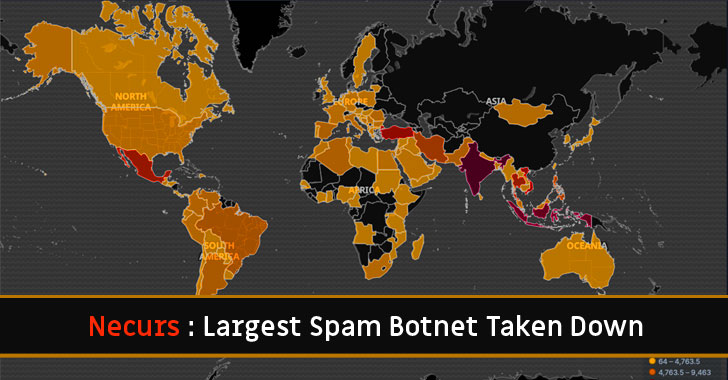
the botnet network of the Necurs malware, which has infected more
than 9 million computers globally, and also hijacked the majority
of its infrastructure.
The latest botnet takedown was the result of a coordinated
operation involving international police and private tech companies
across 35 countries.
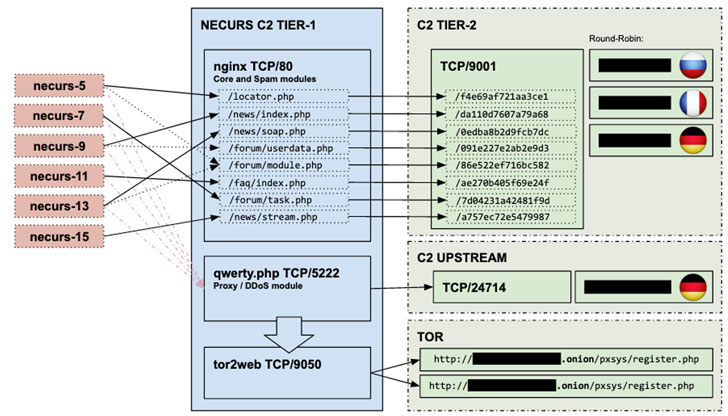
The operation was conducted successfully after researchers
successfully broke the domain generation algorithm (DGA)
implemented by the Necurs malware, which helped it remain resilient
for a long time.
DGA is basically a technique to unpredictably generate new domain
names at regular intervals, helping malware authors to continuously
switch the location of C&C servers and maintain undisrupted
digital communication with the infected machines.
“We were then able to accurately predict over six million unique
domains that would be created in the next 25 months. Microsoft
reported these domains to their respective registries in countries
around the world so the websites can be blocked and thus prevented
from becoming part of the Necurs infrastructure,” Microsoft
said[1].
Additionally, with the help of court orders, Microsoft has also
obtained control over the U.S.-based infrastructure Necurs uses to
distribute malware and infect victim computers.
to register new ones, we have significantly disrupted the botnet.”
First detected in 2012, Necurs is one of the world’s most
prolific spam botnet that infects systems with banking
malware[2], cryptojacking
malware[3] and ransomware,
and then further abuses them to send out massive amounts of spam
emails to new victims.
To avoid detection and maintain persistence on targeted
computers, Necurs utilizes its kernel-mode rootkit that disables a
large number of security applications, including Windows
Firewall.
Necurs was noticed mainly in 2017 when it started spreading
Dridex and Locky
ransomware at the rate of 5 million emails per hour to
computers across the globe.
[4]
“From 2016 to 2019, it was the most prominent method to deliver
spam and malware by criminals and was responsible for 90% of the
malware spread by email worldwide,” researchers at BitSight[5] said in a separate
report published today.
“During 58 days of investigation, for example, we observed that
one Necurs-infected computer sent a total of 3.8 million spam
emails to over 40.6 million potential victims,” Microsoft said.
In some cases, the attackers even started blackmailing victims
for a ransom claiming that they have knowledge of their
extramarital affairs and threatened to send proof to the victim’s
spouse, family, friends, and co-workers.
According to the latest stats published by researchers, India,
Indonesia, Turkey, Vietnam, Mexico, Thailand, Iran, the
Philippines, and Brazil are the top countries that have been hit by
the Necurs malware.
References
- ^
Microsoft said
(blogs.microsoft.com) - ^
banking malware
(thehackernews.com) - ^
cryptojacking malware
(thehackernews.com) - ^
Locky ransomware
(thehackernews.com) - ^
BitSight
(www.bitsight.com)
Read more http://feedproxy.google.com/~r/TheHackersNews/~3/44ubAc5lyOY/necurs-botnet-takedown.html