uncovering forensic evidence of sabotage on Linux systems,
including rootkits and intrusive malware that may otherwise go
undetected.
The cloud offering, dubbed Project
Freta[1], is a snapshot-based
memory forensic mechanism that aims to provide automated
full-system volatile memory inspection of virtual machine (VM)
snapshots, with capabilities to spot malicious software, kernel
rootkits[2], and other stealthy
malware techniques such as process
hiding[3].
The project is named after Warsaw’s Freta Street,
the birthplace of Marie Curie, the famous French physicist who
brought X-ray medical
imaging to the battlefield during World War I.
[4][5]
“Modern malware is complex, sophisticated, and designed with
non-discoverability as a core tenet,” said Mike Walker, Microsoft’s
senior director of New Security Ventures. “Project Freta intends to
automate and democratize VM forensics to a point where every user
and every enterprise can sweep volatile memory for unknown malware
with the push of a button — no setup required.”
The objective is to infer the presence of malware from memory,
at the same time gain the upper hand in the fight against threat
actors who deploy and reuse stealthy malware on target systems for
ulterior motives, and more importantly, render evasion infeasible
and increase the development cost of undiscoverable cloud
malware.
different aspects that would make systems immune to such attacks in
the first place by preventing any program from:
- Detecting the presence of a security sensor prior to installing
itself - Residing in an area that’s out of view of the sensor
- Detecting the sensor’s operation and accordingly erasing or
modifying itself to escape detection, and - Tampering with the sensor’s functions to cause sabotage
“When attackers and defenders share a microarchitecture, every
detection move a defender makes disturbs the environment in a way
that is eventually discoverable by an attacker invested in
secrecy,” Walker noted. “The only way to discover such attackers is
to remove their insight into defense.”
Open to anyone with a Microsoft Account (MSA) or Azure Active
Directory (AAD) account, Project Freta lets users submit memory
images (.vmrs, .lime, .core, or .raw files) via an online portal or
an API, post
which a detailed report is generated that delves into different
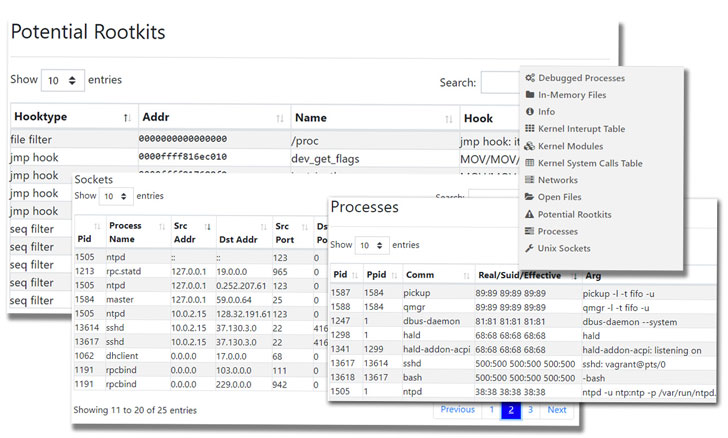
sections (kernel modules, in-memory files, potential rootkits,
processes, and more) that can be exported via JSON format.
[6]
Microsoft said it focused on Linux due to the need for
fingerprinting operating systems in the cloud in a
platform-agnostic manner from a scrambled memory image. The
increased complexity is given the large number of publicly
available kernels for Linux. This initial release version of
Project Freta supports over 4,000 Linux kernels, with Windows
support in the pipeline.
It’s also in the process of adding a sensor capability that
allows users to migrate the volatile memory of live VMs to an
offline environment for further analysis and more AI-based
decision-making tools for threat detection.
“The goal of this democratization effort is to increase the
development cost of undiscoverable cloud malware toward its
theoretical maximum,” Walker said. “Producers of stealthy malware
would then be locked into an expensive cycle of complete
re-invention, rendering such a cloud an unsuitable place for
cyberattacks.”
The online analysis portal can be accessed here[7]. The full documentation
for Project Freta is available
here[8].
References
- ^
Project Freta
(www.microsoft.com) - ^
kernel rootkits
(docs.microsoft.com) - ^
process hiding
(www.jstage.jst.go.jp) - ^
Freta Street
(en.wikipedia.org) - ^
X-ray medical imaging
(spectrum.ieee.org) - ^
an API
(docs.microsoft.com) - ^
accessed here
(freta.azurewebsites.net) - ^
available here
(docs.microsoft.com)
Read more http://feedproxy.google.com/~r/TheHackersNews/~3/Mu29H_trkvw/microsoft-linux-forensics-rootkit.html