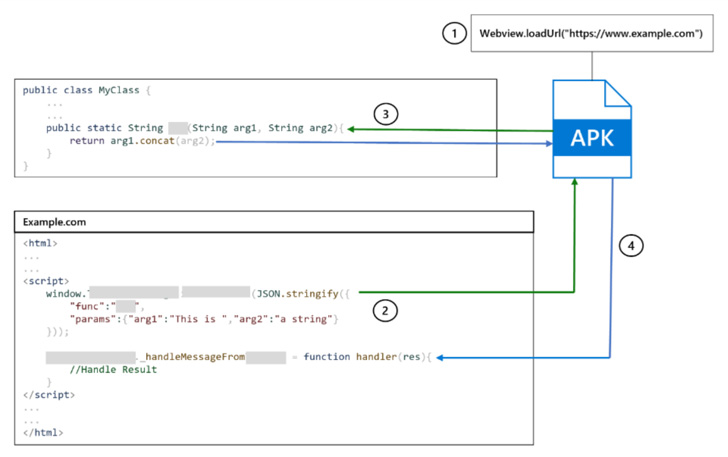
“A crafted URL (unvalidated deeplink) can force the
com.zhiliaoapp.musically WebView to load an arbitrary website,”
according to an advisory for the flaw. “This may allow an attacker
to leverage an attached JavaScript interface for the takeover with
one click.”
Put simply, the flaw makes it possible to circumvent the apps’s
restrictions to reject untrusted hosts and load any website of the
attacker’s choice through the Android System WebView[3], a mechanism to display
web content on other apps.
“The filtering takes place on the server-side and the decision
to load or reject a URL is based on the reply received from a
particular HTTP GET request,” Valsamaras explained, adding the
static analysis “indicated that it is possible to bypass the
server-side check by adding two additional parameters to the
deeplink.”
A consequence of this exploit designed to hijack WebView to load
rogue websites is that it could permit the adversary to invoke over
70 exposed TikTok endpoints, effectively compromising a user’s
profile integrity. There’s no evidence that the bug has been
weaponized in the wild.
“From a programming perspective, using JavaScript interfaces[4]
poses significant risks,” Microsoft noted. “A compromised
JavaScript interface can potentially allow attackers to execute
code using the application’s ID and privileges.”
References
- ^
said
(www.microsoft.com) - ^
CVE-2022-28799
(nvd.nist.gov) - ^
WebView
(developer.android.com) - ^
JavaScript interfaces
(thehackernews.com)
Read more https://thehackernews.com/2022/09/microsoft-discover-severe-one-click.html