At least six different Russia-aligned actors launched no less
than 237 cyberattacks against Ukraine from February 23 to April 8,
including 38 discrete destructive attacks that irrevocably
destroyed files in hundreds of systems across dozens of
organizations in the country.
“Collectively, the cyber and kinetic actions work to disrupt or
degrade Ukrainian government and military functions and undermine
the public’s trust in those same institutions,” the company’s
Digital Security Unit (DSU) said[1]
in a special report.
The major malware families that have been leveraged for
destructive activity as part of Russia’s relentless digital
assaults include: WhisperGate[2], HermeticWiper[3]
(FoxBlade[4]
aka KillDisk), HermeticRansom[5]
(SonicVote), IssacWiper[6]
(Lasainraw), CaddyWiper[7], DesertBlade[8], DoubleZero[9]
(FiberLake), and Industroyer2[10].
WhisperGate, HermeticWiper, IssacWiper, and CaddyWiper are all
data wipers designed to overwrite data and render machines
unbootable, while DoubleZero is a .NET malware capable of data
deletion. DesertBlade, also a data wiper, is said to have been
launched against an unnamed broadcasting company in Ukraine on
March 1.
SonicVote, on the other hand, is a file encryptor detected in
conjunction with HermeticWiper to disguise the intrusions as a
ransomware attack, while Industroyer2 specifically targets
operational technology to sabotage critical industrial production
and processes.
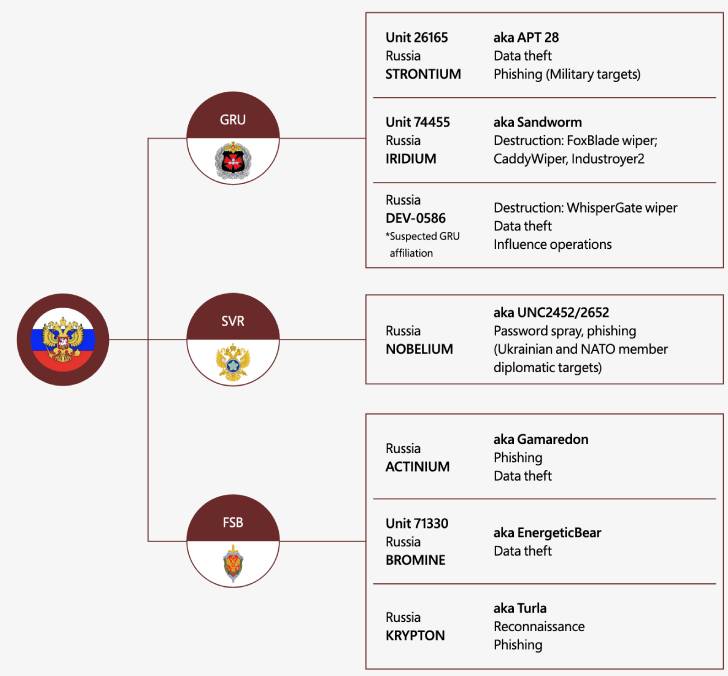
Microsoft attributed HermeticWiper, CaddyWiper, and Industroyer2
with moderate confidence to a Russian state-sponsored actor named
Sandworm[11] (aka Iridium). The
WhisperGate attacks have been tied to a previously unknown cluster
dubbed DEV-0586, which is believed to be affiliated to Russia’s
GRU military intelligence[12].
32% of the total 38 destructive attacks are estimated to have
singled out Ukrainian government organizations at the national,
regional and city levels, with over 40% of the attacks aimed at
organizations in critical infrastructure sectors in the
nations.
In addition, Microsoft said it observed Nobelium[13], the threat actor
blamed for the 2020 SolarWinds supply chain attack, attempting to
breach IT firms serving government customers in NATO member states,
using the access to siphon data from Western foreign policy
organizations.
Other malicious attacks involve phishing campaigns targeting
military entities (Fancy Bear[14] aka Strontium) and
government officials (Primitive Bear[15] aka Actinium[16]) as well as data theft
(Energetic Bear[17] aka Bromine) and
reconnaissance (Venomous Bear[18] aka Krypton)
operations.
“Russia’s use of cyberattacks appears to be strongly correlated
and sometimes directly timed with its kinetic military operations
targeting services and institutions crucial for civilians,” Tom
Burt, corporate vice president of customer security and trust,
said[19].
“Given Russian threat actors have been mirroring and augmenting
military actions, we believe cyberattacks will continue to escalate
as the conflict rages. It’s likely the attacks we’ve observed are
only a fraction of activity targeting Ukraine.”
References
- ^
said
(query.prod.cms.rt.microsoft.com) - ^
WhisperGate
(thehackernews.com) - ^
HermeticWiper
(thehackernews.com) - ^
FoxBlade
(thehackernews.com) - ^
HermeticRansom
(thehackernews.com) - ^
IssacWiper
(thehackernews.com) - ^
CaddyWiper
(thehackernews.com) - ^
DesertBlade
(www.microsoft.com) - ^
DoubleZero
(thehackernews.com) - ^
Industroyer2
(thehackernews.com) - ^
Sandworm
(thehackernews.com) - ^
GRU
military intelligence (thehackernews.com) - ^
Nobelium
(thehackernews.com) - ^
Fancy
Bear (thehackernews.com) - ^
Primitive Bear
(thehackernews.com) - ^
Actinium
(thehackernews.com) - ^
Energetic Bear
(thehackernews.com) - ^
Venomous Bear
(thehackernews.com) - ^
said
(blogs.microsoft.com)
Read more https://thehackernews.com/2022/04/microsoft-documents-over-200.html